Question: Selective Victim Cache Simulator: Compares three different cache policies. Selective Victim Cache Simulator use the following simulator site. http://www.ecs.umass.edu/ece/koren/architecture/SVCache/default.htm Notes: 1) After setting up the
Selective Victim Cache Simulator: Compares three different cache policies. Selective Victim Cache Simulator use the following simulator site.
http://www.ecs.umass.edu/ece/koren/architecture/SVCache/default.htm
Notes: 1) After setting up the mentioned specifications, INITIALIZE and then RUN.
2) After changing a certain setting, if for example, you change the cache to selective victim from normal cache; make this change, press INITIALIZE and then only RUN. Make sure that the two tables on the right are cleared before you RUN the simulation.
3) The output values are in the boxes allocated for each cache type.
1) Use the following specifications:
| Specification | Value |
| Block size | 32 bytes |
| L1,L2,Victim Cache type | Direct Mapped |
| Memory traces | T1(80K) |
| L1-Access time | 5 |
| L2-Access time | 10 |
| Victim cache access time | 1 |
| Memory access time | 10 |
(a) Where does the victim lie in the memory hierarchy?
(b) Compare the memory access times for a system with and without victim cache. What do you infer?
| L1 size | L2 size | Victim size | Momery Access time - w/o VC | Memory Access time - w VC |
| 4KB | 16KB | 1KB | ||
| 4KB | 32KB | 1KB | ||
| 8KB | 32KB | 2KB | ||
| 8KB | 64KB | 4KB |
(c) How does the cache policy affect the victim cache effectiveness? On what type of cache does this victim caching technique prove most effective?
| L1XL2XVC sizes | Direct Mapped - w/o VC | Direct Mapped - with VC | 2-way SA - w/o VC | 2-way SA with VC | 4-way SA w/o VC | 4-way SA with VC |
| 4KBx16KBx1KB | ||||||
| 4KBx32KBx2KB | ||||||
| 8KBx64KBx4KB | ||||||
2) Compare the L1 and L2 cache hits, victim cache hits between the two for different cache types and write down your inference. Use the same setup as before.
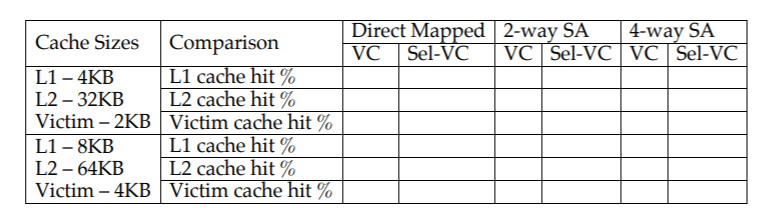
(a) What is the difference between victim and selective victim caching techniques?
(b) How better is the selective victim cache?
Direct Mapped | 2-way SA 4-way SA VC Sel-VC VC Sel-VC VCSel-VC Cache SizesComparison LI-AKB | L1 cache hit % L2-32KB | L2 cache hit % Victim-2KB | Victim cache hit % | LI-8KB | L1 cache hit % L2-64KB | L2 cache hit % | Victim-4KB | Victim cache hit % | | | Direct Mapped | 2-way SA 4-way SA VC Sel-VC VC Sel-VC VCSel-VC Cache SizesComparison LI-AKB | L1 cache hit % L2-32KB | L2 cache hit % Victim-2KB | Victim cache hit % | LI-8KB | L1 cache hit % L2-64KB | L2 cache hit % | Victim-4KB | Victim cache hit % | | |
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


