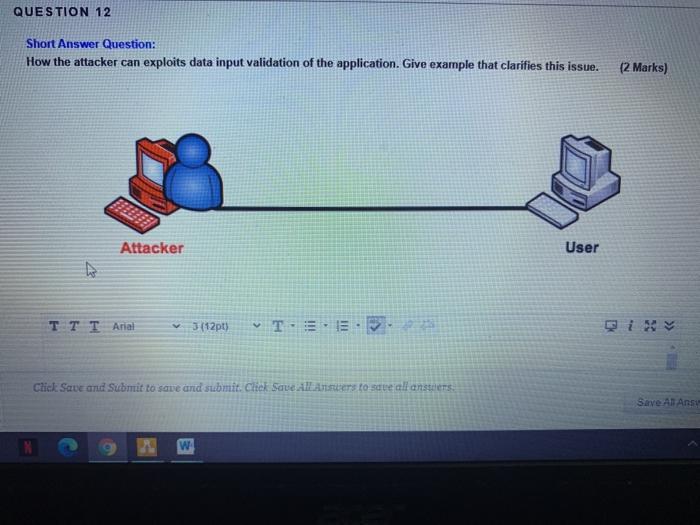
Question: QUESTION 12 Short Answer Question: How the attacker can exploits data input validation of the application. Give example that clarifies this issue. (2 Marks) Attacker
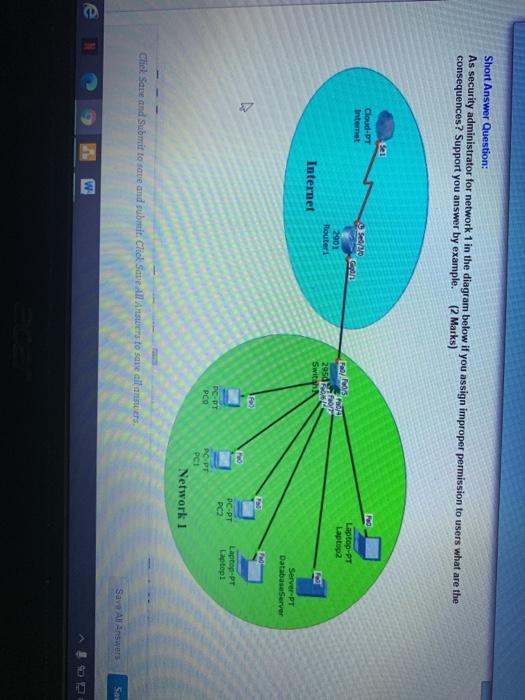
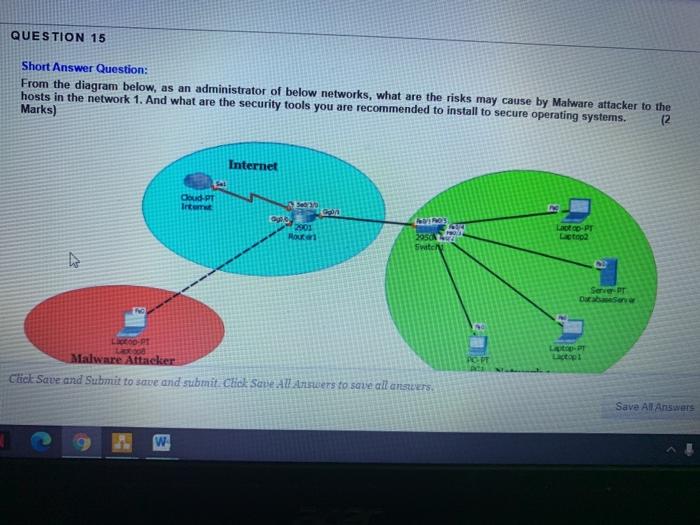
QUESTION 12 Short Answer Question: How the attacker can exploits data input validation of the application. Give example that clarifies this issue. (2 Marks) Attacker User Arial 3 (12pt) w T- Click Save and Submit to save and submit. Click Save anders to save all anstres Save An Ans Short Answer Question: As security administrator for network 1 in the diagram below if you assign improper permission to users what are the consequences? Support you answer by example. (2 Marks) HO Cloud-PT Internet Sed 20 Laptop-PT Laptop 2 2001 Routeri 2954 Internet Swit Server-PT DatabaseServer DC-PT Laptop-PT Laptop PO PC-PT PCO PC PT PC: Network 1 Chick Save and Submit to save and substit. Click Save All Answers to save all answers Save All Answers Sa 3 QUESTION 14 Short Answer Question: Map the following scenarios to their appropriate term (Auditing OR Monitoring). (2 marks). Reading in log files to find if there are any suspicious activities in a system. Viewing PC performance from windows task manager. A Auditing Using IP cameras to see if there is a physical violation to B. Monitoring a physical access control to a building. Checking if software used in a system are licensed. QUESTION 15 2P Short Antwer Question: From the diagram below, as an administrator of below networks, what are the risks may cause by Malware attacker to the hosts in the network 1. And what are the security tools you are recommended to install to secure operating systems. (2 Marks) Internet Click Save and submit to save and submit Chok Save All Answers to save all answers Save An Answer QUESTION 15 Short Answer Question: From the diagram below, as an administrator of below networks, what are the risks may cause by Malware attacker to the hosts in the network 1. And what are the security tools you are recommended to install to secure operating systems. Marks) (2 Internet Goud PT Irtem OP Route La op-PT Leto 2950 Switch Serre-P Darbono LEO.PT Malware Attacker Click Save and Submit to save and submit Click Save All Answers to save all ansuers, POT Lactal Save All Answers w
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


