Question: SECTION B: Grade Rubrics The rubric used for evaluating the assignment ( II ) above. table [ [ Criteria , Excellent ( 2 .
SECTION B: Grade Rubrics
The rubric used for evaluating the assignment II above.
tableCriteriaExcellent Good Satisfactory tableNeedsImprovement tableUnderstanding ofCase StudytableDemonstrates adeepunderstanding ofthe case study,including key facts,issues andcontexttableShows a solidunderstanding ofthe case study,capturingimportant detailsand context.tableDemonstrates abasicunderstanding ofthe case study butmay miss somekey details.tableDisplays a limitedunderstanding ofthe case study,missing significantdetailsInstallation Process,tableSuccessfullyinstalls theProVerif with noerrors followingall providedinstructionstableInstalls theProverif withminor errors thatdo not impactfunctionalityfollowing mostprovidedinstructionstableInstalls theProVerif withsome errors,requiringadditionaltroubleshootingtableUnable to install theProVeriftableExecution of CaseStudy TaskstableExecutes all casestudy tasksaccurately andefficientlytableCompletes mosttasks with minorerrors orinefficienciestableCompletes sometasks withsignificant errorsor inefficiencies.tableUnable to completecase study tasks.tableOverallDocumentation andPresentationtableProvides clear andcomprehensivedocumentation ofthe installationprocess and theexecution of thecodetableDocuments theinstallationprocess but lacksclarity orcompletenessNAtableDoes not providedocumentation ProVerif is a computer security tool used for the formal verification of security properties in cryptographic
protocols. It falls under the category of formal methods, which involve mathematical techniques for specifying,
modeling, and verifying systems. This software can be used to prove the secrecy authenticity, and equivalence
properties of cryptographic protocols.
Todo list:
Download the Proverif Manual from Here.
Install the Proverif software according to the instructions in section in the manual.
You are required to run the case study in Chapter specifically and This includes;
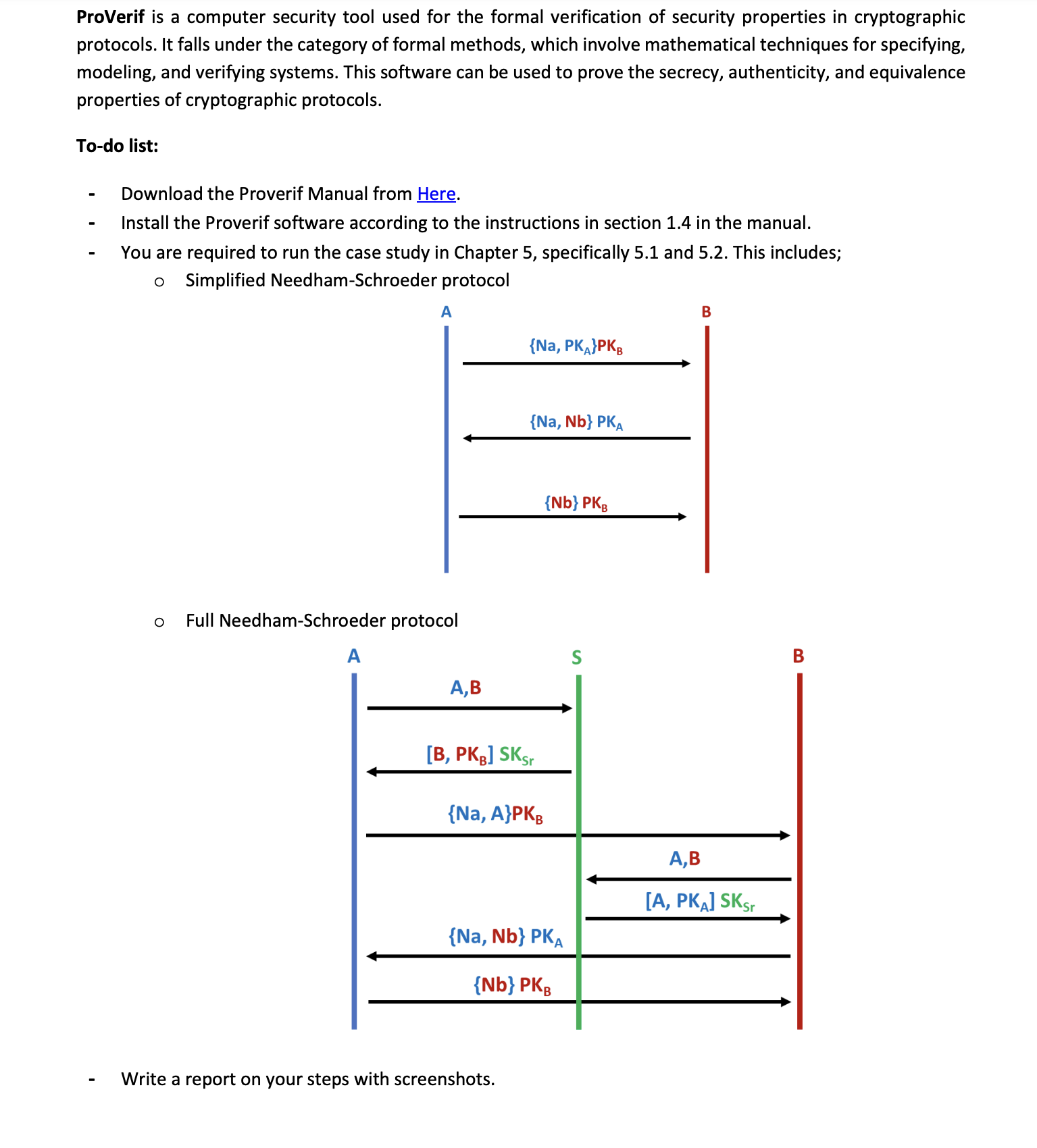
Simplified NeedhamSchroeder protocol
Full NeedhamSchroeder protocol
Write a report on your steps with screenshots.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


