Question: Task 1 (1%): Encrypt an example text with Cryptool. For the key lengths of 56 bits, enter the input key of 64 bits to obtain
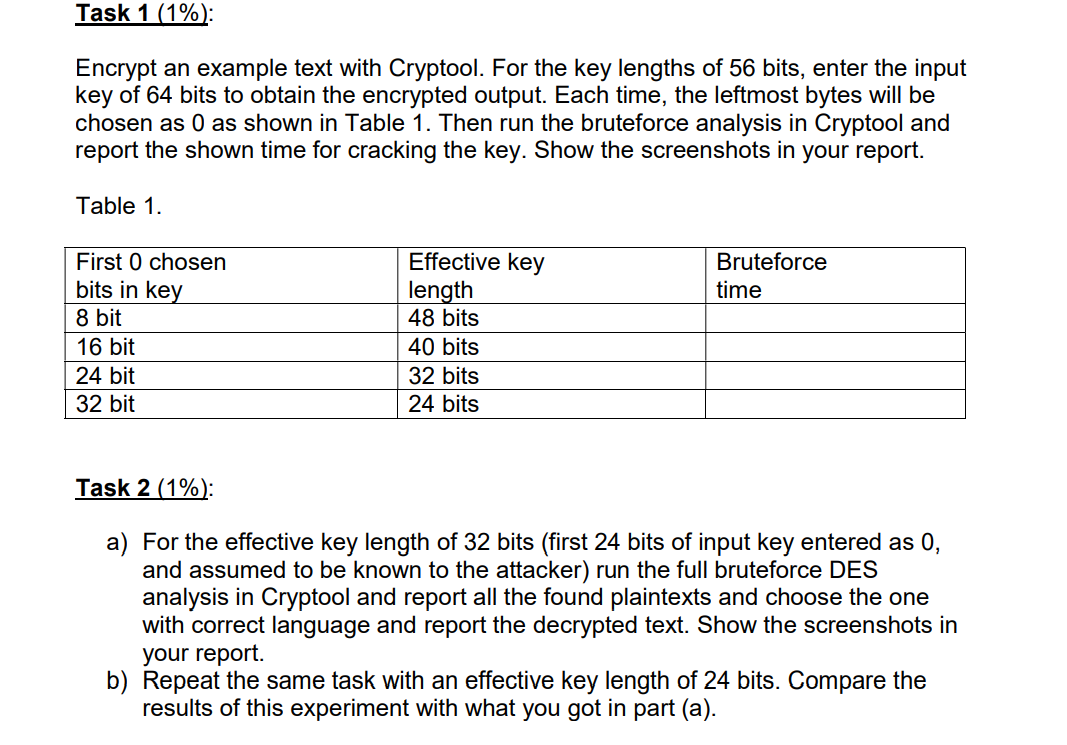
Task 1 (1%): Encrypt an example text with Cryptool. For the key lengths of 56 bits, enter the input key of 64 bits to obtain the encrypted output. Each time, the leftmost bytes will be chosen as 0 as shown in Table 1. Then run the bruteforce analysis in Cryptool and report the shown time for cracking the key. Show the screenshots in your report. Table 1. Bruteforce time First O chosen bits in key 8 bit 16 bit 24 bit 32 bit Effective key length 48 bits 40 bits 32 bits 24 bits Task 2 (1%): a) For the effective key length of 32 bits (first 24 bits of input key entered as 0, and assumed to be known to the attacker) run the full bruteforce DES analysis in Cryptool and report all the found plaintexts and choose the one with correct language and report the decrypted text. Show the screenshots in your report. b) Repeat the same task with an effective key length of 24 bits. Compare the results of this experiment with what you got in part (a). Task 1 (1%): Encrypt an example text with Cryptool. For the key lengths of 56 bits, enter the input key of 64 bits to obtain the encrypted output. Each time, the leftmost bytes will be chosen as 0 as shown in Table 1. Then run the bruteforce analysis in Cryptool and report the shown time for cracking the key. Show the screenshots in your report. Table 1. Bruteforce time First O chosen bits in key 8 bit 16 bit 24 bit 32 bit Effective key length 48 bits 40 bits 32 bits 24 bits Task 2 (1%): a) For the effective key length of 32 bits (first 24 bits of input key entered as 0, and assumed to be known to the attacker) run the full bruteforce DES analysis in Cryptool and report all the found plaintexts and choose the one with correct language and report the decrypted text. Show the screenshots in your report. b) Repeat the same task with an effective key length of 24 bits. Compare the results of this experiment with what you got in part (a)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


