Question: Select a correct statement regarding encryption methods. Multiple Choice Most companies prefer using asymmetric-key encryption method for data transmission. o Symmetric-key encryption method is used
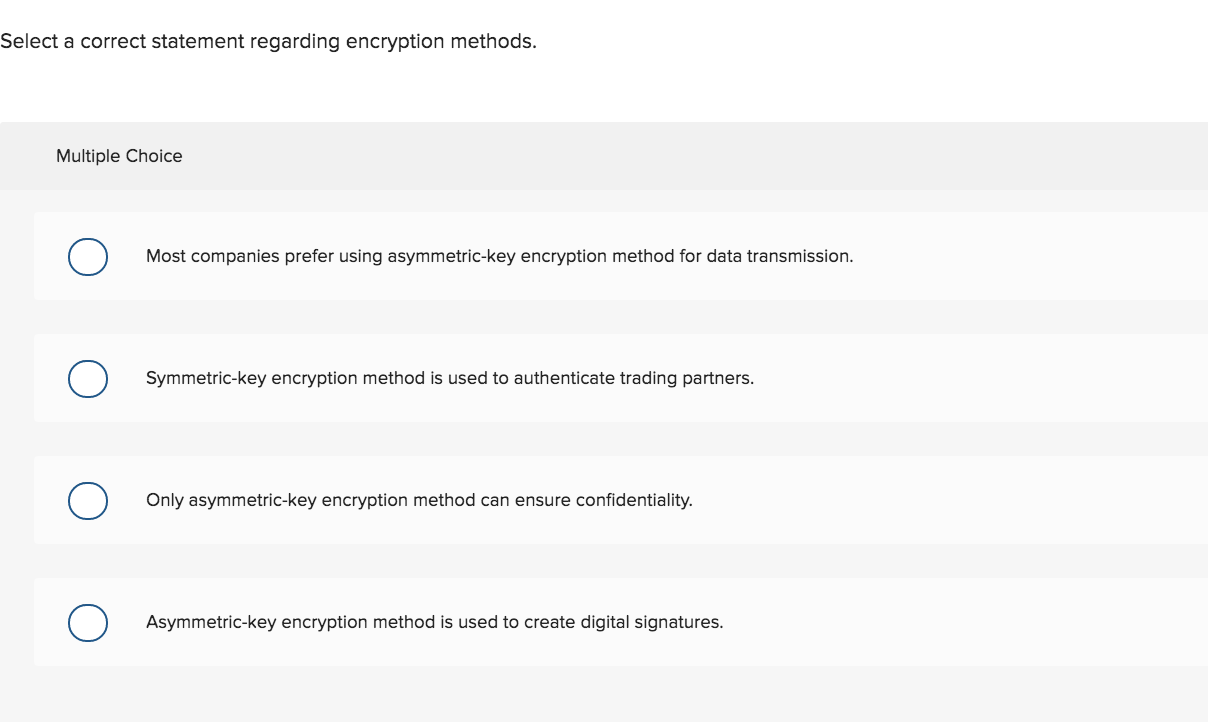
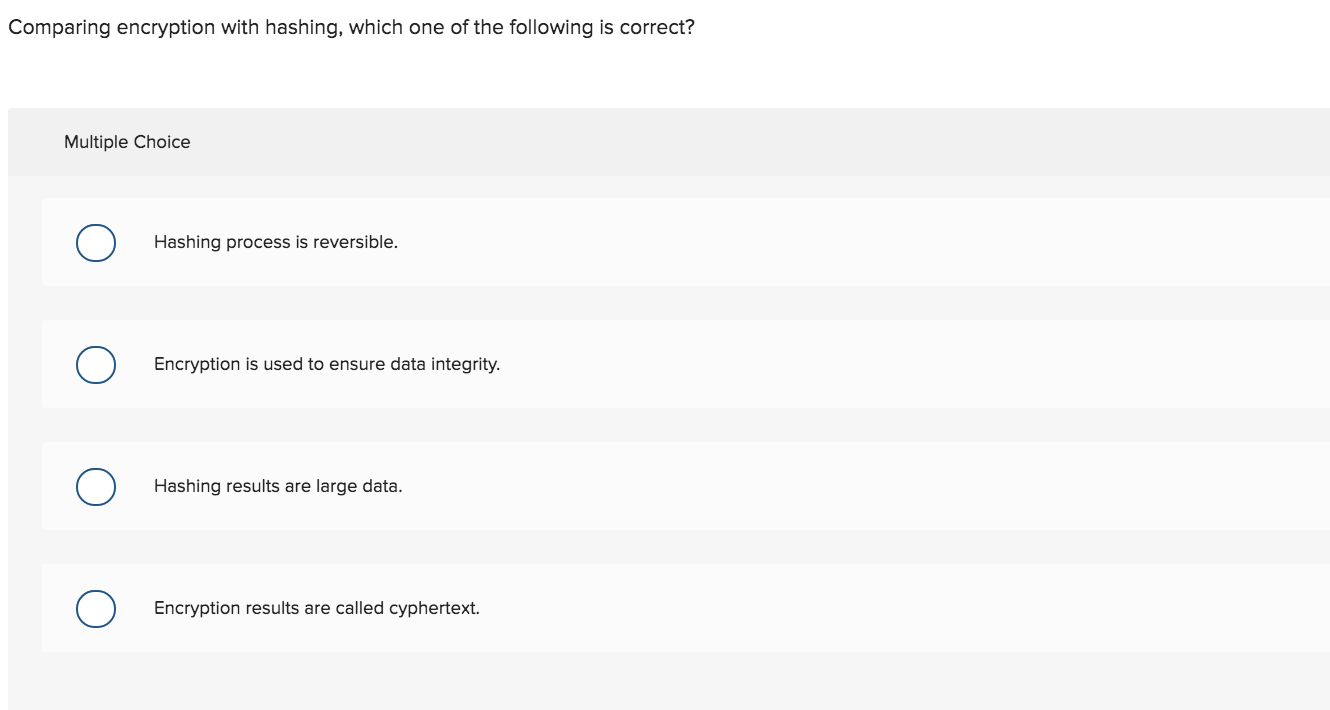
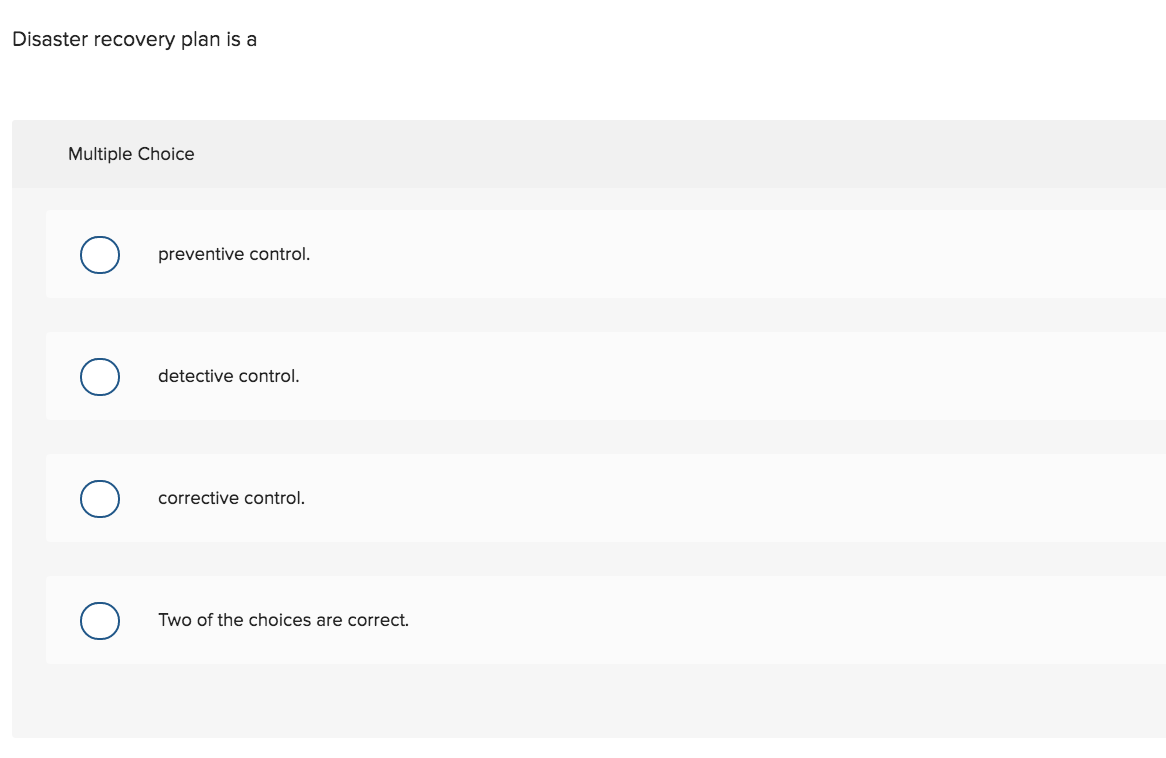
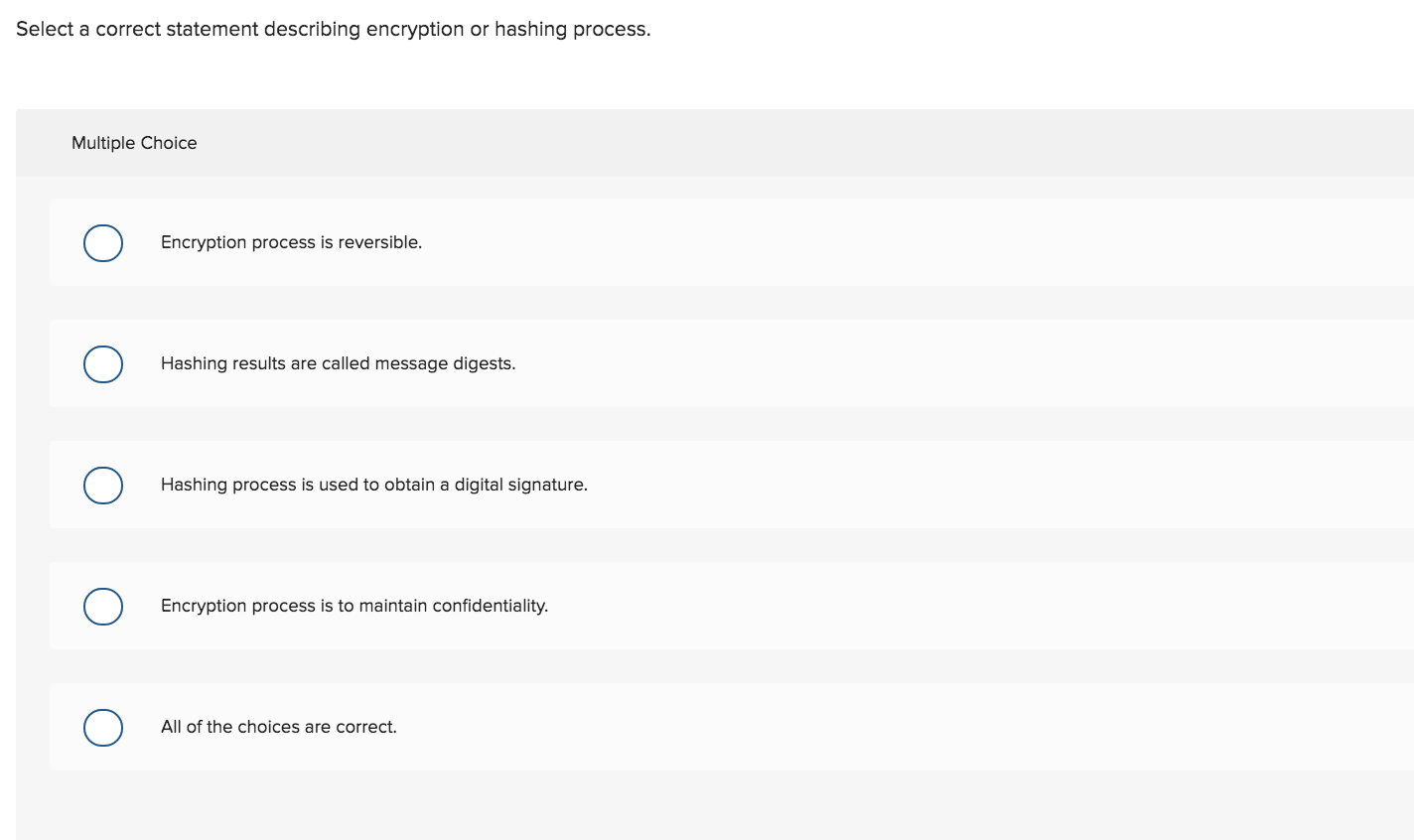
Select a correct statement regarding encryption methods. Multiple Choice Most companies prefer using asymmetric-key encryption method for data transmission. o Symmetric-key encryption method is used to authenticate trading partners. Only asymmetric-key encryption method can ensure confidentiality. Asymmetric-key encryption method is used to create digital signatures. Comparing encryption with hashing, which one of the following is correct? Multiple Choice Hashing process is reversible. Encryption is used to ensure data integrity. Hashing results are large data. Encryption results are called cyphertext. Disaster recovery plan is a Multiple Choice preventive control. detective control. corrective control. Two of the choices are correct. Select a correct statement describing encryption or hashing process. Multiple Choice Encryption process is reversible. Hashing results are called message digests. Hashing process is used to obtain a digital signature. Encryption process is to maintain confidentiality. All of the choices are correct. Select a correct statement regarding encryption methods. Multiple Choice Most companies prefer using asymmetric-key encryption method for data transmission. o Symmetric-key encryption method is used to authenticate trading partners. Only asymmetric-key encryption method can ensure confidentiality. Asymmetric-key encryption method is used to create digital signatures
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


