Question: . Short Answers: Security Analysis Consider the scenario in which a customer physically goes to a Starbucks store, and uses their physical plastic credit car
 .
.
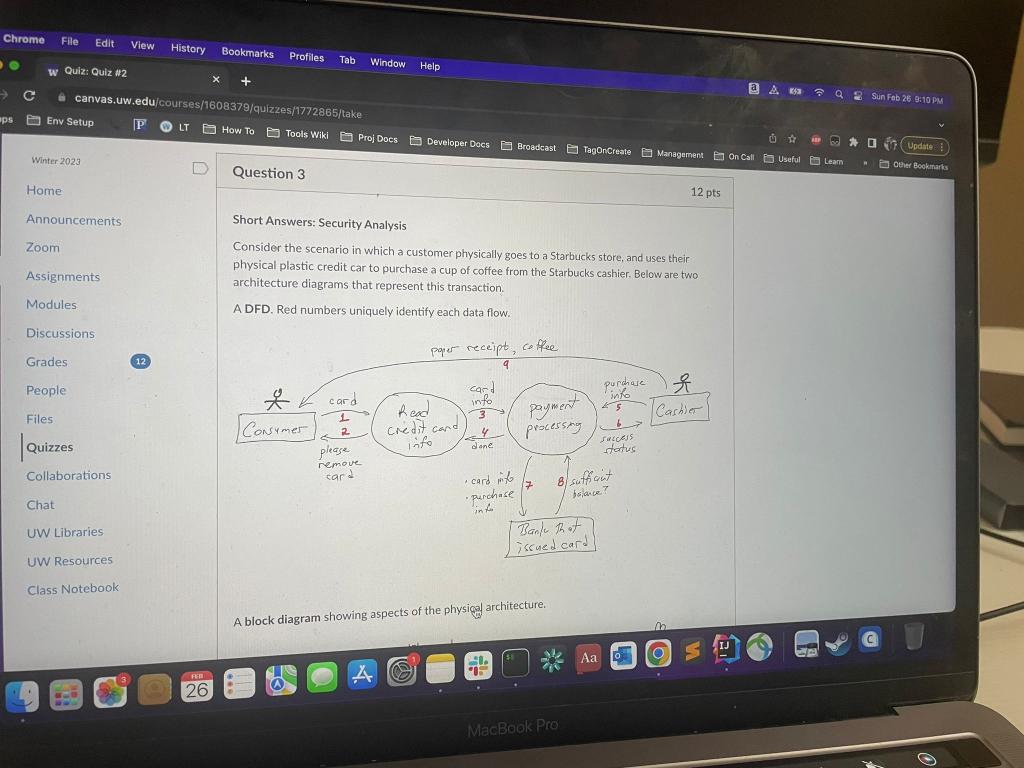
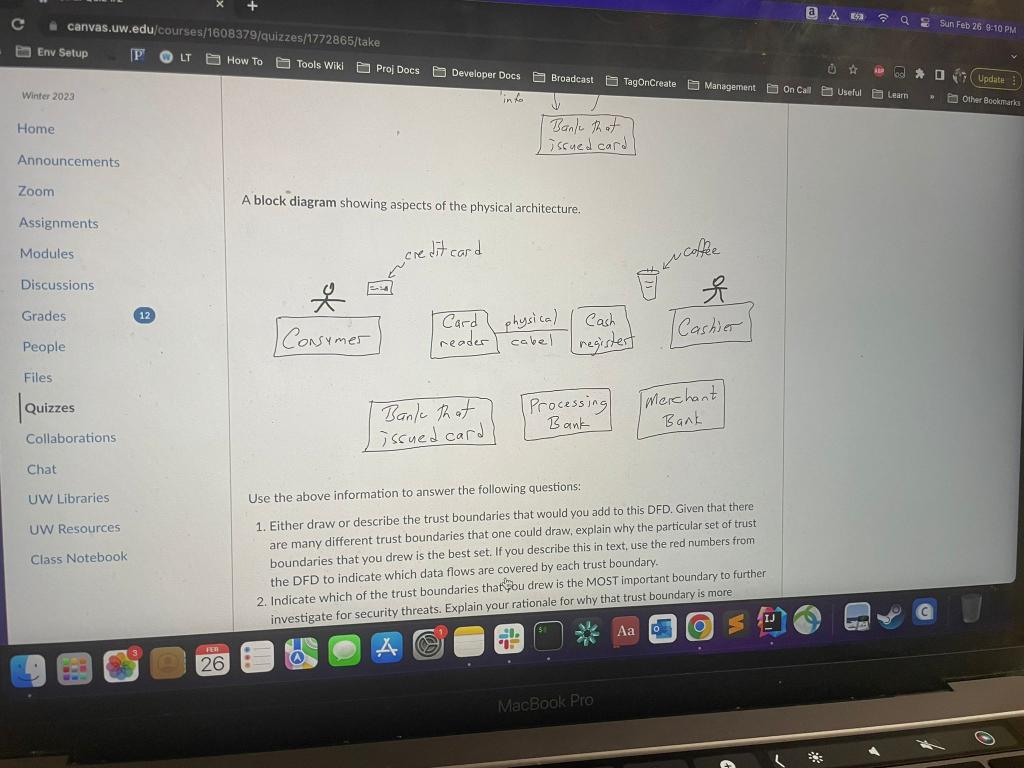
Short Answers: Security Analysis Consider the scenario in which a customer physically goes to a Starbucks store, and uses their physical plastic credit car to purchase a cup of coffee from the Starbucks cashier. Below are two architecture diagrams that represent this transaction. A DFD. Red numbers uniquely identify each data flow. A block diagram showing aspects of the physigal architecture. A block diagram showing aspects of the physical architecture. Use the above information to answer the following questions: 1. Either draw or describe the trust boundaries that would you add to this DFD. Given that there are many different trust boundaries that one could draw, explain why the particular set of trust boundaries that you drew is the best set. If you describe this in text, use the red numbers from the DFD to indicate which data flows are covered by each trust boundary. 2. Indicate which of the trust boundaries that fou drew is the MOST important boundary to further investigate for security threats. Explain your rationale for why that trust boundary is more Short Answers: Security Analysis Consider the scenario in which a customer physically goes to a Starbucks store, and uses their physical plastic credit car to purchase a cup of coffee from the Starbucks cashier. Below are two architecture diagrams that represent this transaction. A DFD. Red numbers uniquely identify each data flow. A block diagram showing aspects of the physigal architecture. A block diagram showing aspects of the physical architecture. Use the above information to answer the following questions: 1. Either draw or describe the trust boundaries that would you add to this DFD. Given that there are many different trust boundaries that one could draw, explain why the particular set of trust boundaries that you drew is the best set. If you describe this in text, use the red numbers from the DFD to indicate which data flows are covered by each trust boundary. 2. Indicate which of the trust boundaries that fou drew is the MOST important boundary to further investigate for security threats. Explain your rationale for why that trust boundary is more
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


