Question: Required Operations You must implement the following encryption schemes in this assignment. Note that the following descriptions often refer to the encodable / encryptable range,
Required Operations
You must implement the following encryption schemes in this assignment. Note that the following descriptions often refer to the "encodableencryptable range," which is defined by the Cipher. WIINCHAR lowest value in the range Cipher. WAXCHAR highest value in the range and Cipher. TOTALCHARS total number of characters within the range constants within cipher java
Substitution.java
grad Expand
The Substitution Cipher is likely the most commonly known encryption algorithm. It consists of assigning each input character a unique output character, ideally one that differs from the original, and replacing all characters from the input with the output equivalent when encrypting and viceversa when decrypting
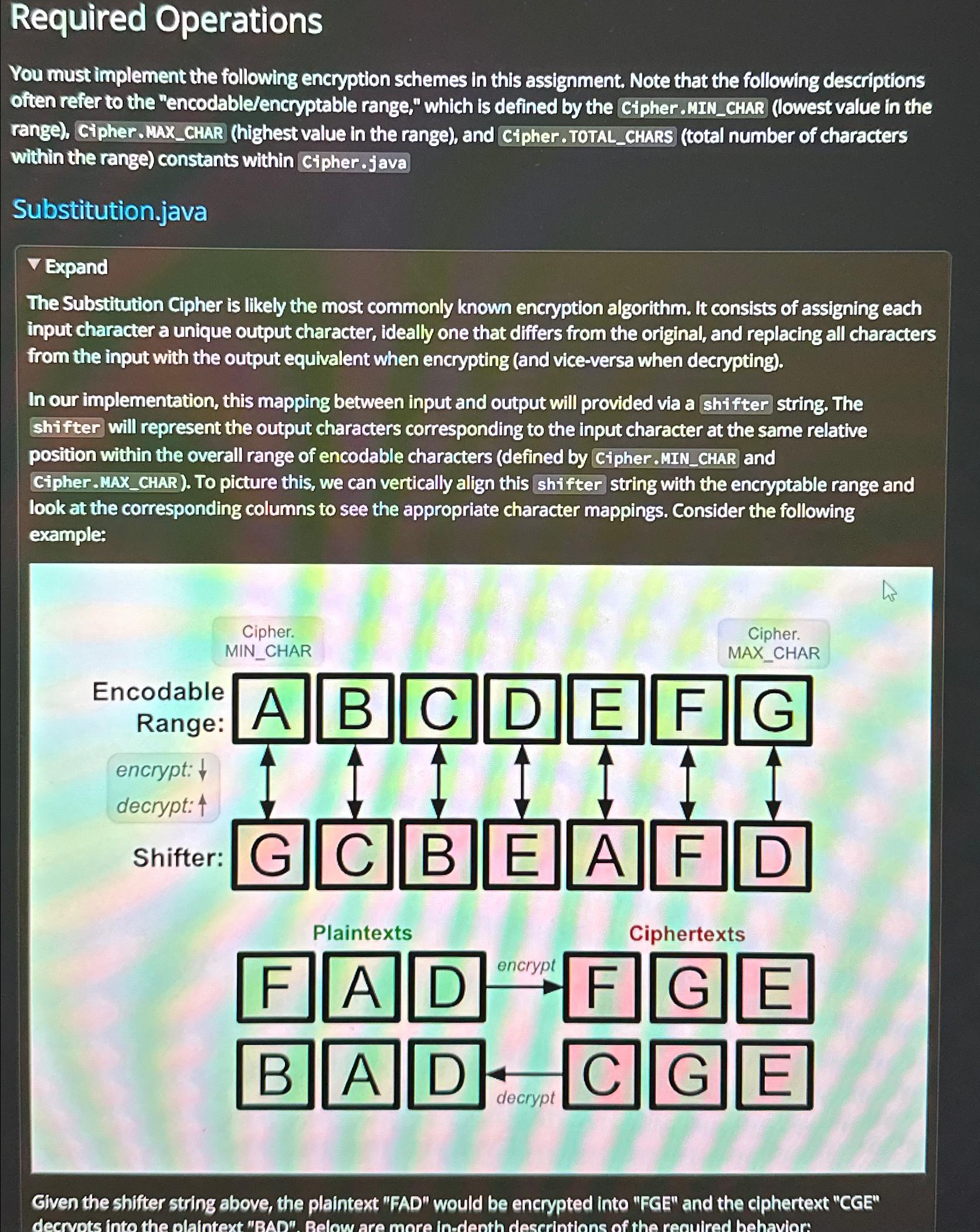
In our implementation, this mapping between input and output will provided via a shifter string. The shifter will represent the output characters corresponding to the input character at the same relative position within the overall range of encodable characters defined by Cipher.MINCHAR and Cipher.MAXCHAR To picture this, we can vertically align this shifter string with the encryptable range and look at the corresponding columns to see the appropriate character mappings. Consider the following example:
Given the shifter string above, the plaintext "FAD" would be encrypted into "FGE" and the ciphertext "CGE"
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


