Question: Question 2 0/2 pts With reference to the following slide in our lecture, Which of the following two options are most easiest to do (we
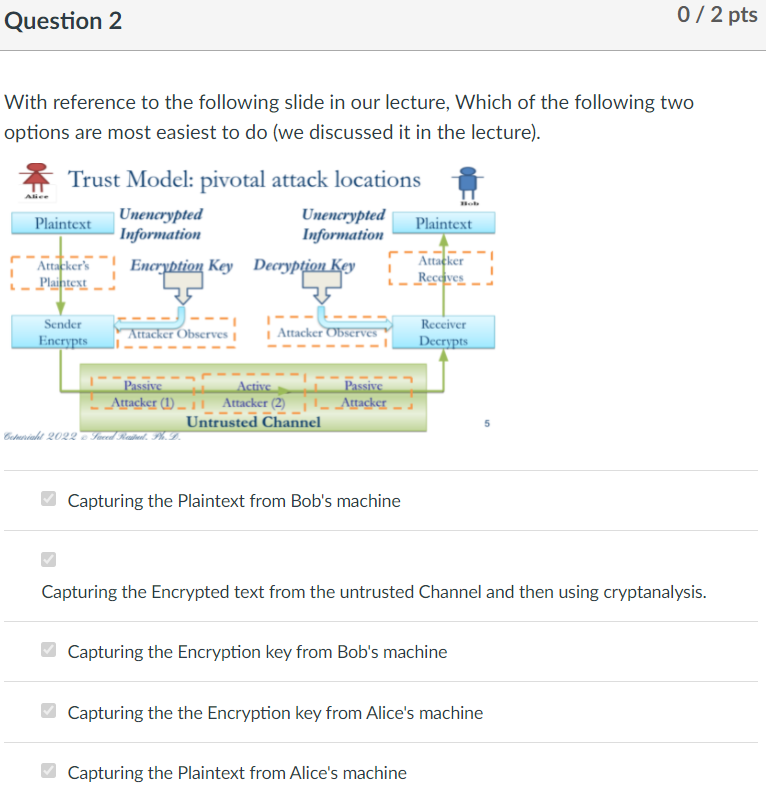
Question 2 0/2 pts With reference to the following slide in our lecture, Which of the following two options are most easiest to do (we discussed it in the lecture). Alice Trust Model: pivotal attack locations Plaintext Unencrypted Unencrypted Plaintext Information Information Attacker's Encryption Key Decryption Key Attacker Plaintext Receives Sender Encrypts - Attacker Observes Attacker Observes Receiver Decrypts Passive Attacker Passive Active Attacker (1) _ It Attacker (2) Untrusted Channel Coherwisaht 2022 Saeed Rebel. XL. Capturing the plaintext from Bob's machine Capturing the Encrypted text from the untrusted Channel and then using cryptanalysis. Capturing the Encryption key from Bob's machine Capturing the the Encryption key from Alice's machine Capturing the plaintext from Alice's machine - Question 3 0/2 pts What do we mean by Bidirectional Trust between Alice and Bob? Alice has Bob's Key Bob has Alice's Key Alice Trusts Bob's key and Bob Trusts Alice's Key Bob Trusts Alice's Key Alice has Bob's key and Bob has Alice's Key Alice Trusts Bob's Key Question 4 0/2 pts When we say that Alice Trusts Bob, what do we mean? (Check all that apply) Alice Trusts Bob's key and Bob Trusts Alice's Key Alice has Bob's Key Bob Trusts Alice's Key Alice has Bob's key and Bob has Alice's Key Alice Trusts Bob's Key Bob has Alice's Key Question 5 0/2 pts Which of the following is Incorrect statement or restatement of the Fundamental Principle of Trust: (Be careful of subtle differences) To establish trust we need to have unquestionable trust in the trust anchor. The only to establish trust over an untrusted communication medium is to exchange the secret key through an external trusted mechanism o One way to establish trust over an untrusted communication medium is to exchange the secret key through an external trusted mechanism Trust can be derived from an existing trust. Question 6 0 / 1 pts In a Web of Trust without delegation with N existing members, how many people will a new member have to establish trust with before she is trusted by the entire group? N(N-1) 1 ON(N-1)/2 Question 7 0/2 pts Which of the following is correct statement? Phil Zimmermann worked at MIT and Founders of RSA went to FAU. Phil Zimmermann proposed the Hierarchical Trust Model while the RSA company proposed Web of Trust Model. Phil Zimmermann created a secure email system and RSA founders invented a public Key Algorithm. The founders of RSA company proposed a Web of Trust model with delegation and Phil Zimmermann proposed it WITH delgation
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


