Question: Questions 10-8 to 10-14 please. I will leave a thumbs up only if this is completed in full. Hitting the Target On December 18, 2013,
Questions 10-8 to 10-14 please. I will leave a thumbs up only if this is completed in full. 
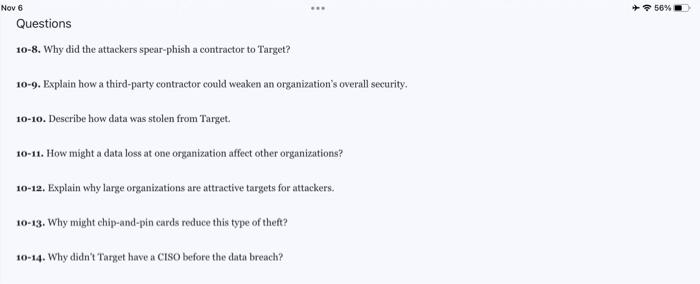
Hitting the Target On December 18, 2013, Target Corporation announced that it had lost 40 million credit and debit card numbers to attackers. Less than a month later Target announced an additional 70 million customer accounts were stolen that included names, emails, addresses, phone numbers, and so on. After accounting for some overlap between the two data losses, it turns out that about 98 million customers were affected. ,mi That's 31 percent of all 318 million people in the United States (including children and those without credit cards). This was one of the largest data breaches in U.S. history. These records were stolen from point-of-sale (POS) systems at Target retail stores during the holiday shopping season (November 27 to December 15 . 2013). If you were shopping at a Target during this time, it's likely your data was lost. Following is a short summary of how attackers got away with that much data. How Did They Do lt? The attackers first used spear-phishing to infect a Target third-party vendor named Fazio Mechanical Services (refrigeration and HVAC services). 3as Attackers placed a piece of malware called Citadel to gather keystrokes, login credentials, and screenshots from Faxio users., pas The attackers then used the stolen login credentials from Fazio to access a vendor portal (server) on Target's network. The attackers escalated privileges on that server and gained access to Target's internal network. Once in, the attackers compromised an internal Windows file server. From this server the attackers used malware named Trojan. POSRAM (a variant of BlackPOS) to extract information from POS terminals. BlackPOS was developed by a 17-year-old from St. Petersburg. Russia, and can be purchased from underground sites for about $2,000304 The customer data was continuously sent from the POS terminals to an extraction server within Target's network. It was then funneled out of Target's network to drop servers in Russia, Brazil, and Miami. From there the data was taken and sold on the black market. (See Figure 10-17.) Figure 10-17 The Damage For the attackers, the "damage" was great. It's estimated that the attackers sold about 2 million credit cards for about \$26.85 each for a total profit of $53.7M.305Not bad for a few weeks of work. Incentives for this type of criminal activity are substantial. Payoffs like these encourage even more data breaches. Target, on the other hand, incurred much greater losses than the hacker's gains. It was forced to upgrade its payment terminals to support chip-and-PIN enabled cards (to prevent cloning cards from stolen information), which cost more than \$100M. In 2015. Target lost a legal battle with banks over reimbursement of costs associated with the data breach, which could exceed $160M. It also had to pay increased insurance premiums, pay legal fees, pay for consumer credit monitoring, and pay regulatory fines. Target faced a loss of customer confidence and a drop in its revenues ( a 46 percent loss for that quarter). Analysts put the direct loss to Target as high at $450M.306 The company lost its ClO Beth Jacob and paid its CEO Gregg Steinhafel \$16M to leave 307 And in late 2015 , Target paid banks $39 million for losses related to the data breach. 3 3at The data breach affected more than just Target. The amount of media coverage related to the Target data breach likely accelerated the shift from magnetic swipe cards to EMV-compliant smart cards begun in 2015- This shift will force the eventual replacement of 800 million payment cards and 14 million POS terminals at a cost of $7B.109 The good news is that the adoption of EMV-compliant smart cards will greatly reduce the $10B in credit card fraud that occurs each year. It will also likely reduce the amount of credit card theft by hackers because stolen credit card numbers would be of little value without the physical card. Just like car accidents, data breaches may not be viewed as important until after they occur. The data breach affected Target enough that it upgraded its infrastructure, changed internal systems, and hired a Chief Information Security Officer (CISO). sho Will there be a more severe data breach in the future? Probably. Are organizations ready for it? Based on past performance, we won't be ready for it until after it happens. Figure 1017 Target Data Breach Aquila jS Demo The Damage For the attackers, the "damage" was great. It's estimated that the attackers sold about 2 million credit cards for about $26.85 each for a total profit of \$53.7M. 30s Not bad for a few weeks of work. Incentives for this type of criminal activity are substantial. Payoffs like these encourage even more data Questions 10-8. Why did the attackers spear-phish a contractor to Target? 10-9. Explain how a third-party contractor could weaken an organization's overall security, 10-10. Describe how data was stolen from Target. 10-11. How might a data loss at one organization affect other organizations? 10-12. Explain why large organizations are attractive targets for attackers. 10-13. Why might chip-and-pin cards reduce this type of theft? 10-14. Why didn't Target have a CISO before the data breach




Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


