Question: Scenario As a senior cybersecurity engine r for an organization, you review past incident reports involving the recovery of systems or applications from a backup
Scenario
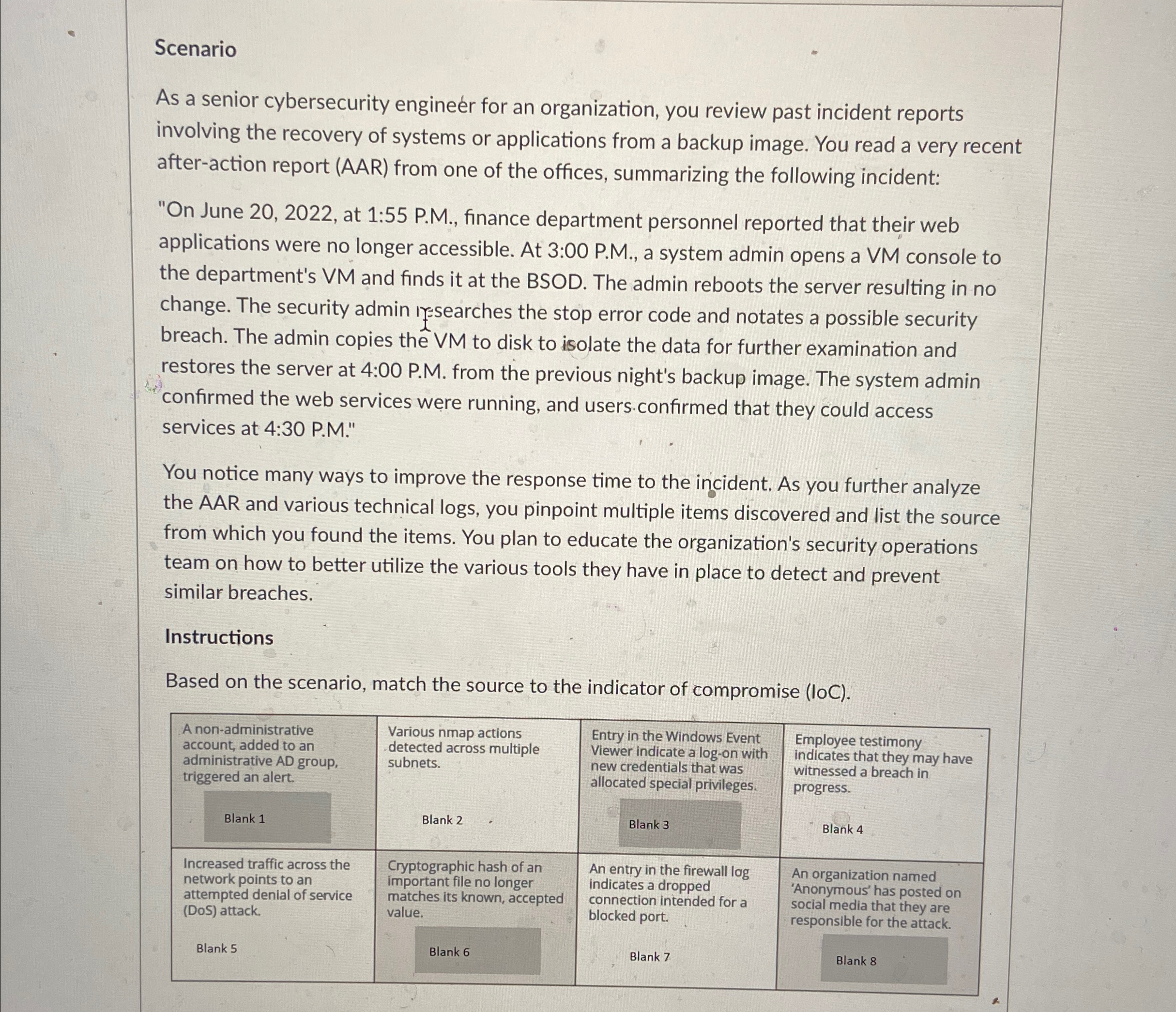
As a senior cybersecurity enginer for an organization, you review past incident reports involving the recovery of systems or applications from a backup image. You read a very recent afteraction report AAR from one of the offices, summarizing the following incident:
On June at : PM finance department personnel reported that their web applications were no longer accessible. At : PM a system admin opens a VM console to the department's VM and finds it at the BSOD. The admin reboots the server resulting in no change. The security admin ifsearches the stop error code and notates a possible security breach. The admin copies the VM to disk to isolate the data for further examination and restores the server at : PM from the previous night's backup image. The system admin confirmed the web services were running, and users.confirmed that they could access services at : PM
You notice many ways to improve the response time to the incident. As you further analyze the AAR and various technical logs you pinpoint multiple items discovered and list the source from which you found the items. You plan to educate the organization's security operations team on how to better utilize the various tools they have in place to detect and prevent similar breaches.
Instructions
Based on the scenario, match the source to the indicator of compromise IoC
tabletableA nonadministrativeaccount added to anadministrative AD group,triggered an alert.Blank tableVarious nmap actionsdetected across multiplesubnetsBlank tableEntry in the Windows EventViewer indicate a logon withnew credentials that wasallocated special privileges.Blank tableEmployee testimonyindicates that they may havewitnessed a breach inprogressBlank tableIncreased traffic across thenetwork points to anattempted denial of serviceDoS attack.tableCryptographic hash of animportant file no longermatches its known, acceptedvaluetableAn entry in the firewall logindicates a droppedconnection intended for ablocked port.tableAn organization namedAnonymous has posted onsocial media that they areresponsible for the attack.Blank Blank Blank Blank
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


