Question: Question 22 Compared to asymmetric encryption, symmetric encryption is not enough to address two key issues: and key distribution, digital signatures key distribution, farge overhead
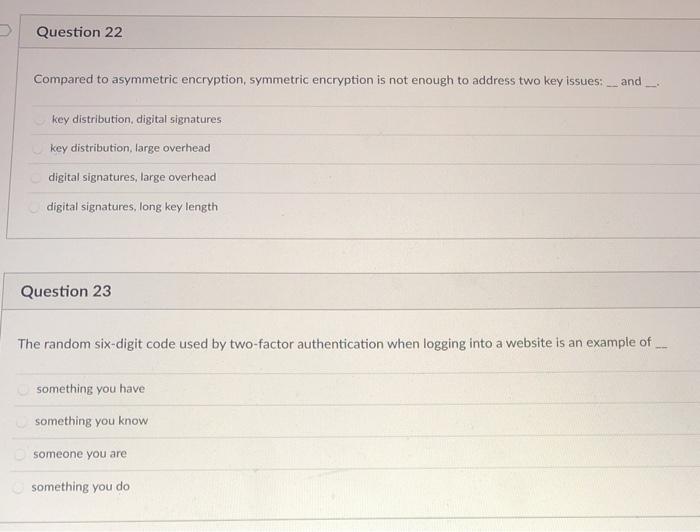
Question 22 Compared to asymmetric encryption, symmetric encryption is not enough to address two key issues: and key distribution, digital signatures key distribution, farge overhead digital signatures, large overhead digital signatures, long key length Question 23 The random six-digit code used by two-factor authentication when logging into a website is an example of something you have something you know someone you are something you do
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


