Question: Question 1 (4 points) Precaution for data security is: Actions which regularly support the measures which were implemented to protect the data Planned measures to
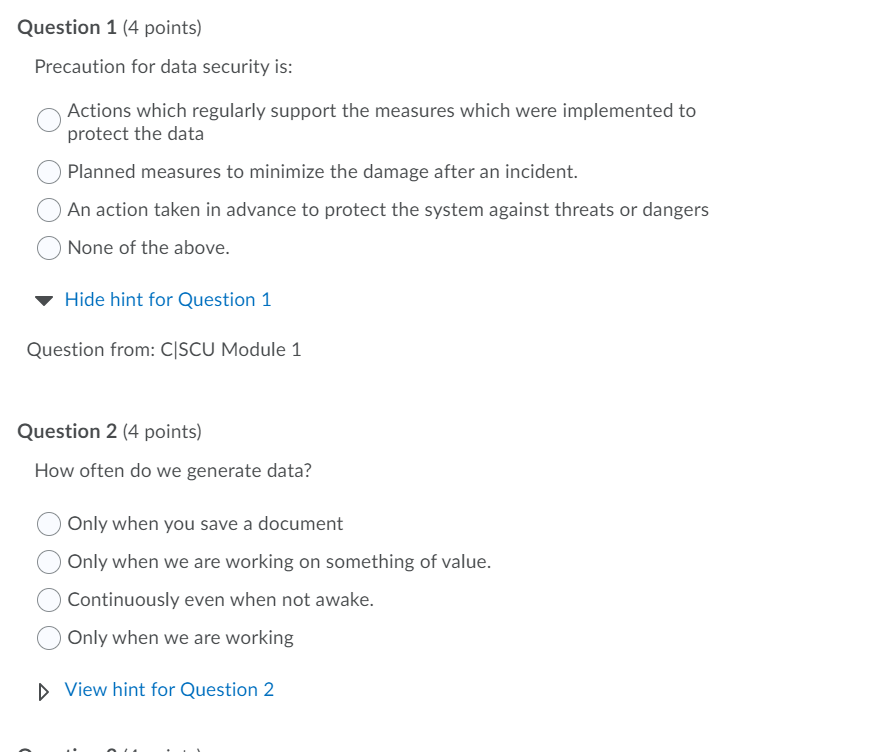
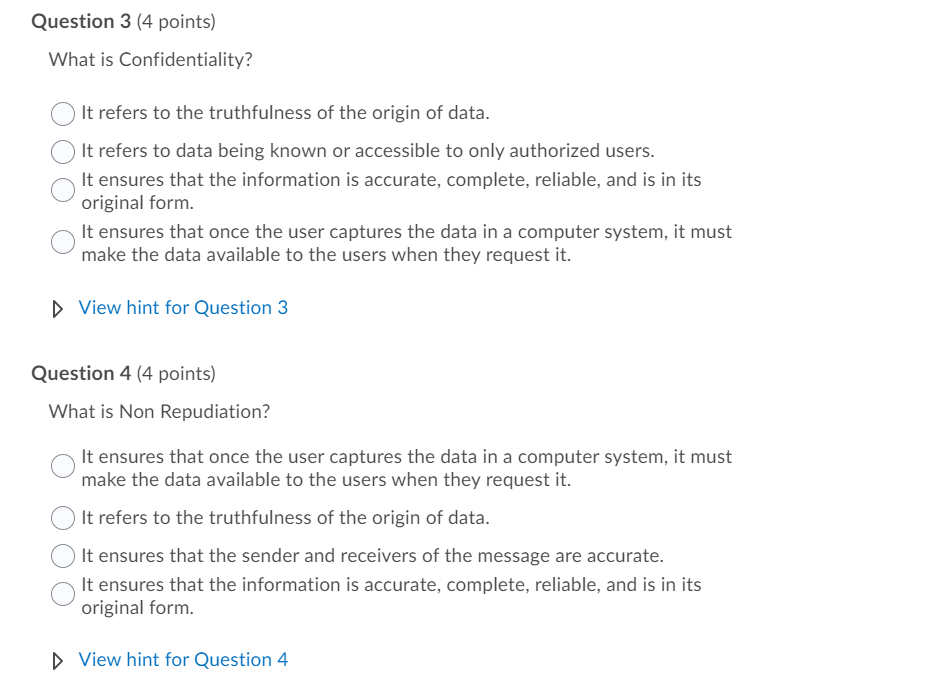
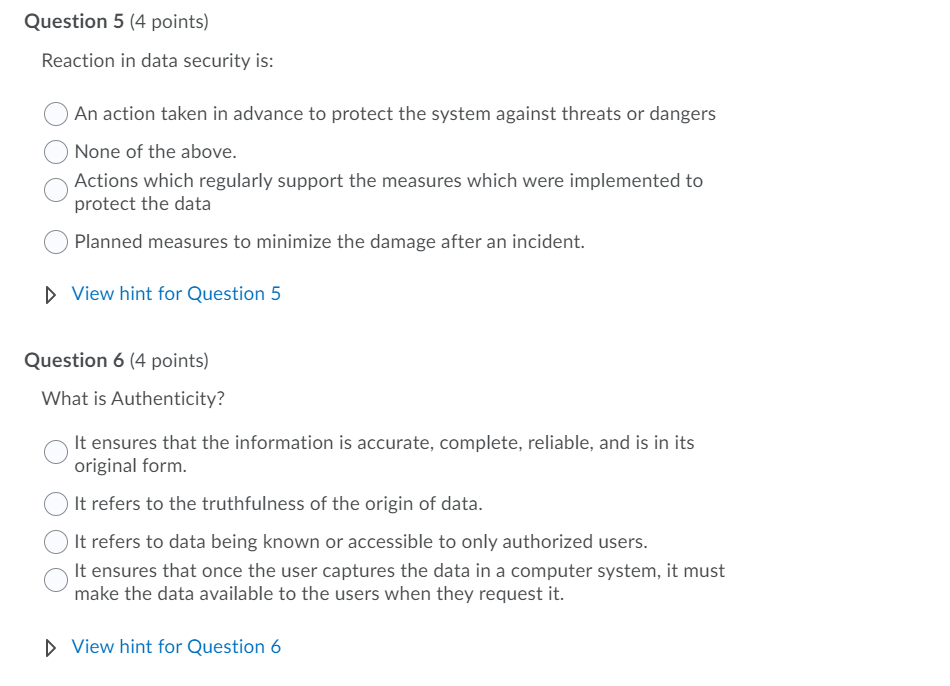
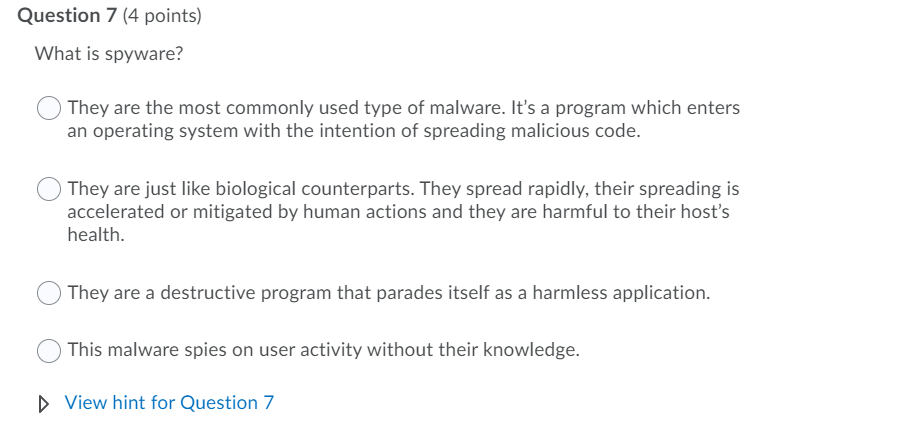
Question 1 (4 points) Precaution for data security is: Actions which regularly support the measures which were implemented to protect the data Planned measures to minimize the damage after an incident. An action taken in advance to protect the system against threats or dangers None of the above. Hide hint for Question 1 Question from: C|SCU Module 1 Question 2 (4 points) How often do we generate data? Only when you save a document Only when we are working on something of value. Continuously even when not awake. Only when we are working View hint for Question 2 Question 3 (4 points) What is Confidentiality? It refers to the truthfulness of the origin of data. It refers to data being known or accessible to only authorized users. It ensures that the information is accurate, complete, reliable, and is in its original form. It ensures that once the user captures the data in a computer system, it must make the data available to the users when they request it. View hint for Question 3 Question 4 (4 points) What is Non Repudiation? It ensures that once the user captures the data in a computer system, it must make the data available to the users when they request it. It refers to the truthfulness of the origin of data. It ensures that the sender and receivers of the message are accurate. It ensures that the information is accurate, complete, reliable, and is in its original form. View hint for Question 4 Question 5 (4 points) Reaction in data security is: An action taken in advance to protect the system against threats or dangers None of the above. Actions which regularly support the measures which were implemented to protect the data Planned measures to minimize the damage after an incident. View hint for Question 5 Question 6 (4 points) What is Authenticity? It ensures that the information is accurate, complete, reliable, and is in its original form. It refers to the truthfulness of the origin of data. It refers to data being known or accessible to only authorized users. It ensures that once the user captures the data in a computer system, it must make the data available to the users when they request it. View hint for Question 6 Question 7 (4 points) What is spyware? They are the most commonly used type of malware. It's a program which enters an operating system with the intention of spreading malicious code. They are just like biological counterparts. They spread rapidly, their spreading is accelerated or mitigated by human actions and they are harmful to their host's health. They are a destructive program that parades itself as a harmless application. This malware spies on user activity without their knowledge. View hint for Question 7 Question 8 (4 points) What is a worm? They are just like biological counterparts. They spread rapidly, their spreading is accelerated or mitigated by human actions and they are harmful to their host's health. They are a destructive program that parades itself as a harmless application. They are the most commonly used type of malware. It's a program which enters an operating system with the intention of spreading malicious code. This malware spies on user activity without their knowledge. View hint for Question 8 Question 9 (4 points) Malware is: Weaknesses is software that must be fixed. A general term used to refer to a variety of hostile or intrusive