Question: Question 8 Symmetric cryptoalgorithms... Not yet answered Select one: Marked out of 1 a. are typically hundreds or thousands times slower than asymmetric cryptoalgorithms both
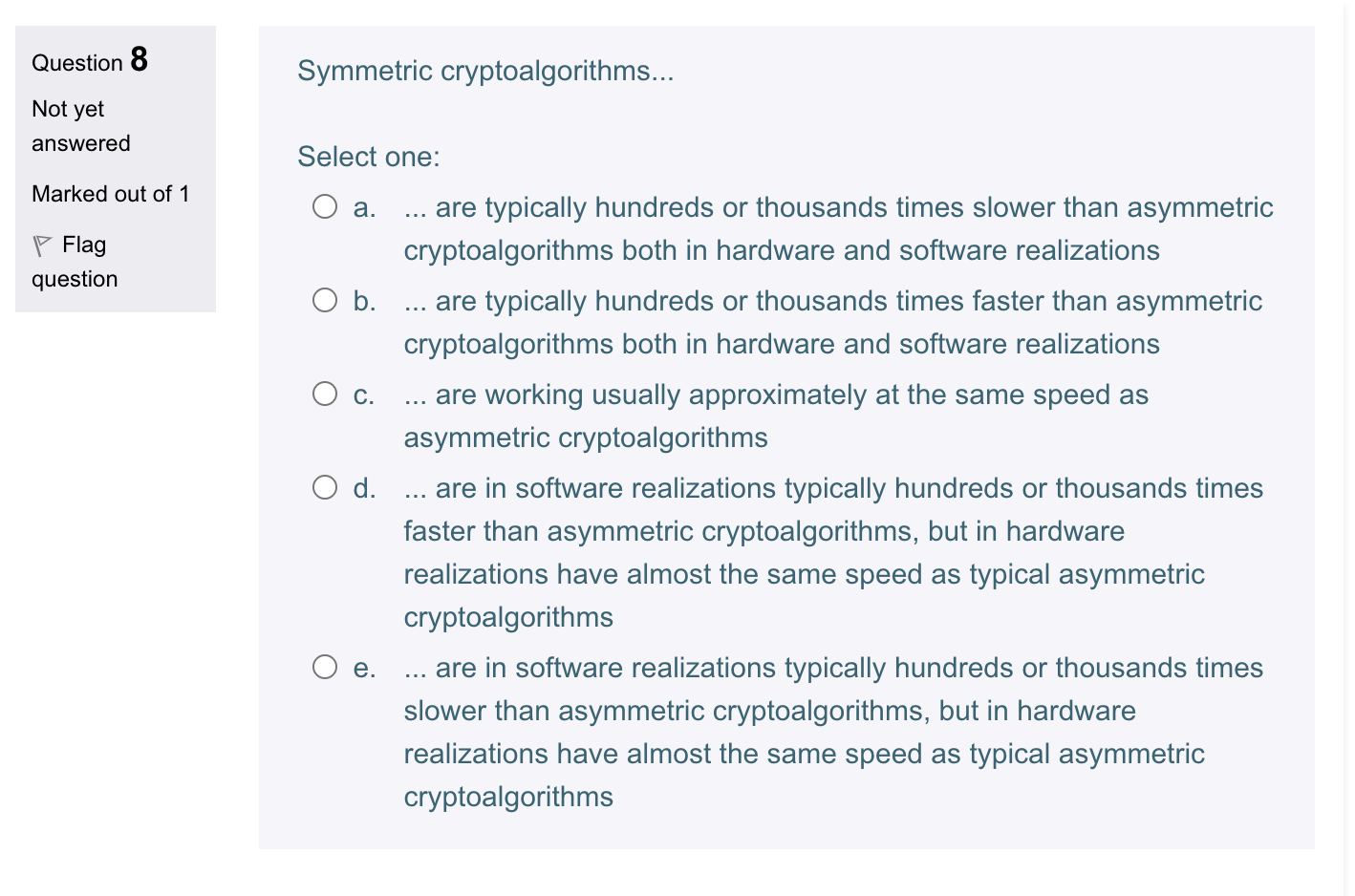
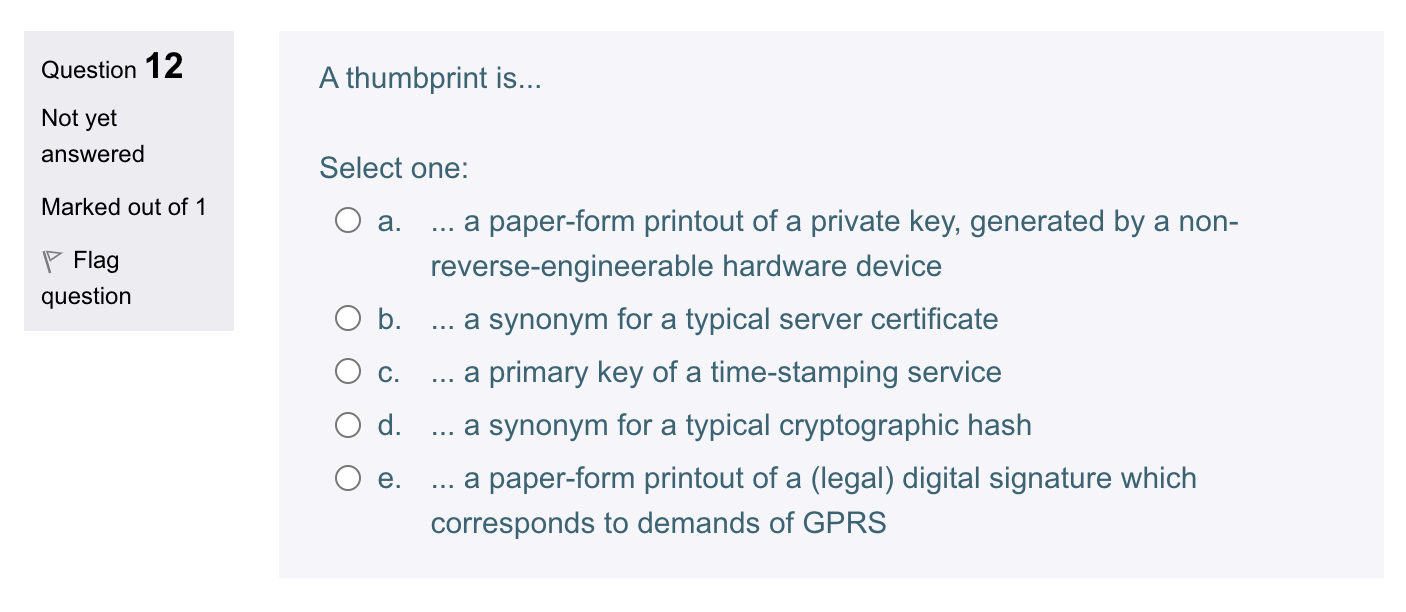
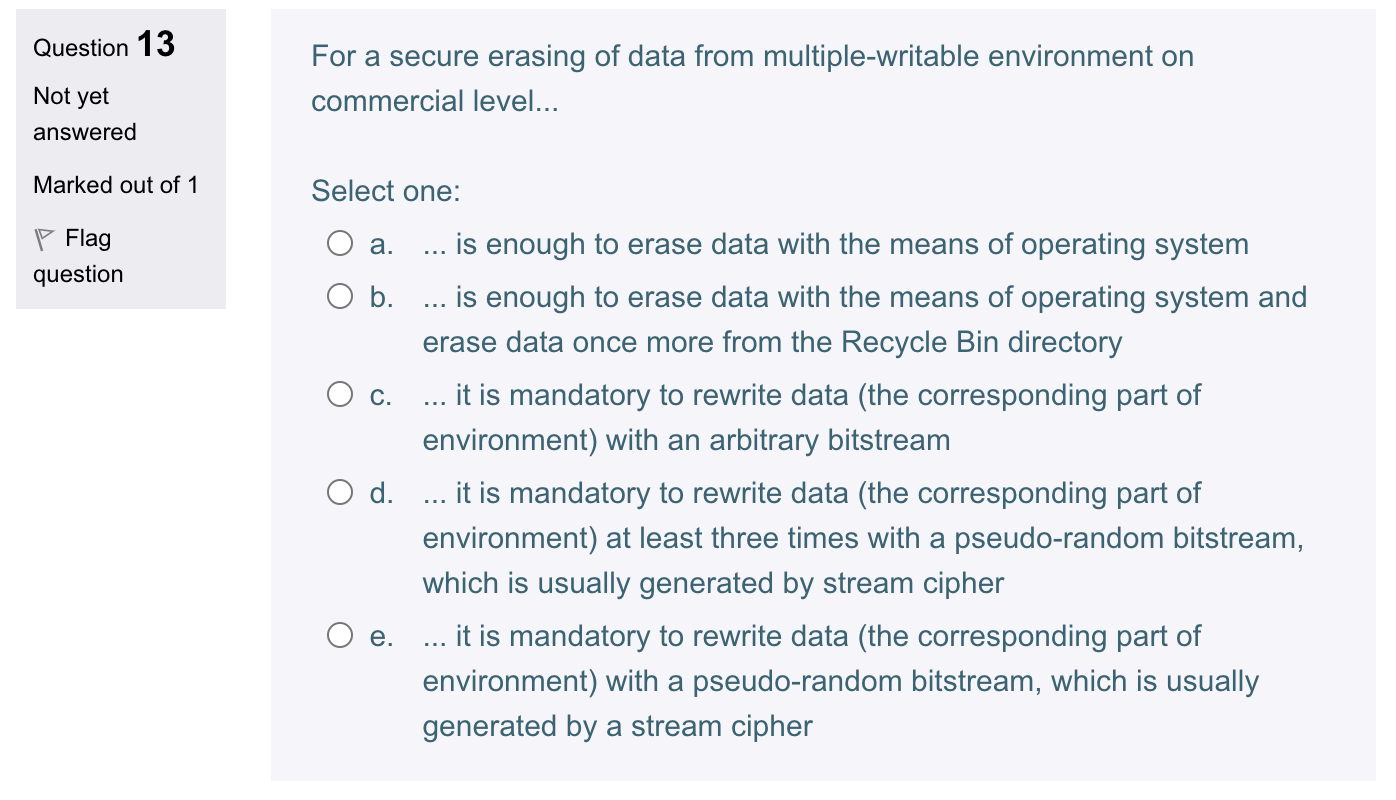
Question 8 Symmetric cryptoalgorithms... Not yet answered Select one: Marked out of 1 a. are typically hundreds or thousands times slower than asymmetric cryptoalgorithms both in hardware and software realizations b. ... are typically hundreds or thousands times faster than asymmetric cryptoalgorithms both in hardware and software realizations c. ... are working usually approximately at the same speed as asymmetric cryptoalgorithms d. ... are in software realizations typically hundreds or thousands