Question: QUESTION 3 To prevent XSS attacks any user supplied input should be examined and any dangerous code removed or escaped to block its execution. O
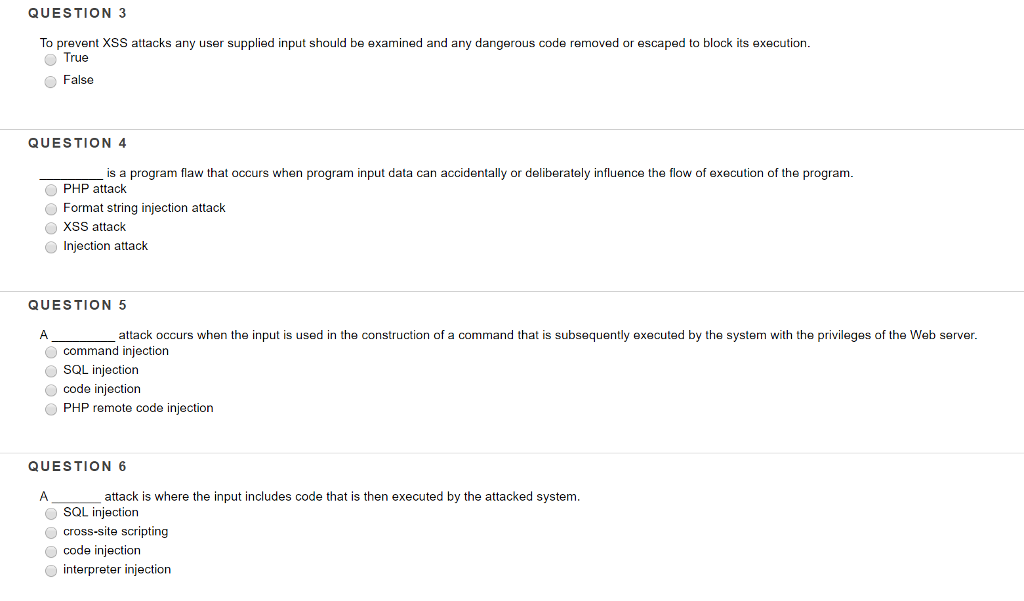
QUESTION 3 To prevent XSS attacks any user supplied input should be examined and any dangerous code removed or escaped to block its execution. O True False QUESTION 4 is a program flaw that occurs when program input data can accidentally or deliberately influence the flow of execution of the program PHP attack Format string injection attack XSS attack Injection attack QUESTION 5 attack occurs when the input is used in the construction of a command that is subsequently executed by the system with the privileges of the Web server command injection SQL injection code injection PHP remote code injection QUESTION 6 attack is where the input includes code that is then executed by the attacked systenm SQL injection cross-site scripting code injection interpreter injection
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


