Question: Sample Code to Change: #include #include #include int main(void){ //Useastruct to force local variable memory ordering struct { char buff[5]; char pass; } localinfo; localinfo.pass

![force local variable memory ordering struct { char buff[5]; char pass; }](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f5421bee92e_27566f5421b75474.jpg)
Sample Code to Change:
#include #include #include
int main(void){ //Useastruct to force local variable memory ordering struct { char buff[5]; char pass; } localinfo; localinfo.pass =0;
printf(" Enter thepassword: ");
gets(localinfo.buff);//Get thepassword from the user//fgets(localinfo.buff, byte_size, stdin);
if(strcmp(localinfo.buff,"byte")){// Check the password printf (" Wrong Password "); } else { printf (" Correct Password "); localinfo.pass =1;//Setaflagdenoting correct pass} if(localinfo.pass){/*NowGiveroot oradmin rightstouser*/ printf (" Congratulations! Root privileges given totheuser! "); }return0;}
Language: C
Provide Code
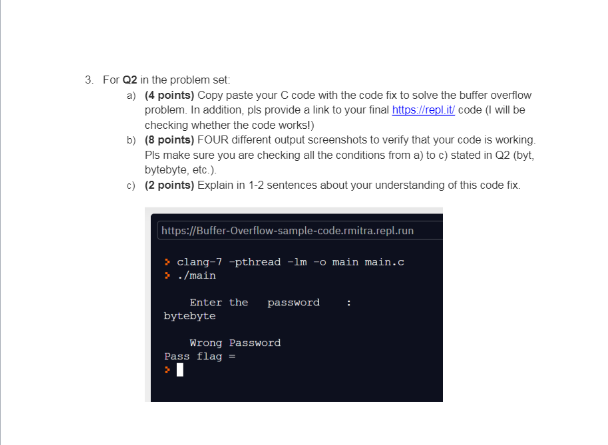
Buffer Overflow Lab Objective: To make the students familiar with the Buffer Overflow in stack and heap and help them modify and understand the code in a better manner by hands on practical's Background: In information Security and programming, a buffer overflow, or buffer overrun is an anomaly where a program, while writing data to a buffer, over runs the buffer's boundary and overwrites the adjacent memory locations. Buffers are areas of memory set aside to hold data, often while moving it from one section of a program to another, or between programs. Buffer overflows can often be triggered by malformed inputs; if one assumes all inputs will be smaller than a certain size and the buffer is created to be that size, then an anomalous transaction that produces more data could cause it to write past the end of the buffer. If this overwrites adjacent data or executable code, this may result in erratic program behaviour, including memory access errors, incorrect results and crashes Buffer Overflow Attack Function Function Paramers Paramoura Return Function Return Function Base Pointer M Code Base Power Burer Before Attack Alter Attack Procedure: Step 1: Sign in to https://repl.it/ with your email address Step 2: Write your code on the online IDE and check for errors Step 3: "Run" the program as per the given problem set. Step 4: Take screenshots for each question and submit the document in a pdf format Problem Set 1. Edit the program to demonstrate buffer overflow problem with a password of size twice the given length (eg. "bytebyte"). A reference code is attached in the assignment. 2. Rewrite the program for Q1 above to create a fix for this problem by limiting the size of user input and possibly using a different function to compare the strings. Your improved program should display an output "wrong password" for the following cases a) attempt password = "by". User input is half that of given password text. b) attempt password = "bytebyte". User input is twice that of given password text. c) attempt password = "1234". User input is a garbage text of same length d) attempt password = "12345678901234567890". User input is a garbage text which is longer than the given password Reference links: User input: http://www.cplusplus com/reference cstdio/fgets/ String functions for strcmp - http://www.cplusplus.com/reference/cstring/strcmp/ strncmp - http://www.cplusplus.com/reference/cstring/strncmp/ strlen - http://www.cplusplus.com/reference/cstring/strlen/ Deliverable Pls upload a Single PDF containing the following information: 1. (2 points) Name your file as your SE ID_>As.pdf eg jsmith 1s_As3 pdf 2. (4 points) Demonstrate buffer overflow problem with a screenshot about "Wrong Password as given in Q1 in the problem set. The user should not be getting root privileges. But the user does so because the localinfo.pass" flag gets corrupted. Sample output | https://Buffer-Overflow-sample-code.rmitra.repl.run > clang-7 -pthread -lm -o main main.c > ./main password : Enter the bytebyte Wrong Password Pass flag - y Congratulations! Root privileges given to the user! 3. For Q2 in the problem set: a) (4 points) Copy paste your C code with the code fix to solve the buffer overflow problem. In addition, pls provide a link to your final https://repl.it/code (I will be checking whether