Question: Question 5 (1 point) How does a distributed denial-of-service (DDoS) attack work and why are they so dangerous? Save Question 6 (1 point) G Assuming
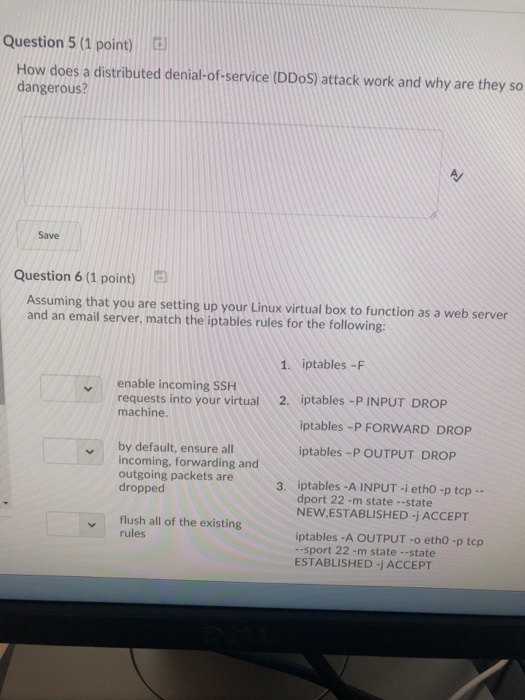
Question 5 (1 point) How does a distributed denial-of-service (DDoS) attack work and why are they so dangerous? Save Question 6 (1 point) G Assuming that you are setting up your Linux virtual box to function as a web server and an email server, match the iptables rules for the following 1. iptables-F venable incoming SSH 2. iptables-P INPUT DROP requests into your virtual machine. iptables -P FORWARD DROP by default, ensure all incoming, forwarding and outgoing packets are dropped iptables -P OUTPUT DROP iptables-A INPUT-i eth0-p tcp- dport 22 -m state --state NEW ESTABLISHED -j ACCEPT 3. flush all of the existing rules y iptables -A OUTPUT-o etho -p tcp --sport 22-m state--state ESTABLISHED -jACCEPT
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


