Question: Referencing Figure A 1 in the Cloud Case pdf , indicate whether the following vulnerabilities exist at each process step in the table below... You
Referencing Figure A in the Cloud Case pdf indicate whether the following vulnerabilities exist at each process step in the table below...
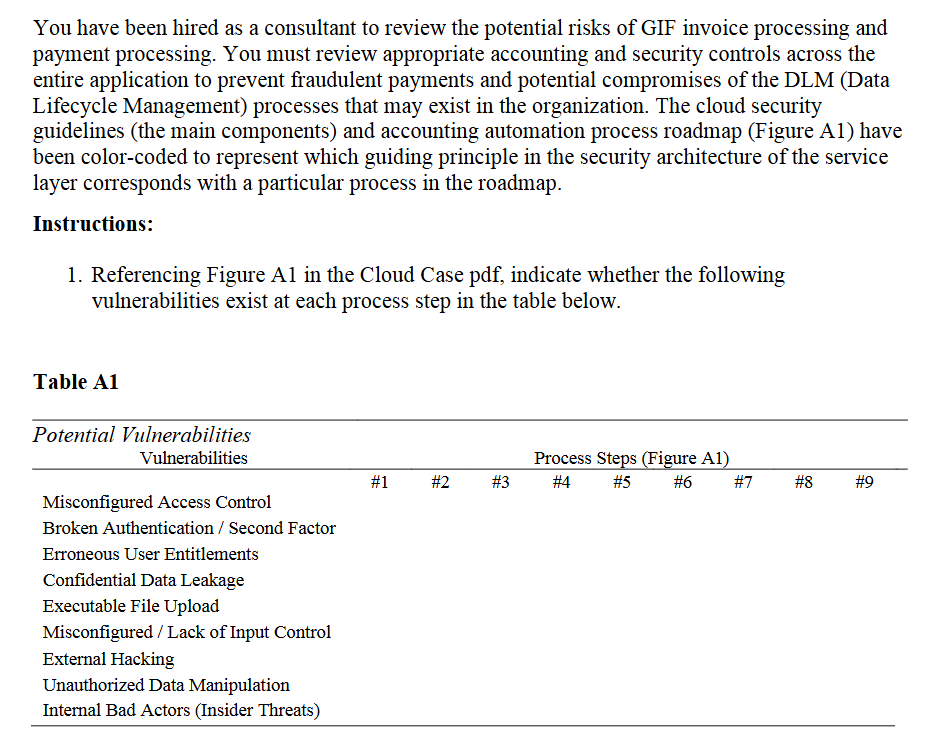
You have been hired as a consultant to review the potential risks of GIF invoice processing and payment processing. You must review appropriate accounting and security controls across the entire application to prevent fraudulent payments and potential compromises of the DLM Data Lifecycle Management processes that may exist in the organization. The cloud security guidelines the main components and accounting automation process roadmap Figure A have been colorcoded to represent which guiding principle in the security architecture of the service
layer corresponds with a particular process in the roadmap.
Figure A is included. Please fill out Table A
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


