Question: someone please help me solve this problem please, thank you This practical will focus on chapter 8 (malware analysis), you will need copy of the
someone please help me solve this problem please, thank you
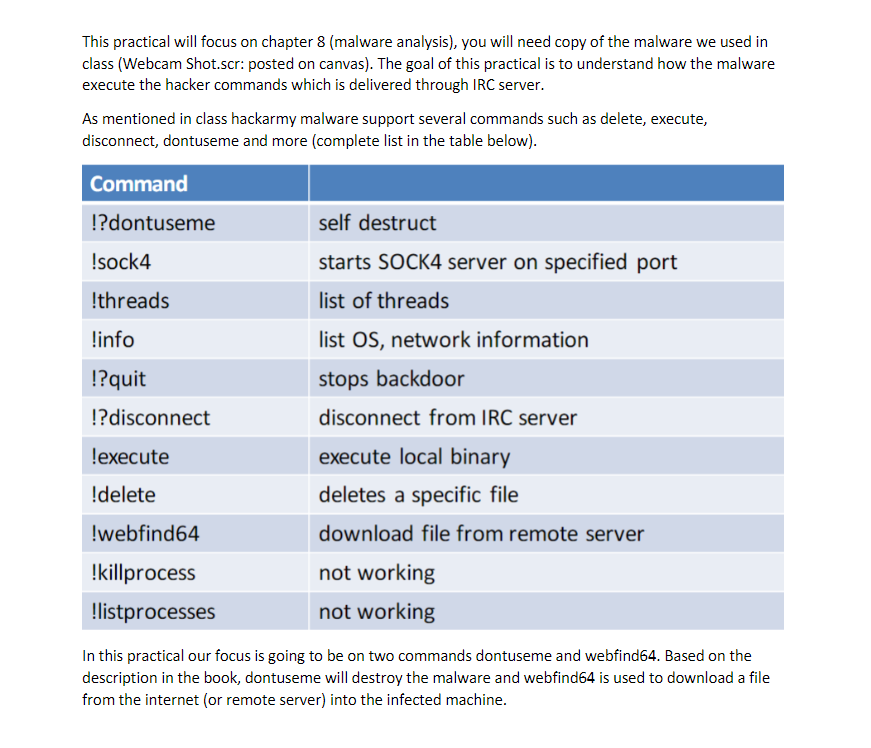
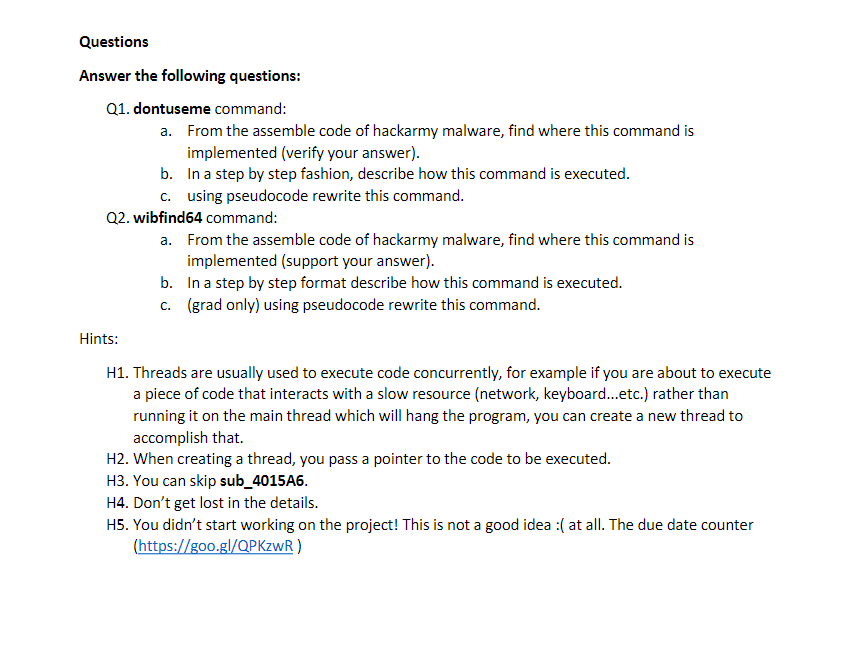
This practical will focus on chapter 8 (malware analysis), you will need copy of the malware we used in class (Webcam Shot.scr: posted on canvas). The goal of this practical is to understand how the malware execute the hacker commands which is delivered through IRC server As mentioned in class hackarmy malware support several commands such as delete, execute, disconnect, dontuseme and more (complete list in the table below) Command ?dontuseme sock4 threads info !?quit ?disconnect lexecute delete self destruct starts SOCK4 server on specified port list of threads list OS, network information stops backdoor disconnect from IRC server execute local binary deletes a specific file download file from remote server not working not working webfind64 !killprocess listprocesses In this practical our focus is going to be on two commands dontuseme and webfind64. Based on the description in the book, dontuseme will destroy the malware and webfind64 is used to download a file from the internet (or remote server) into the infected machine This practical will focus on chapter 8 (malware analysis), you will need copy of the malware we used in class (Webcam Shot.scr: posted on canvas). The goal of this practical is to understand how the malware execute the hacker commands which is delivered through IRC server As mentioned in class hackarmy malware support several commands such as delete, execute, disconnect, dontuseme and more (complete list in the table below) Command ?dontuseme sock4 threads info !?quit ?disconnect lexecute delete self destruct starts SOCK4 server on specified port list of threads list OS, network information stops backdoor disconnect from IRC server execute local binary deletes a specific file download file from remote server not working not working webfind64 !killprocess listprocesses In this practical our focus is going to be on two commands dontuseme and webfind64. Based on the description in the book, dontuseme will destroy the malware and webfind64 is used to download a file from the internet (or remote server) into the infected machine
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


