Question: rningApiAssessment: 4 5 2 2 3 4 5 1 ? autoSkip = true&resume = f Over... H - E - B H - E -
rningApiAssessment:autoSkiptrue&resumef
Over...
HEB Prepaid Acco...
Synchrony
cybersecurity
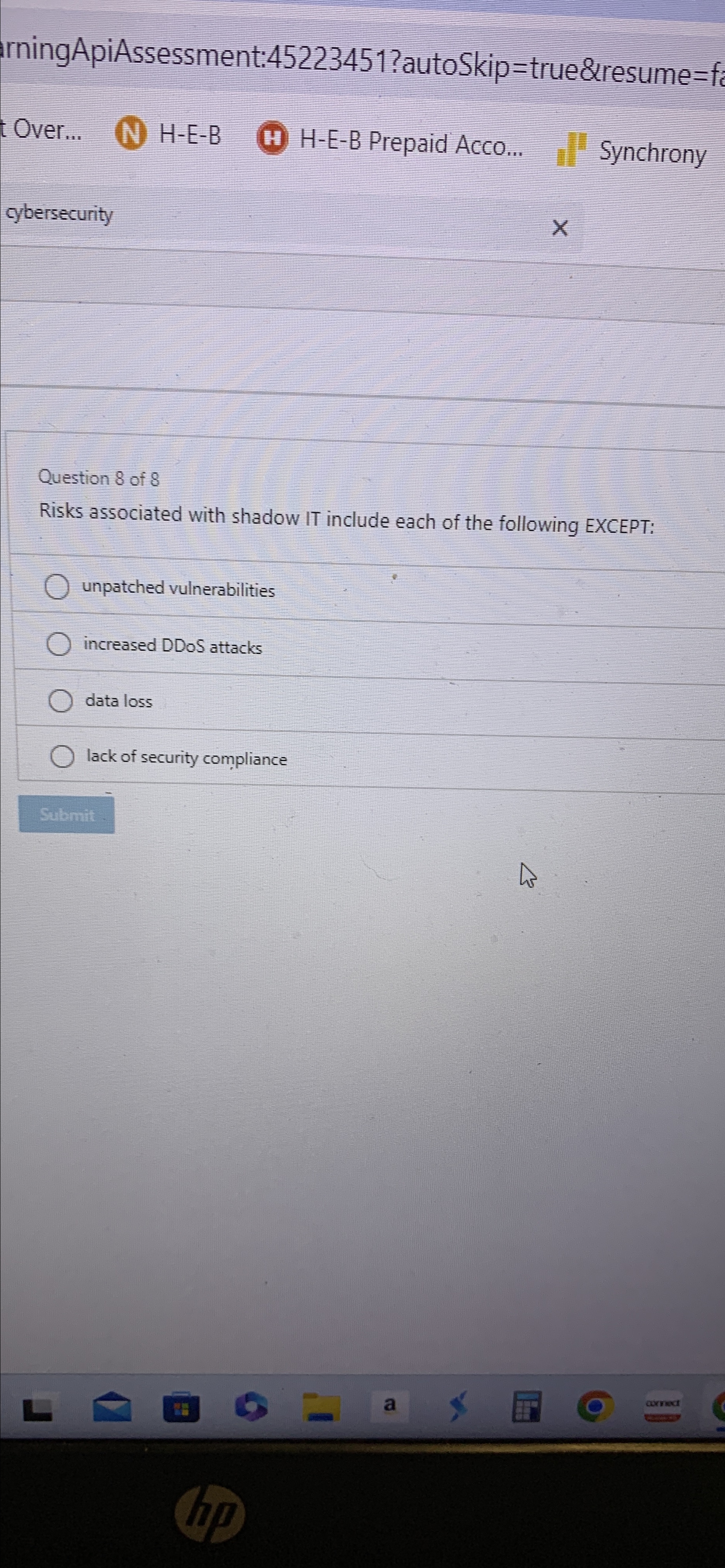
Question of
Risks associated with shadow IT include each of the following EXCEPT:
unpatched vulnerabilities
increased DDoS attacks
data loss
lack of security compliance
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


