Question: Question 1: List five types of authentication vulnerabilities that apply to tokens. A Unix directory listing indicates rw- r-- r-- for a file. Briefly explain
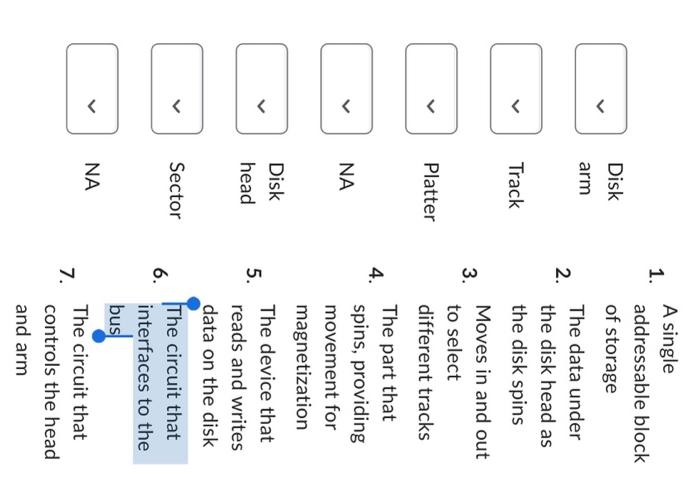
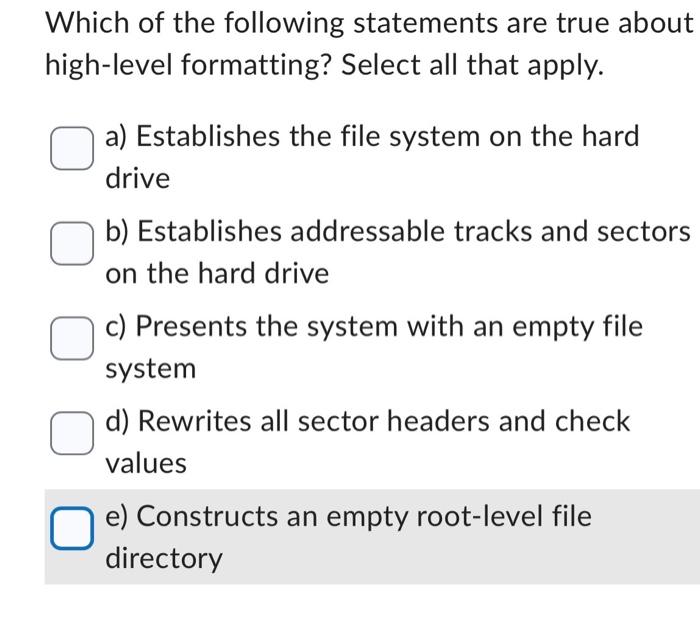
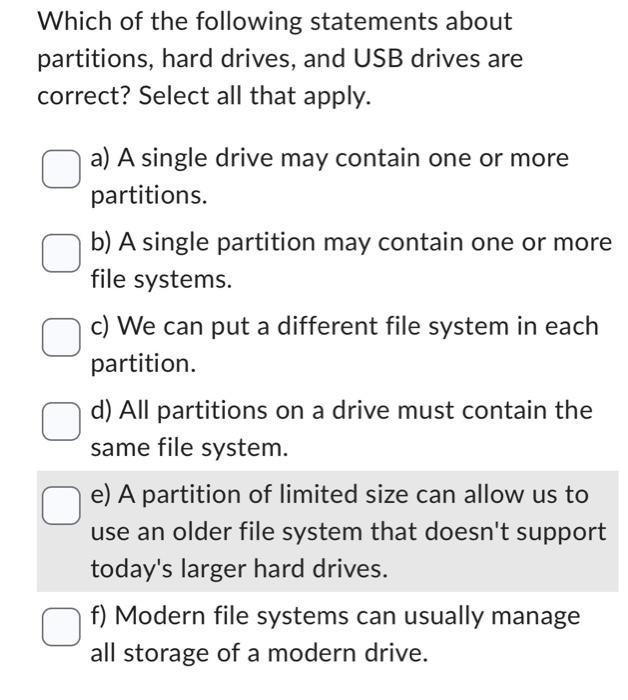
1. A single addressable block Disk of storage arm 2. The data under the disk head as Track the disk spins 3. Moves in and out to select Platter different tracks 4. The part that NA spins, providing movement for magnetization Disk head 5. The device that reads and writes data on the disk Sector 6. The circuit that interfaces to the bus 7. The circuit that controls the head and arm Which of the following statements are true about high-level formatting? Select all that apply. a) Establishes the file system on the hard drive b) Establishes addressable tracks and sectors on the hard drive c) Presents the system with an empty file system d) Rewrites all sector headers and check values e) Constructs an empty root-level file directory Which of the following statements about partitions, hard drives, and USB drives are correct? Select all that apply. a) A single drive may contain one or more partitions. b) A single partition may contain one or more file systems. c) We can put a different file system in each partition. d) All partitions on a drive must contain the same file system. e) A partition of limited size can allow us to use an older file system that doesn't support today's larger hard drives. f) Modern file systems can usually manage all storage of a modern drive
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