software Poor software sold by commercial companies. Hardware that has vulnerabilities. View hint for Question 9 Question 10 (4 points) Which of the following antivirus software functions isolate files suspected of being infected with malware after detection? Delete Quarantine Ignore Retry View hint for Question 10 Question 11 (4 points) Your Windows Defender detects a run time virus, what should I do? Forward it as an attachment to IT. Repair, delete, or quarantine the file. Ignore it. Save it on a USB drive for later investigation. View hint for Question 11 Question 11 (4 points) Your Windows Defender detects a run time virus, what should I do? Forward it as an attachment to IT. Repair, delete, or quarantine the file. Ignore it. Save it on a USB drive for later investigation. View hint for Question 11 Question 12 (4 points) What is an antivirus? It blocks bulk commercial email. It prevents unwanted network scans. It's 100% foolproof method to protect your device. It is a software application that detects and eradicates malware from a computer system. View hint for Question 12 Page 1: 1 2 3 5 Question 14 (6 points) How does a worm and Trojan horse differ? Trojan horses disrupt normal operations by flooding the network with traffic. Worms generally attack the user's data, encrypting them for ransom. Worms generally hide themselves as a useful/harmless application. Trojan horses are commonly hide themselves as useful/harmless applications. View hint for Question 14 7 a 10 11 12 13 14 15 16 17 18 Question 15 (6 points) You accidentally open an executable attached to an email from an unknown source. Nothing seems to be wrong or happening, what should I do next? Forward the email to the IT administrators. Open and run an antivirus program on full scan. Do nothing it should be fine. Delete the email and reboot the PC. View hint for Question 15 19 20 Question 16 (6 points) Which of the following is true about personal data? Personal data cannot harm your work environment. It is information owned by an organization. Personal data can be used to do emotional as well as financial damage. Personal data theft is less damaging than organizational data. View hint for Question 16 Question 17 (6 points) Data belonging to commercial entities, if leaked, can wreak havoc on them. Which of the following are implications of a data breach? All displayed answers are correct. Loss of productivity. Loss of intellectual property. Loss of reputation. View hint for Question 17 Question 18 (6 points) Which of the following is true about organizational data? Organizational data are often subject to intentional theft by market competitors. Personal and organizational data are always stored separately. Organizational data is always on company owned PC's and phones. Protecting data owned by commercial entities are the sole responsibility of the company. . View hint for Question 18 Question 19 (8 points) One of the last Padgett Beale campgrounds that used a telephone reservation and cash only process has decided to accept credit cards through the use of a portable credit card reader service le-g. Square) through a smart phone. What are the risks to the campground? Loss of credit card reader The loss of the phone will result in theft of customer information. Malware/Spyware may steal customer information Loss of cell phone connection View hint for Question 19 Question 20 (8 points) Padgett Beale's General Manager for Robenia's Guest House has notified staff members that a group of foreign dignitaries will be staying at the property for a nearby conference. She has asked that the names, titles, and rooms of the guests be protected for operational security