Question: Question: 1) Please select all the valid statements about Public-Key Cryptography: a. Public-key encryption is more secure than secret-key encryption. b. Public-key encryption is asymmetric
Question:
1) Please select all the valid statements about Public-Key Cryptography:
a. Public-key encryption is more secure than secret-key encryption.
b. Public-key encryption is asymmetric encryption.
c. Public-key encryption is more efficient than secret-key encryption.
d. Distributing public keys is trivial.
2) Please select all the valid statements about the uses of public-key cryptosystems:
a. To provide authentication and digital signature, a receiver's public key is used to encrypt a message.
b. To provide authentication and digital signature, a sender's private key is used to encrypt a message.
c. To provide confidentiality, a sender's private key is used to encrypt a message.
d. To provide confidentiality, a receiver's public key is used to encrypt a message.
3) The essential public-key cryptography requirements basically state that a suitable trap-door one-way function is needed in a practical public-key cryptographic scheme.
a. True
b. False
4)In RSA, which of the following should not be known by attackers?
Value of n
Value of (n)
Value of e
Value of p or q
Value of d
5) In RSA, when the owner the key pair derives the private key d using the extended Euclid's algorithm with ax+by=1, which of the following statements about a, b, x, and y are valid:
a. a is n
b. b is e
c. b is (n)
d. a is (n)
e. x will be the derived private key d
f. y will be the derived private key d
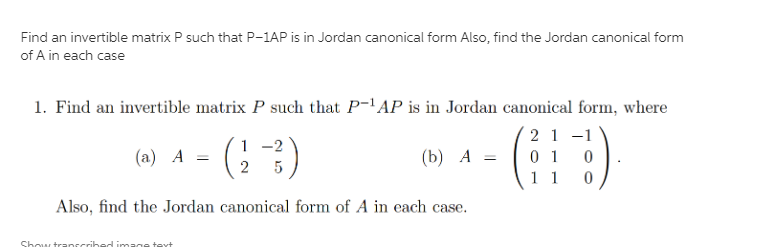
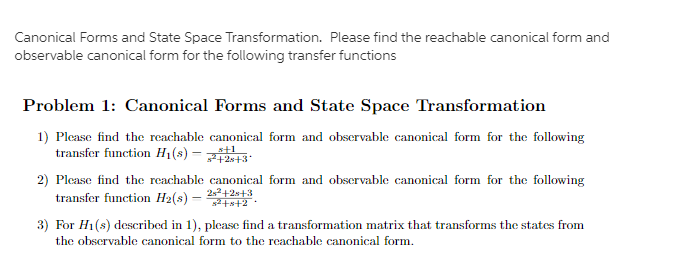
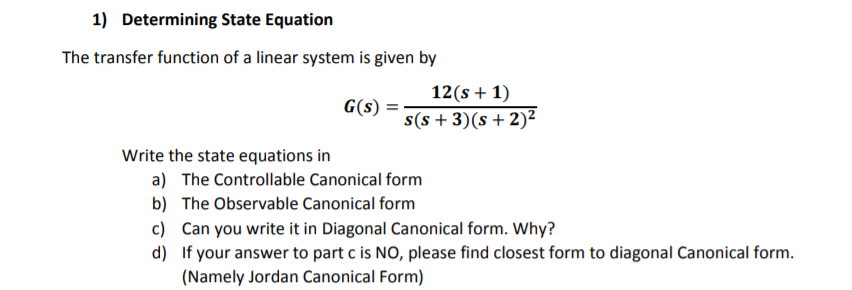
\fCanonical Forms and State Space Transformation. Please fincl the reachable canonical form and observable canonical form for the following transfer functions Problem 1: Canonical Forms and State Space Transformation 1] Please find the reachable canonical form and observable canonical form for the following transfer function Hlfsj gig 2] Please find the reachable canonical form and observable canonical form for the following transfer function Hsfs] w. 3] For H1[s} described in I], please find a transformation matrix that transforms the states from the chem-arable canonical form to the rtslchable canonical form. 1} Determining State Equation The transfer function of a linear system is given by 12(s + 1) am = 3(3 + 3x: + 2)2 Write the state equations in a] The Controllable Canonical form b) The Observable Canonical form :1 Can you write It in Diagonal Canonical form. Why? {1) If your answer to part c is NO, please find closest form to diagonal Canonical form. [Namely Jordan Canonical Form} 4 pts Question 7 If you know the values of a quantitative Y and five quantitative X's, then in an attempt to predict Y you can use if you have a linear model and if you do not. Repression Trees Logistic Regression Regression Neural Networks Exponential Smoothing Moving Averages Classification Trees Regression Trees 4nts
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


