Question: Question 15 2 pts CSRF attacks can be used to phish login credentials True O False Question 16 2 pts CSRF attacks may be used
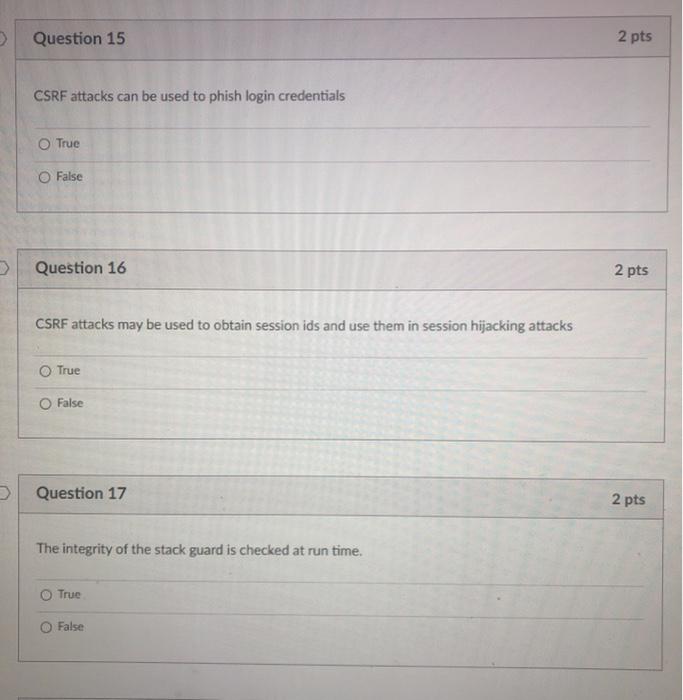
Question 15 2 pts CSRF attacks can be used to phish login credentials True O False Question 16 2 pts CSRF attacks may be used to obtain session ids and use them in session hijacking attacks True O False Question 17 2 pts The integrity of the stack guard is checked at run time, True False
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


