Question: Question 1 (1 point) A(n) targets a vulnerability. O A) threat O B) protocol C) hoax O D) risk Save Question 2 (1 point) is
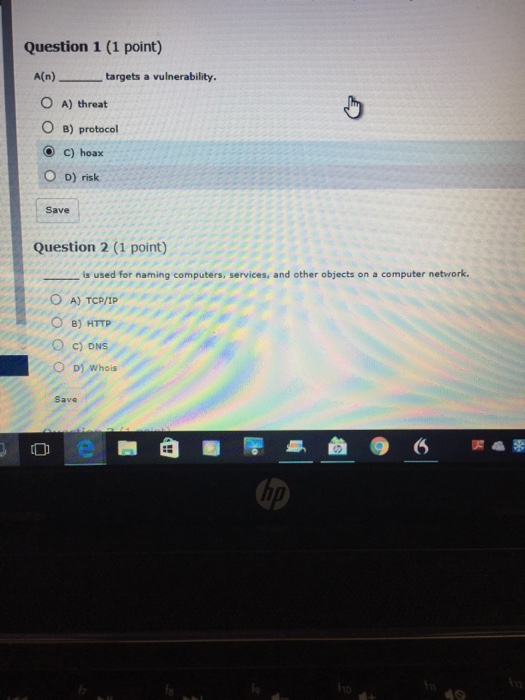
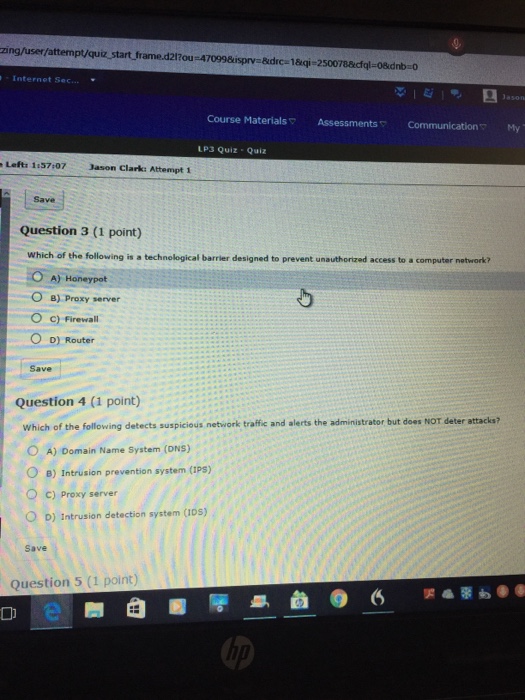
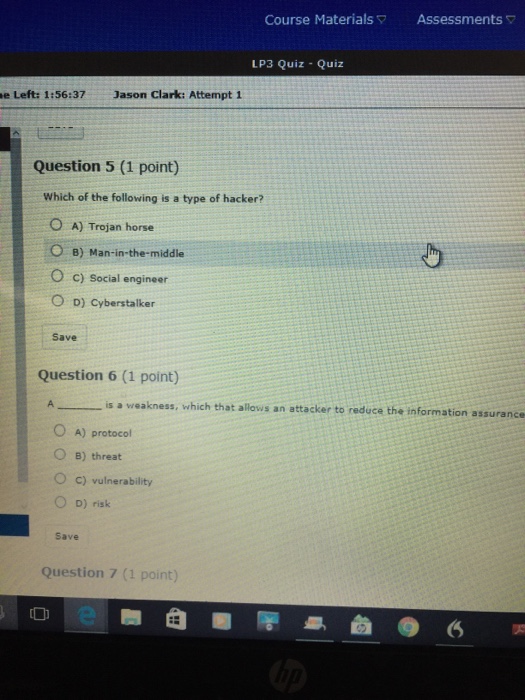
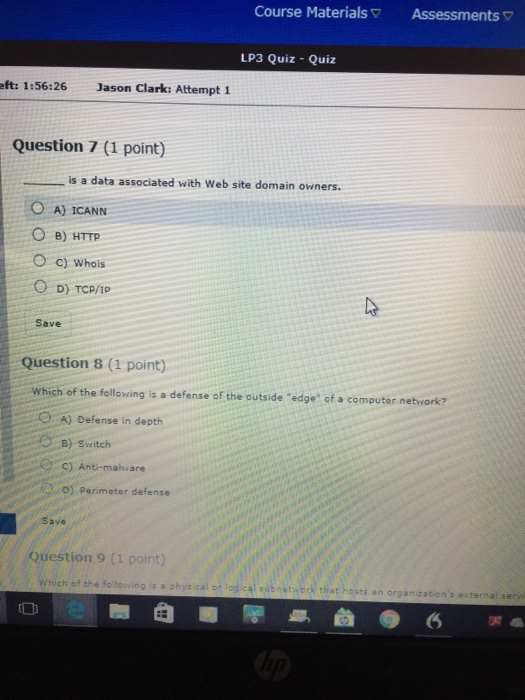
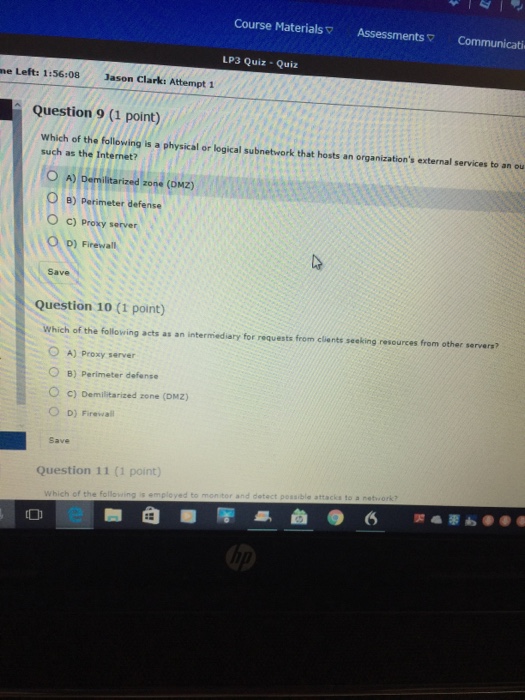
Question 1 (1 point) A(n) targets a vulnerability. O A) threat O B) protocol C) hoax O D) risk Save Question 2 (1 point) is used for naming computers, services, and other objects on a computer network O A) TCP/IP B) HTTP O c) DNS O D) Whois Save lip
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


