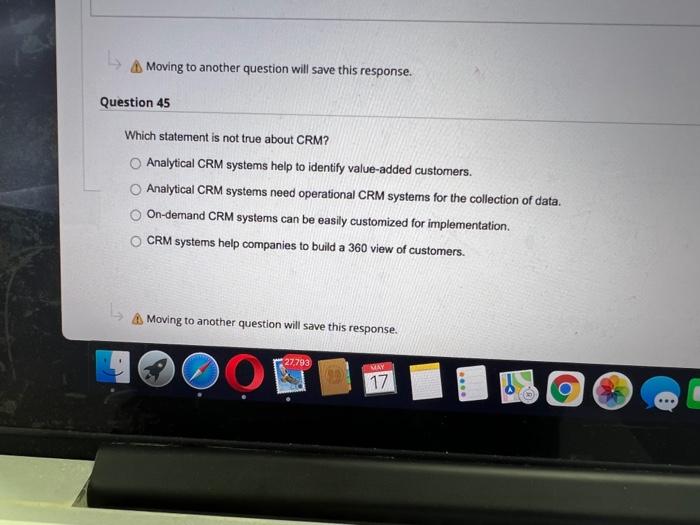
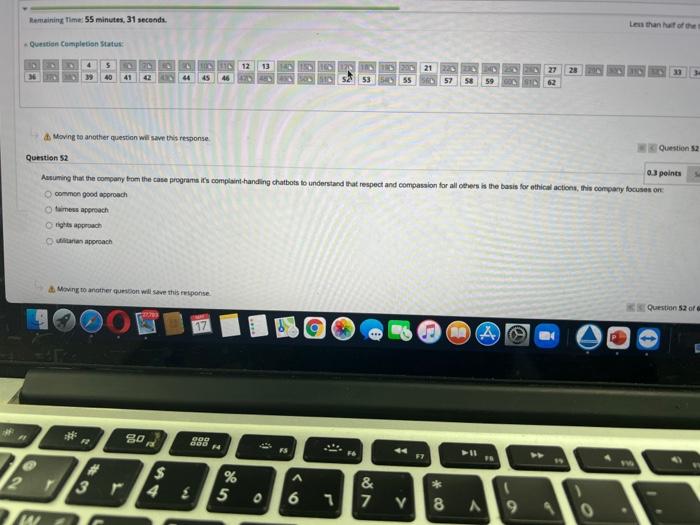
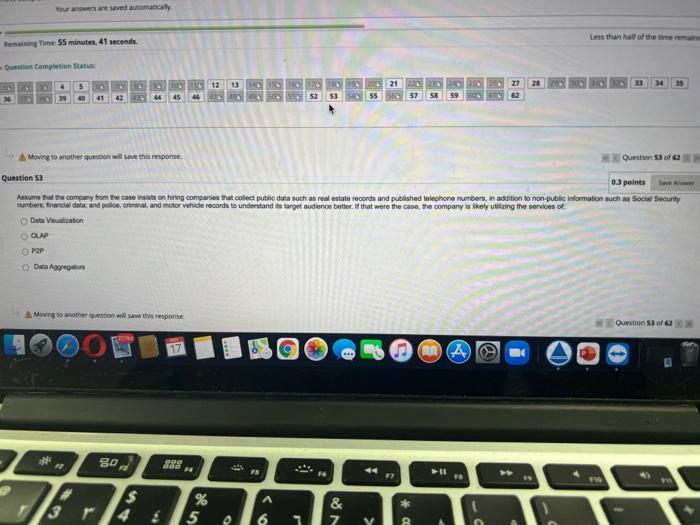
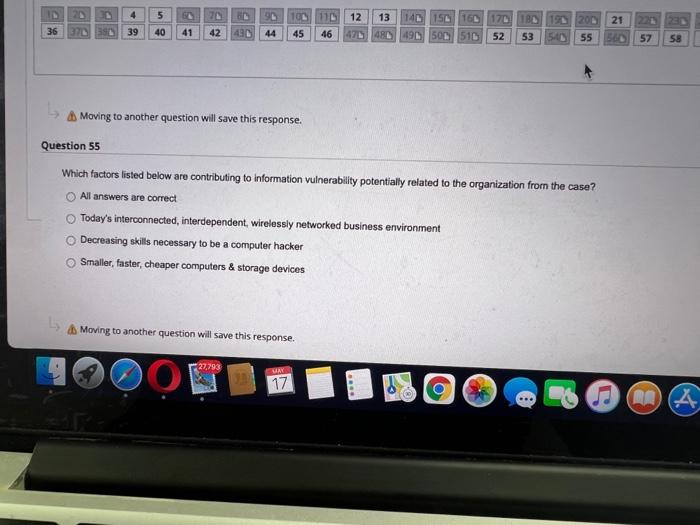
Question: Question Completion Status: 4 21 26 367 B 5 40 70 42 90 44 10110 45 46 12 13 140 150 160 170 180 190
Question Completion Status: 4 21 26 367 B 5 40 70 42 90 44 10110 45 46 12 13 140 150 160 170 180 190 200 470 480 490 SOL 516 52 53 54 55 2702 57 58 39 41 4 SED Moving to another question will save this response. Question 40 Which statement is not true? Bunding is when a business sells a group of products or services together at a higher price than their combined individual prices. Amazon's recommenders' system is an example of cross-selling. Cross-selling is the marketing of additional related products to customers based on a previous purchase. Upseiling is a strategy selling higher value products to customers. Moving to another question will save this response. 27,793 DO 17 O . 36 370 380 39 40 42 430 44 45 46 470 480 490 500 510 52 53 4 Moving to another question will save this response. Question 41 When a company implements an ERP system, these are the advantages of the vanilla approach except The implementation can be done quickly. The ERP systems can be easily upgraded. Specific business processes can be easily modified. It uses the built-in options. Moving to another question will save this response. 27,793 DAY 17 g ... 36 38 39 40 41 430 44 45 46 470 480 490 500 510 A Moving to another question will save this response. Question 42 Which of the following statements is false about supply chain management? The bullwhip effect is a problem with downstream activities. O VMI helps to reduce inventory with suppliers. JIT shifts inventory upstream. The supply chain flows downstream as well as upstream. A Moving to another question will save this response. 27,793 MAY DOI 17 O 45 46 476 480 490 500 510 52 A Moving to another question will save this response. Question 44 Which statement is false about IT outsourcing? Control and cost are two major benefits of outsourcing. SaaS and cloud computing are different names of outsourcing. Outsourcing converts fixed costs into variable costs. Outsourcing allows firms to focus on core competencies. Moving to another question will save this response. 27,793 MAY 0 17 g . Moving to another question will save this response. Question 45 Which statement is not true about CRM? Analytical CRM systems help to identify value-added customers. Analytical CRM systems need operational CRM systems for the collection of data. On-demand CRM systems can be easily customized for implementation. CRM systems help companies to build a 360 view of customers. Moving to another question will save this response. 