reasons. Which information security function should PBI's IT department focus on? Integrity Availability. Confidentiality Continuity View hint for Question 20 Question 1 (4 points) Precaution for data security is: Actions which regularly support the measures which were implemented to protect the data Planned measures to minimize the damage after an incident. An action taken in advance to protect the system against threats or dangers None of the above. Hide hint for Question 1 Question from: C|SCU Module 1 Question 2 (4 points) How often do we generate data? Only when you save a document Only when we are working on something of value. Continuously even when not awake. Only when we are working View hint for Question 2 Question 3 (4 points) What is Confidentiality? It refers to the truthfulness of the origin of data. It refers to data being known or accessible to only authorized users. It ensures that the information is accurate, complete, reliable, and is in its original form. It ensures that once the user captures the data in a computer system, it must make the data available to the users when they request it. View hint for Question 3 Question 4 (4 points) What is Non Repudiation? It ensures that once the user captures the data in a computer system, it must make the data available to the users when they request it. It refers to the truthfulness of the origin of data. It ensures that the sender and receivers of the message are accurate. It ensures that the information is accurate, complete, reliable, and is in its original form. View hint for Question 4 Question 5 (4 points) Reaction in data security is: An action taken in advance to protect the system against threats or dangers None of the above. Actions which regularly support the measures which were implemented to protect the data Planned measures to minimize the damage after an incident. View hint for Question 5 Question 6 (4 points) What is Authenticity? It ensures that the information is accurate, complete, reliable, and is in its original form. It refers to the truthfulness of the origin of data. It refers to data being known or accessible to only authorized users. It ensures that once the user captures the data in a computer system, it must make the data available to the users when they request it. View hint for Question 6 Question 7 (4 points) What is spyware? They are the most commonly used type of malware. It's a program which enters an operating system with the intention of spreading malicious code. They are just like biological counterparts. They spread rapidly, their spreading is accelerated or mitigated by human actions and they are harmful to their host's health. They are a destructive program that parades itself as a harmless application. This malware spies on user activity without their knowledge. View hint for Question 7 Question 8 (4 points) What is a worm? They are just like biological counterparts. They spread rapidly, their spreading is accelerated or mitigated by human actions and they are harmful to their host's health. They are a destructive program that parades itself as a harmless application. They are the most commonly used type of malware. It's a program which enters an operating system with the intention of spreading malicious code. This malware spies on user activity without their knowledge. View hint for Question 8 Question 9 (4 points) Malware is: Weaknesses is software that must be fixed. A general term used to refer to a variety of hostile or intrusive software Poor software sold by commercial companies. Hardware that has vulnerabilities. View hint for Question 9 Question 10 (4 points) Which of the following antivirus software