Question: Sample Output: Encode text Decode text Exit Please select an option between 1 and 3 : 1 Please enter the text to encode: My horse
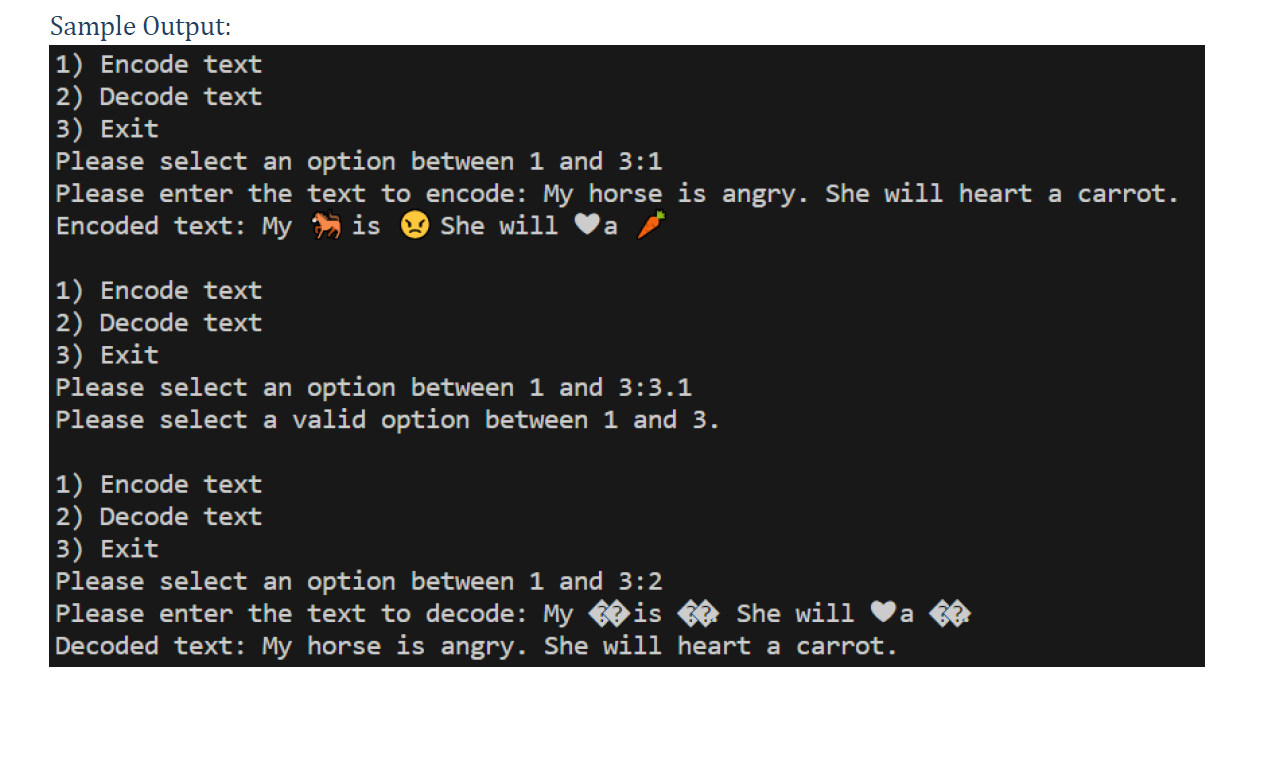
Sample Output:
Encode text
Decode text
Exit
Please select an option between and :
Please enter the text to encode: My horse is angry. She will heart a carrot.
Encoded text: My is She will a
Encode text
Decode text
Exit
Please select an option between and :
Please select a valid option between and
Encode text
Decode text
Exit
Please select an option between and :
Please enter the text to decode: My is he will a
Decoded text: My horse is angry. She will heart a carrot.If after going through the whole input list, matchfound is False
Add the original word at wordindex to the encrypted string
Assignment : Secret Codes Arrays & Functions
Assignment for COSC Intro to Programming
Page of
Requirements for the Cipher Functions:
In this case, we will be using a cipher to translate a message to or from emoji. A Substitution cipher is a very simple type of cipher that operates by replacing characters or words from one form of communication with those from another. In our case, we will convert from English letters into emoji. Your encode and decode functions will each have one parameter, which is the message to be translated.
English
Unicode
Emoji
English
Unicode
Emoji
English
Unicode
Emoji
UFAF
cat
UF
horse
UFE
angry mad
UF
clap
UFF
map
UFFA
alien
UFD
cookie
cow
UFA
OK okay
UFC
apple
UFE
dog
UF
sad
UF
banana
UFC
egg
elephant
UFA
sheep
ewe
UF
bee
UFD
fish
UFF
sleep
bed
UFCC
bird
UF
fox
UFA
tree
UF
car
UF
happy
UF
wave
UFB
carrot
UF
heart
U
zombie
UFDF
For your assignment submission, please limit the words to translate to those included above, which were chosen intentionally by this courses professors. However, if youd like to extend things somewhat, you can include the secondary words like mad and okay that are shown in parentheses in the chart.
There are many ways to implement this in Python, but probably the easiest way for our needs would be to declare two arrays: one includes a list of words, and the other includes the emoji equivalents of those words. Then, given a message, for each word, if that word is in the first array, match that words position in the first array with the same position in the second array. Ensure that the translation happens regardless of case.
Here is some partial pseudocode for the encode function that you can make use of:
Start with an empty string called encodedstring
Use the split method to turn the input message into a list of words For each wordindex, counting up from to the length of the input word list
Assume that there is no match found matchfound False
For each translationindex in the emoji word list
If the word at wordindex equals the input word at translationindex
Add the emoji at translationindex to the encodedstring Set matchfound to True
If after going through the whole input list, matchfound is False
Add the original word at wordindex to the encrypted stringEven perfectly translated into Python, the output from this may not be perfect and troubleshooting the differences in how the input displays is intentionally left as an exercise.
Style Guide:
To be eligible for full marks on this or any assignment in this course your application must conform to the requirements as outlined above as well as our prescribed style guide, in this case making sure to observe the PEP naming conventions for Python as well as appropriate and complete program documentation.
Development Hints:
As always, start with your planning steps. The pseudocode shown above may be part of the process and plan steps and of
Only after planning, consider how you can translate the given pseudocode into Python code.
Ciphers are a very common programming exercise and thus there are numerous reference materials and possibly even full solutions available on the web. However, be cautious with these!
o Make sure any borrowed code works and that your program actually meets our requirements.
o Make sure all code in your program conforms to our PEP style guide.
o Reference any code directly taken from any form of online resource or another person, or this will be considered an incident of plagiarism. You can just do this in a comment before the part you have taken from another source.
Please make a Plan output input and pseoudocode
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