27,793 DO MAY 17 O Remaining Time: 55 minutes, 31 seconds Len than to the Question Completion Status . DS 12 13 21 $ GB 53 27 62 Moving to another question will save this response Question 2 Question 52 3 points Asuming that the company from the case programa it's complaint handling chatbots to understand that respect and compassion for all others is the basis for ethical actions, this company focuses on common good approach fames approach is approach an approach Mening to another question will save this response Questions of CABA 80 888 FS F7 A $ A 2 % 5 * 6 & 7 7 V 8 A 9 0 w Your answers are saved automatically Less than half of the time Remaining Time 55 minutes, 41 seconds. Question Completion Status 4 5 12 13 21 221 27 20 39 41 55 57 58 59 62 Moving to another question will save this response Question 53 of 2 Question 53 0.3 points Save Assume that the company from De catena on hiring companies that collect public data such as real estate records and published telephone numbers, in addition to non public information such as Social Security numbers and data and policial, and motor vehicle records to understand its target audience better that were the case, the company is likely tizing the services of Dala Vution OLAP P2P Data Agrego Moving to another question will saw this response Questions of 62 AB SO 20 75 F6 $ A 13 r % 5 & 7 6 1 Y 8 4 5 20 3139 70 42 100 110 45 46 36 39 40 41 44 12 13 140 150 160 170 120 200 21 470 480 490 500 510 52 53 500 55 BU 230 58 57 Moving to another question will save this response. Question 55 Which factors listed below are contributing to information vulnerability potentially related to the organization from the case? All answers are correct Today's interconnected, interdependent, wirelessly networked business environment Decreasing skills necessary to be a computer hacker Smaller, faster, cheaper computers & storage devices Moving to another question will save this response. 27,798 00 17 O A Less than half of the time Ramning Time: 56 minutes, 09 seconds Question Completion Status: 4 12 13 21 28 22 62 52 55 57 Moving to ante question will save this response Question 57 of 2 Question 57 3 points Save AS During the use of the most recent city and the organization from the case realized that the attacking software had the ability to accurately perform new, unseen tisks, built on known properties famed from training or historical data that are tabeled. It is thus likely that the attack has been carried out by some sort of Expert System Neural Network Machine Leaming Robo AN A 80 $ % 5 &7 6 V 8 9 E R 70 T Y U BE 5 40 36 100 45 21 39 41 42 111 12 13 140 150 160 170 46 470 480 190 500 510 52 BL 44 53 TED 190 200 55 220 57 56 Moving to another question will save this response. Question 58 Bypassing security mechanisms within the organization mentioned in the case would be a security threat originating within: Man-made disasters Hardware threats Employees Present options do not answer this question correctly Moving to another question will save this response. 27,793 UY DOL 17 O A 21 5 27 100 45 12 13 140 150 160 170 064 490 SOLSID 52 2010 55 270 280 57 58 36 40 41 42 44 46 53 SA 59 Moving to another question will save this response. Question 59 If an unauthorized access point connected to a wireless network exist within the corporate premises of the organization from the case, it is likely a case of Evil Twin Euvesdropping Radio Frequency Jamming War Driving Moving to another question will save this response 22 DO 17 o O 6 A A 9 * F2 20 74 *** FS 76 > #3 2 $ 4 % & * s