functions isolate files suspected of being infected with malware after detection? Delete Quarantine Ignore Retry View hint for Question 10 Question 11 (4 points) Your Windows Defender detects a run time virus, what should I do? Forward it as an attachment to IT. Repair, delete, or quarantine the file. Ignore it. Save it on a USB drive for later investigation. View hint for Question 11 Question 11 (4 points) Your Windows Defender detects a run time virus, what should I do? Forward it as an attachment to IT. Repair, delete, or quarantine the file. Ignore it. Save it on a USB drive for later investigation. View hint for Question 11 Question 12 (4 points) What is an antivirus? It blocks bulk commercial email. It prevents unwanted network scans. It's 100% foolproof method to protect your device. It is a software application that detects and eradicates malware from a computer system. View hint for Question 12 Page 1: 1 2 3 5 Question 14 (6 points) How does a worm and Trojan horse differ? Trojan horses disrupt normal operations by flooding the network with traffic. Worms generally attack the user's data, encrypting them for ransom. Worms generally hide themselves as a useful/harmless application. Trojan horses are commonly hide themselves as useful/harmless applications. View hint for Question 14 7 a 10 11 12 13 14 15 16 17 18 Question 15 (6 points) You accidentally open an executable attached to an email from an unknown source. Nothing seems to be wrong or happening, what should I do next? Forward the email to the IT administrators. Open and run an antivirus program on full scan. Do nothing it should be fine. Delete the email and reboot the PC. View hint for Question 15 19 20 Question 16 (6 points) Which of the following is true about personal data? Personal data cannot harm your work environment. It is information owned by an organization. Personal data can be used to do emotional as well as financial damage. Personal data theft is less damaging than organizational data. View hint for Question 16 Question 17 (6 points) Data belonging to commercial entities, if leaked, can wreak havoc on them. Which of the following are implications of a data breach? All displayed answers are correct. Loss of productivity. Loss of intellectual property. Loss of reputation. View hint for Question 17 Question 18 (6 points) Which of the following is true about organizational data? Organizational data are often subject to intentional theft by market competitors. Personal and organizational data are always stored separately. Organizational data is always on company owned PC's and phones. Protecting data owned by commercial entities are the sole responsibility of the company. . View hint for Question 18 Question 19 (8 points) One of the last Padgett Beale campgrounds that used a telephone reservation and cash only process has decided to accept credit cards through the use of a portable credit card reader service le-g. Square) through a smart phone. What are the risks to the campground? Loss of credit card reader The loss of the phone will result in theft of customer information. Malware/Spyware may steal customer information Loss of cell phone connection View hint for Question 19 Question 20 (8 points) Padgett Beale's General Manager for Robenia's Guest House has notified staff members that a group of foreign dignitaries will be staying at the property for a nearby conference. She has asked that the names, titles, and rooms of the guests be protected for operational security reasons. Which information security function should PBI's IT department focus on? Integrity Availability. Confidentiality Continuity View hint for Question 20