the code works!) b) (8 points) FOUR different output screenshots to verify that your code is working. Pls make sure you are checking all the conditions from a) to c) stated in 02 (byt, bytebyte, etc.) c) (2 points) Explain in 1-2 sentences about your understanding of this code fix. https://Buffer-Overflow-sample-code.rmitra.repl.run > clang-7 -pthread -lm -o main main.c > ./main Enter the password bytebyte Wrong Password Pass flag = Buffer Overflow Lab Objective: To make the students familiar with the Buffer Overflow in stack and heap and help them modify and understand the code in a better manner by hands on practical's Background: In information Security and programming, a buffer overflow, or buffer overrun is an anomaly where a program, while writing data to a buffer, over runs the buffer's boundary and overwrites the adjacent memory locations. Buffers are areas of memory set aside to hold data, often while moving it from one section of a program to another, or between programs. Buffer overflows can often be triggered by malformed inputs; if one assumes all inputs will be smaller than a certain size and the buffer is created to be that size, then an anomalous transaction that produces more data could cause it to write past the end of the buffer. If this overwrites adjacent data or executable code, this may result in erratic program behaviour, including memory access errors, incorrect results and crashes Buffer Overflow Attack Function Function Paramers Paramoura Return Function Return Function Base Pointer M Code Base Power Burer Before Attack Alter Attack Procedure: Step 1: Sign in to https://repl.it/ with your email address Step 2: Write your code on the online IDE and check for errors Step 3: "Run" the program as per the given problem set. Step 4: Take screenshots for each question and submit the document in a pdf format Problem Set 1. Edit the program to demonstrate buffer overflow problem with a password of size twice the given length (eg. "bytebyte"). A reference code is attached in the assignment. 2. Rewrite the program for Q1 above to create a fix for this problem by limiting the size of user input and possibly using a different function to compare the strings. Your improved program should display an output "wrong password" for the following cases a) attempt password = "by". User input is half that of given password text. b) attempt password = "bytebyte". User input is twice that of given password text. c) attempt password = "1234". User input is a garbage text of same length d) attempt password = "12345678901234567890". User input is a garbage text which is longer than the given password Reference links: User input: http://www.cplusplus com/reference cstdio/fgets/ String functions for strcmp - http://www.cplusplus.com/reference/cstring/strcmp/ strncmp - http://www.cplusplus.com/reference/cstring/strncmp/ strlen - http://www.cplusplus.com/reference/cstring/strlen/ Deliverable Pls upload a Single PDF containing the following information: 1. (2 points) Name your file as your SE ID_>As.pdf eg jsmith 1s_As3 pdf 2. (4 points) Demonstrate buffer overflow problem with a screenshot about "Wrong Password as given in Q1 in the problem set. The user should not be getting root privileges. But the user does so because the localinfo.pass" flag gets corrupted. Sample output | https://Buffer-Overflow-sample-code.rmitra.repl.run > clang-7 -pthread -lm -o main main.c > ./main password : Enter the bytebyte Wrong Password Pass flag - y Congratulations! Root privileges given to the user! 3. For Q2 in the problem set: a) (4 points) Copy paste your C code with the code fix to solve the buffer overflow problem. In addition, pls provide a link to your final https://repl.it/code (I will be checking whether the code works!) b) (8 points) FOUR different output screenshots to verify that your code is working. Pls make sure you are checking all the conditions from a) to c) stated in 02 (byt, bytebyte, etc.) c) (2 points) Explain in 1-2 sentences about your understanding of this code fix. https://Buffer-Overflow-sample-code.rmitra.repl.run > clang-7 -pthread -lm -o main main.c > ./main Enter the password bytebyte Wrong Password Pass flag =

![force local variable memory ordering struct { char buff[5]; char pass; }](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f5421bee92e_27566f5421b75474.jpg)




