Question: Question 6 : Using CBC mode to create a MAC Another approach to MAC ( besides HMAC ) is to use block ciphers. One approach
Question : Using CBC mode to create a MAC
Another approach to MAC besides HMAC is to use block ciphers. One approach is to use a block cipher in CBC mode as the basis for a MAC. However, a naive approach for using CBC mode to create MACs has severe flaws.
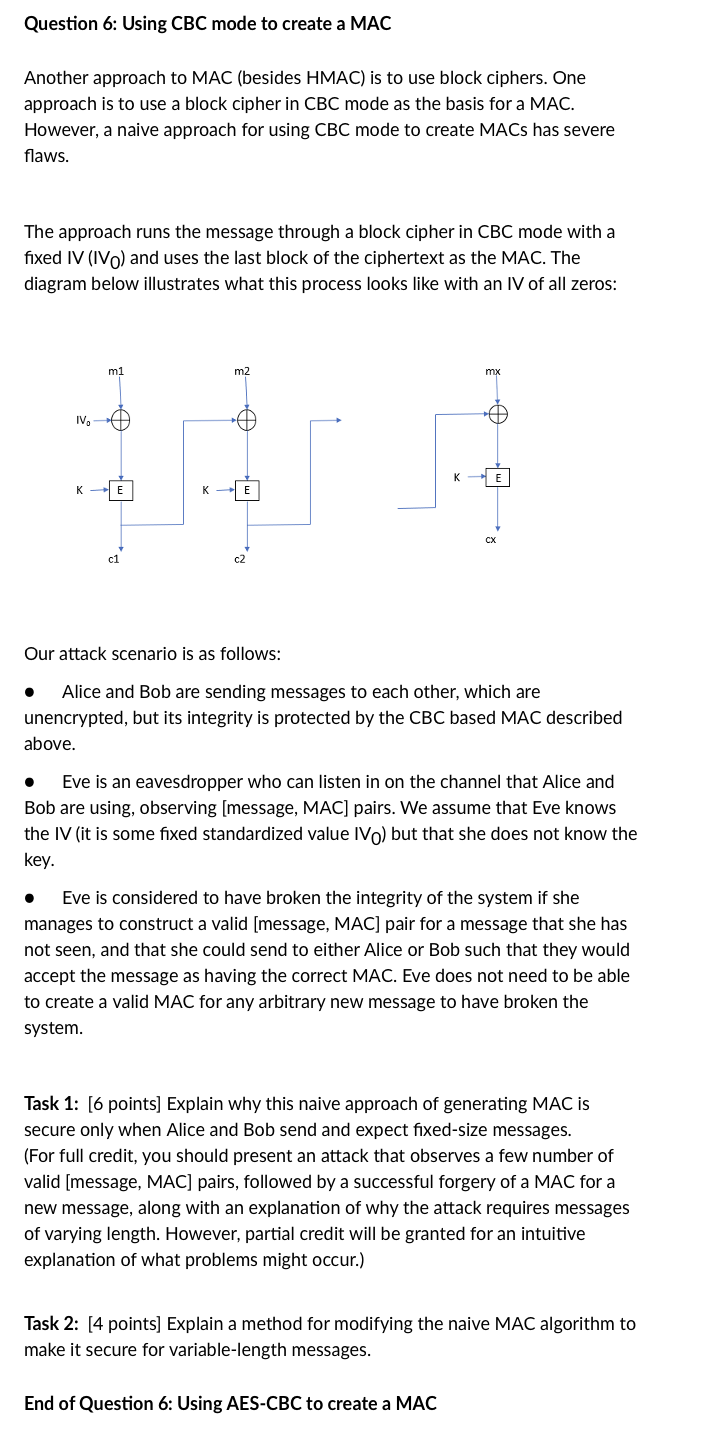
The approach runs the message through a block cipher in CBC mode with a fixed IV IV mathrmV and uses the last block of the ciphertext as the MAC. The diagram below illustrates what this process looks like with an IV of all zeros:
Our attack scenario is as follows:
Alice and Bob are sending messages to each other, which are unencrypted, but its integrity is protected by the CBC based MAC described above.
quad Eve is an eavesdropper who can listen in on the channel that Alice and Bob are using, observing message MAC pairs. We assume that Eve knows the IV it is some fixed standardized value mathrmIV but that she does not know the key.
Eve is considered to have broken the integrity of the system if she manages to construct a valid message MAC pair for a message that she has not seen, and that she could send to either Alice or Bob such that they would accept the message as having the correct MAC. Eve does not need to be able to create a valid MAC for any arbitrary new message to have broken the system.
Task : points Explain why this naive approach of generating MAC is secure only when Alice and Bob send and expect fixedsize messages. For full credit, you should present an attack that observes a few number of valid message MAC pairs, followed by a successful forgery of a MAC for a new message, along with an explanation of why the attack requires messages of varying length. However, partial credit will be granted for an intuitive explanation of what problems might occur.
Task : points Explain a method for modifying the naive MAC algorithm to make it secure for variablelength messages.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


