Question: Question 2 Marks: 30 (a) Consider the pipelined datapath shown in Figure Q(a)i. Describe how this datapath operates by simulating the following two instructions after
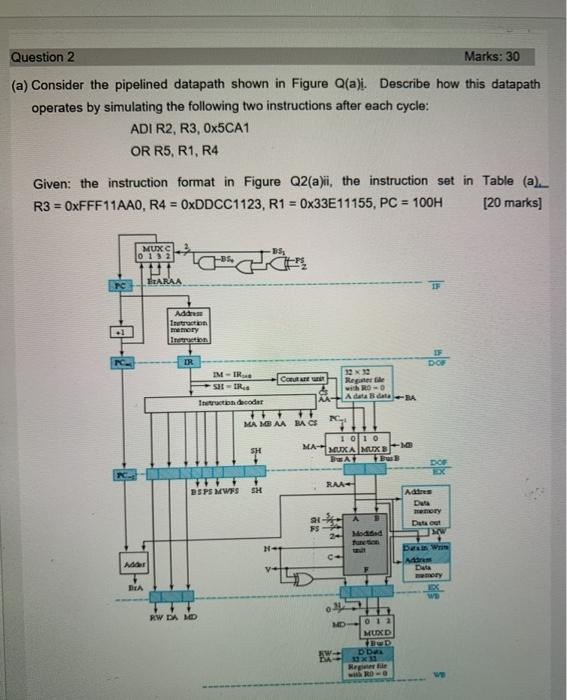
Question 2 Marks: 30 (a) Consider the pipelined datapath shown in Figure Q(a)i. Describe how this datapath operates by simulating the following two instructions after each cycle: ADI R2, R3, Ox5CA1 OR R5, R1, R4 Given: the instruction format in Figure Q2(a)ii, the instruction set in Table (a) R3 = 0xFFF11AAO, R4 = OxDDCC1123, R1 = 0x33E11155, PC = 100H [20 marks] MUX 0 1 3 2 -BS. ERARAA PC IF Add Interaction memory IR DOR IM-TR SHR Registere with ROD Ada BdBA Intion decoder NC MANGAA BACH 1 010 MA-MUXA MAX Bu T 1 SH RA DSPS MWES Adres memory A 21 FS Moded WW DEA RW DA LD O 12 HUD D D Here WIRD Question 2 Marks: 30 (a) Consider the pipelined datapath shown in Figure Q(a)i. Describe how this datapath operates by simulating the following two instructions after each cycle: ADI R2, R3, Ox5CA1 OR R5, R1, R4 Given: the instruction format in Figure Q2(a)ii, the instruction set in Table (a) R3 = 0xFFF11AAO, R4 = OxDDCC1123, R1 = 0x33E11155, PC = 100H [20 marks] MUX 0 1 3 2 -BS. ERARAA PC IF Add Interaction memory IR DOR IM-TR SHR Registere with ROD Ada BdBA Intion decoder NC MANGAA BACH 1 010 MA-MUXA MAX Bu T 1 SH RA DSPS MWES Adres memory A 21 FS Moded WW DEA RW DA LD O 12 HUD D D Here WIRD
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


