Question: Section A (True False) 30 marks True False Please tick (V) in the appropriate boxes for the correct answers. Provide justification for your answers 8.
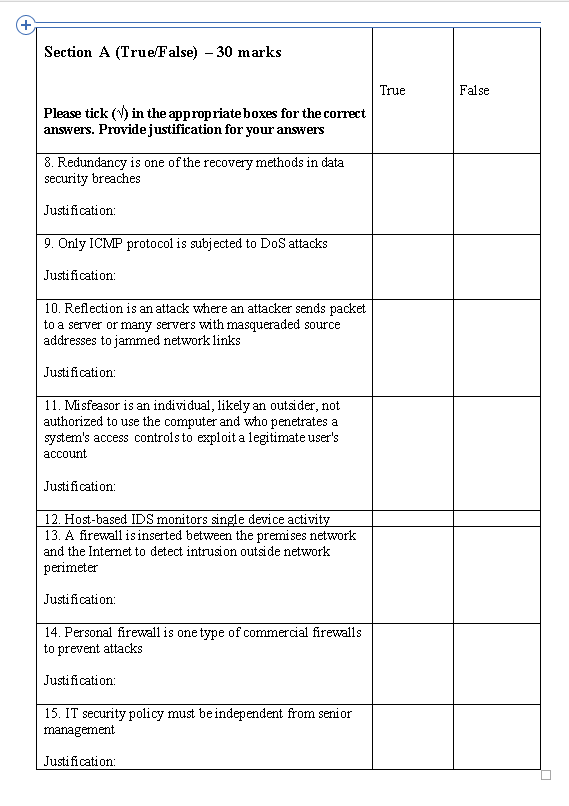
Section A (True False) 30 marks True False Please tick (V) in the appropriate boxes for the correct answers. Provide justification for your answers 8. Redundancy is one of the recovery methods in data security breaches Justification: 9. Only ICMP protocol is subjected to DoS attacks Justification: 10. Reflection is an attack where an attacker sends packet to a server or many servers with masqueraded source addresses to jammed network links Justification: 11. Misfeasor is an individual, likely an outsider, not authorized to use the computer and who penetrates a system's access controls to exploit a legitimate user's account Justification: 12. Host-based IDS monitors single device activity 13. A firewall is inserted between the premises network and the Internet to detect intrusion outside network perimeter Justification: 14. Personal firewall is one type of commercial firewalls to prevent attacks Justification: 15. IT security policy must be independent from senior management Justification
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