times faster than asymmetric cryptoalgorithms, but in hardware realizations have almost the same speed as typical asymmetric cryptoalgorithms e. ... are in software realizations typically hundreds or thousands times slower than asymmetric cryptoalgorithms, but in hardware realizations have almost the same speed as typical asymmetric cryptoalgorithms Question 12 A thumbprint is... Not yet answered Select one: Marked out of 1 a. ... a paper-form printout of a private key, generated by a non- P Flag reverse-engineerable hardware device question b. ... a synonym for a typical server certificate c. a primary key of a time-stamping service d. ... a synonym for a typical cryptographic hash e. ... a paper-form printout of a (legal) digital signature which corresponds to demands of GPRS Question 13 For a secure erasing of data from multiple-writable environment on Not yet commercial level... answered Marked out of 1 Select one: a. ... is enough to erase data with the means of operating system b. ... is enough to erase data with the means of operating system and erase data once more from the Recycle Bin directory c. ... it is mandatory to rewrite data (the corresponding part of environment) with an arbitrary bitstream d. ... it is mandatory to rewrite data (the corresponding part of environment) at least three times with a pseudo-random bitstream, which is usually generated by stream cipher e... it is mandatory to rewrite data (the corresponding part of environment) with a pseudo-random bitstream, which is usually generated by a stream cipher
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


