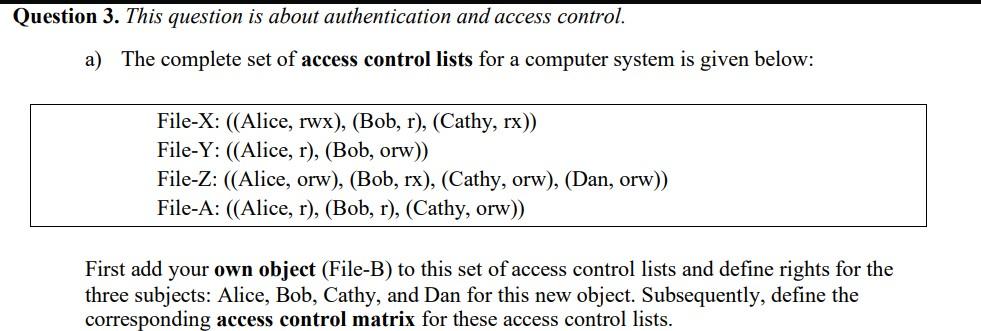
Question: . Question 3. This question is about authentication and access control. a) The complete set of access control lists for a computer system is given
 .
.
Question 3. This question is about authentication and access control. a) The complete set of access control lists for a computer system is given below: File-X: ((Alice, rwx), (Bob, r), (Cathy, rx)) File-Y: ((Alice, r), (Bob, orw)) File-Z: ((Alice, orw), (Bob, rx), (Cathy, orw), (Dan, orw)) File-A: ((Alice, r), (Bob, r), (Cathy, orw)) First add your own object (File-B) to this set of access control lists and define rights for the three subjects: Alice, Bob, Cathy, and Dan for this new object. Subsequently, define the corresponding access control matrix for these access control lists
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


