Question: QUESTION 25 6 points Save Answer Match each threat to the scenario that best describes it. Read them all first and then match them based
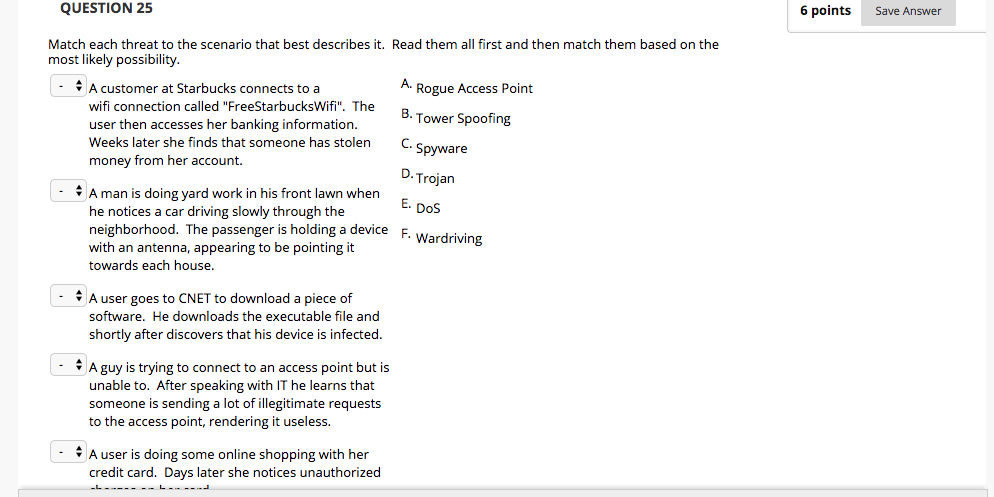
QUESTION 25 6 points Save Answer Match each threat to the scenario that best describes it. Read them all first and then match them based on the most likely possibility A customer at Starbucks connects to a A Rogue Access Point wifi connection called "FreeStarbucksWifi". The B user then accesses her banking information Weeks later she finds that someone has stolenC. money from her account. Tower Spoofin Spyware D.Trojan A man is doing yard work in his front lawn when he notices a car driving slowly through the neighborhood. The passenger is holding a device with an antenna, appearing to be pointing it towards each house F Wardriving A user goes to CNET to download a piece of software. He downloads the executable file and shortly after discovers that his device is infected A guy is trying to connect to an access point but is unable to. After speaking with IT he learns that someone is sending a lot of illegitimate requests to the access point, rendering it useless. A user is doing some online shopping with her credit card. Days later she notices unauthorized QUESTION 25 6 points Save Answer Match each threat to the scenario that best describes it. Read them all first and then match them based on the most likely possibility A customer at Starbucks connects to a A Rogue Access Point wifi connection called "FreeStarbucksWifi". The B user then accesses her banking information Weeks later she finds that someone has stolenC. money from her account. Tower Spoofin Spyware D.Trojan A man is doing yard work in his front lawn when he notices a car driving slowly through the neighborhood. The passenger is holding a device with an antenna, appearing to be pointing it towards each house F Wardriving A user goes to CNET to download a piece of software. He downloads the executable file and shortly after discovers that his device is infected A guy is trying to connect to an access point but is unable to. After speaking with IT he learns that someone is sending a lot of illegitimate requests to the access point, rendering it useless. A user is doing some online shopping with her credit card. Days later she notices unauthorized
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


