Question: Suppose that a C array has been declared as follows: int a[5][8][4]; (a) Give the access function for this array, assuming that the address of
Suppose that a C array has been declared as follows:
int a[5][8][4];
(a) Give the access function for this array, assuming that the address of a is 1000 and
int values occupy four bytes.
(b) What is the address of a[2][4][3]?
Here are the notes:
![Suppose that a C array has been declared as follows: int a[5][8][4];](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3d67f8b9df_19166f3d67f26bcd.jpg)
![is the address of a[2][4][3]? Here are the notes: Implementation of Array](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3d68158a08_19266f3d680ed044.jpg)
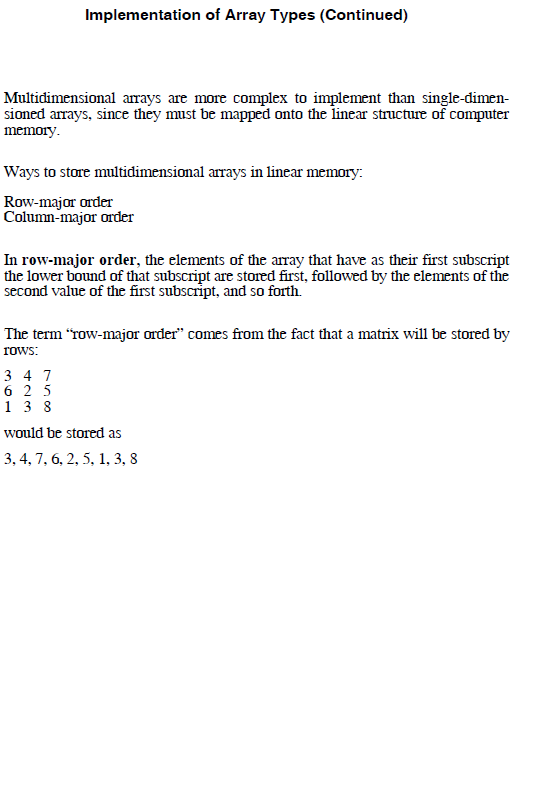
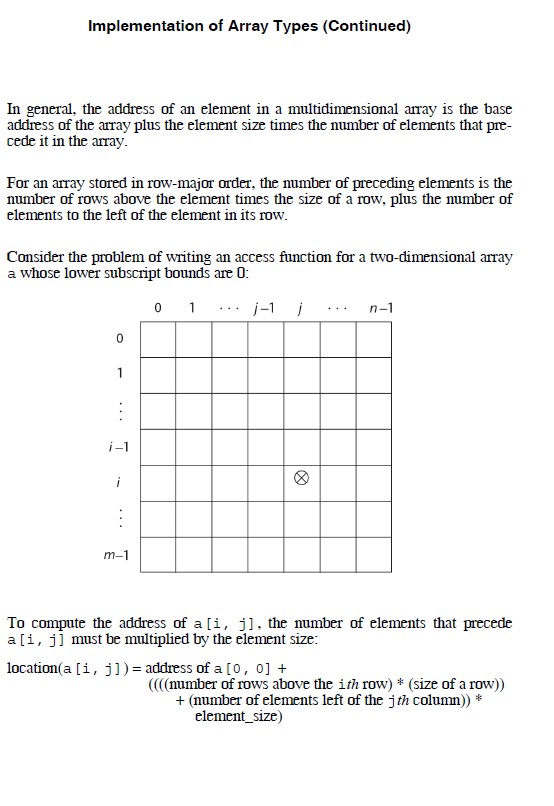
Implementation of Array Types The code to allow accessing of array elements must be generated at compile time. At run time, this code is executed to produce element addresses Suppose that list is a one-dimensional array whose lower subscript bound is 0. The following access function will compute the address of list [k] address (list [k]) address list [0 k element size The first operand of the addition is the constant part and the second is the vari- able part. If the element type is statically bound and the array is statically bound to storage, then the value of the constant part can be computed before mn time. However, the addition and multiplication operations must be done at run time. The access function can be generalized to allow an arbitrary lower bound address (list [k]) address (list [lower bound] (k-lower bound) element size) Next, it is rewritten so that it consists of a constant part and a variable part: address(list [k]) address(list [lower bound] lower bound element size) (k element size If the address of the anray is not known until run time, the subtraction must be done when the array is allocated. A one-dimensional array will require acompile-time descriptor. A mn-time descriptor may be also be needed if mn-time checking of index ranges is performed or if any attributes of the array are dynamic If the subscript ranges are static, the ranges can be incorporated into the code that does the checking, eliminating the need for the run-time descriptor
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


