Question: Task 4 : In IEEE 8 0 2 . 1 1 , open system authentication simply consists of two communications. An authentication is requested by
Task :
In IEEE open system authentication simply consists of two communications. An authentication is
requested by the client, which contains the station ID typically the MAC address This is followed by an
authentication response from the AProuter containing a success or failure message. An example of when
a failure may occur is if the client's MAC address is explicitly excluded in the AProuter configuration.
a What are the benefits of this authentication scheme?
b What are the security vulnerabilities of this authentication scheme?
Task :
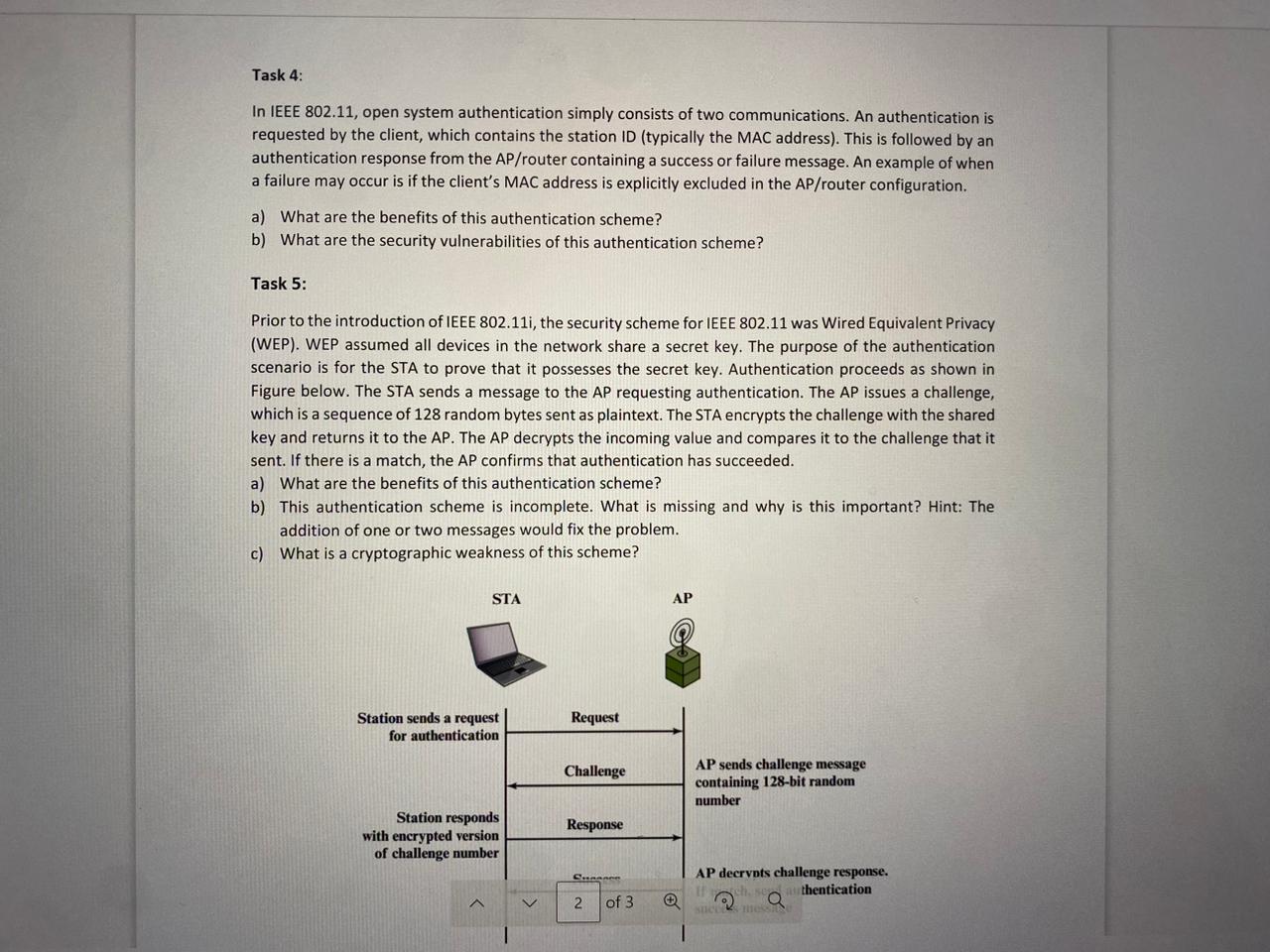
Prior to the introduction of IEEE the security scheme for IEEE was Wired Equivalent Privacy
WEP WEP assumed all devices in the network share a secret key. The purpose of the authentication
scenario is for the STA to prove that it possesses the secret key. Authentication proceeds as shown in
Figure below. The STA sends a message to the AP requesting authentication. The AP issues a challenge,
which is a sequence of random bytes sent as plaintext. The STA encrypts the challenge with the shared
key and returns it to the AP The AP decrypts the incoming value and compares it to the challenge that it
sent. If there is a match, the AP confirms that authentication has succeeded.
a What are the benefits of this authentication scheme?
b This authentication scheme is incomplete. What is missing and why is this important? Hint: The
addition of one or two messages would fix the problem.
c What is a cryptographic weakness of this scheme?
This has done hand written. Hand written answers onlyy
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


