Question: Suppose that you have the executable file for a program that requires a serial number, and the serial number entry routine contains an exploitable buffer
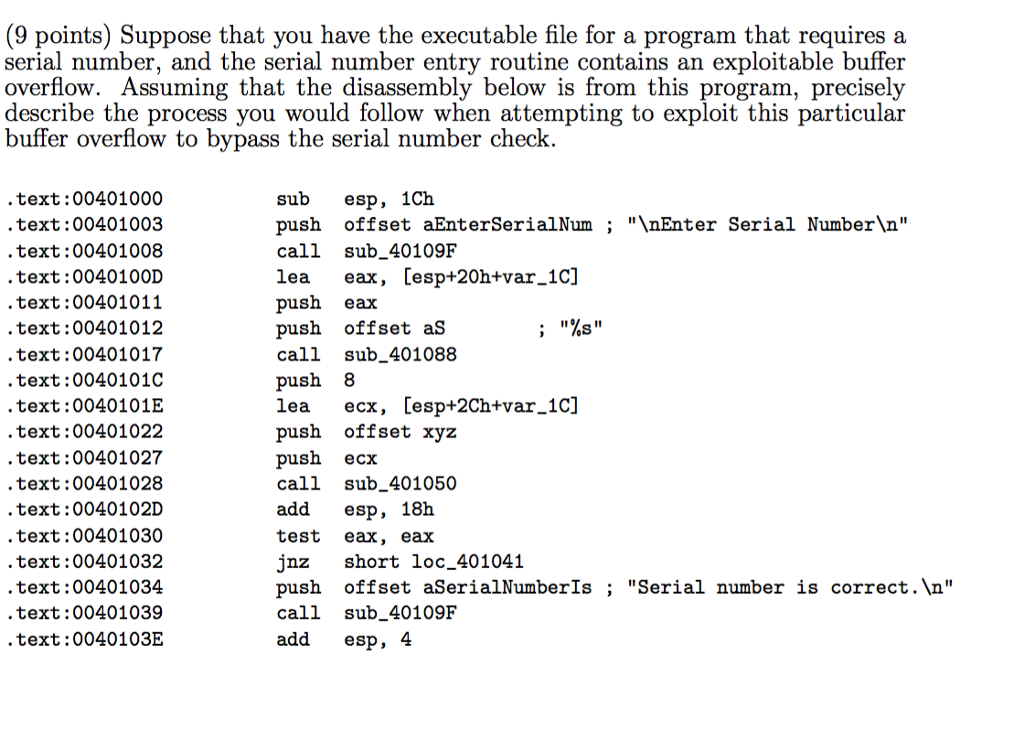
Suppose that you have the executable file for a program that requires a serial number, and the serial number entry routine contains an exploitable buffer overflow. Assuming that the disassembly below is from this program, precisely describe the process you would follow when attempting to exploit this particular buffer overflow to bypass the serial number check. text:00401000 sub esp, 1Ch text:00401003 push offset aEnterSerialNum; " Enter Serial Number " text:00401008 call sub_40109F text:0040100D lea eax, [esp+20h+var_1C] text:00401011 push eax text:00401012 push offset aS; "%s" text:00401017 call sub_401088 text:004010C push 8 text:0040101E lea ecx, [esp+2Ch+var_1C] text:00401022 push offset xyz text:00401027 push ecx text:00401028 call sub_401050 text:0040102D add esp, 18h text:00401030 test eax, eax text:00401032 jz short loc_401041 text:00401034 push offset aSerialNumberIs; " "Serial number is correct. " Text:00401039 call sub_40109F text:0040103E and esp, 4
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


