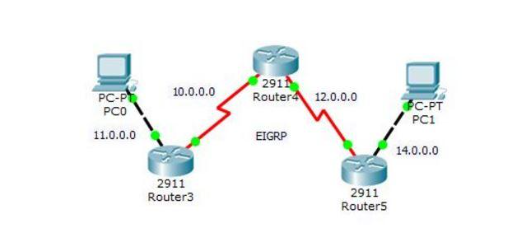
Question: Question 1 : Based on given project, without using packet tracer, what is the 4 main steps to configure VLANs for network as shown below.
Question: Based on given project, without using packet tracer, what is the main steps to
configure VLANs for network as shown below.
Give the configuration in one line with description of each steps
Question: In what ways can a hash value be secured so as to provide message
authentication?
Explain the difference between a message authentication code and a oneway hash function? with
an example for each and how it works
Question: Differentiate of characteristics between Symmetric Encryption Algorithms and Asymmetric Encryption Algorithms In your answer should mentioned the type and length of keys Provide Example of algorithms for Symmetric and Asymmetric
Encryption Algorithms
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


