Question: Question 23 Which statement about TLS from these five is actually false? Not yet answered Select one: Marked out of 1 a. TLS uses asymmetric
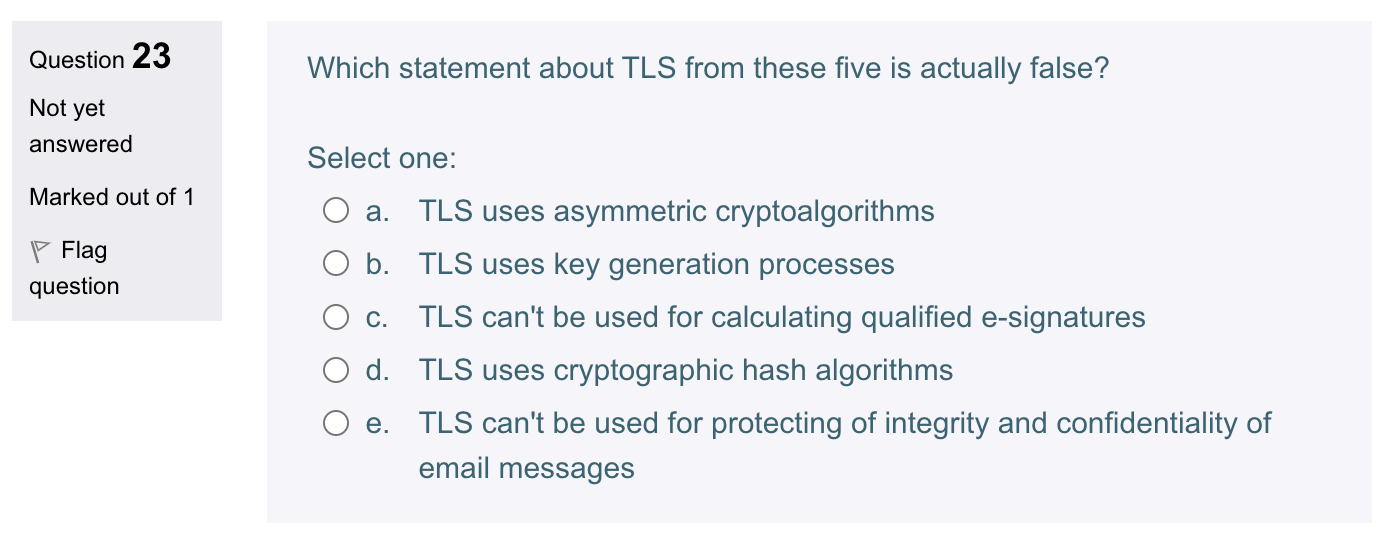
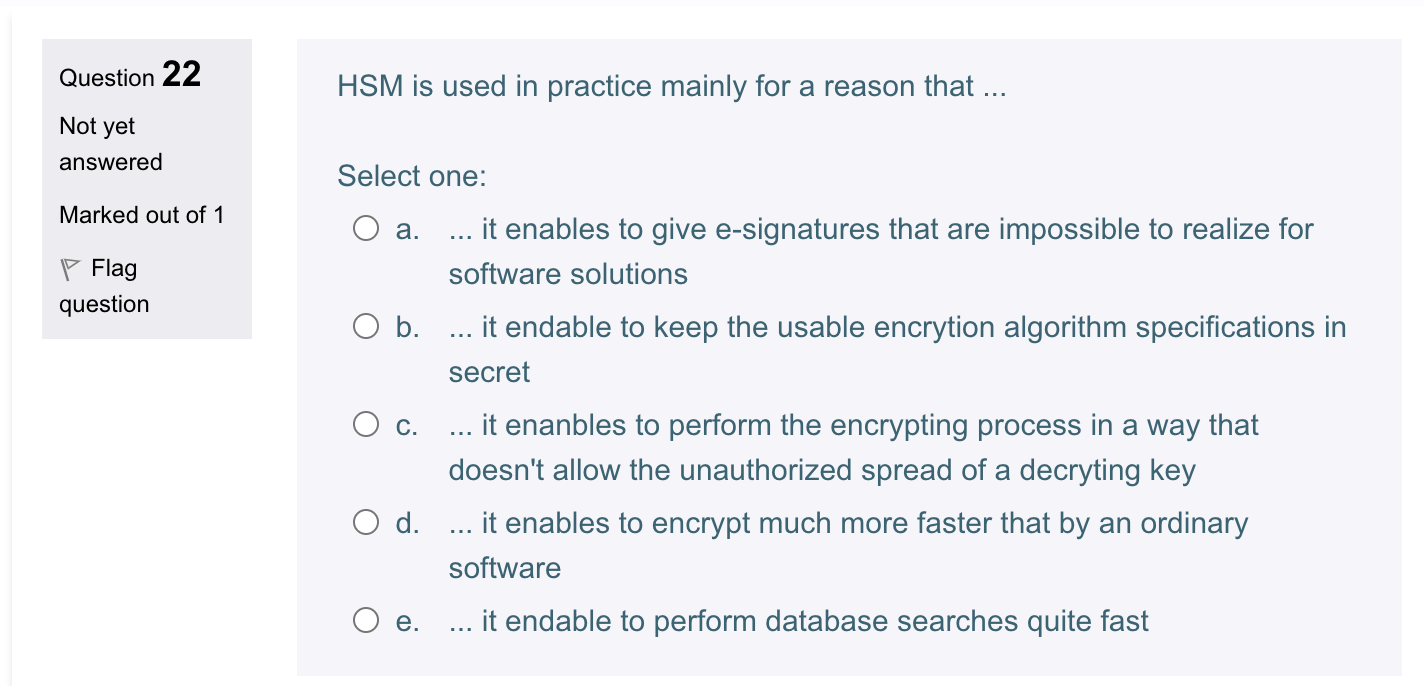
Question 23 Which statement about TLS from these five is actually false? Not yet answered Select one: Marked out of 1 a. TLS uses asymmetric cryptoalgorithms b. TLS uses key generation processes c. TLS can't be used for calculating qualified e-signatures d. TLS uses cryptographic hash algorithms e. TLS can't be used for protecting of integrity and confidentiality of email messages Question 22 HSM is used in practice mainly for a reason that ... Not yet answered Select one: Marked out of 1 a... it enables to give e-signatures that are impossible to realize for software solutions b. ... it endable to keep the usable encrytion algorithm specifications in secret c. ... it enanbles to perform the encrypting process in a way that doesn't allow the unauthorized spread of a decryting key d. ... it enables to encrypt much more faster that by an ordinary software e. ... it endable to perform database searches quite fast
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


