Question: TASK: Do research on three potential wireless network attacks, analyze their effects, and provide brief descriptions of how to stop them in order to support
TASK:
Do research on three potential wireless network attacks, analyze their effects, and provide brief descriptions of how to stop them in order to support your choice of strategy. Comment on the wireless access point's proposed placement as well.
Consider the ethical and legal ramifications of implementing a Bring Your Own Device (BYOD) policy when gaining access to the business network.
I am thinking of including Rogue Access Point, MITM attacks and DoS attacks for the security threats. For the WAP location, I propose its placement within a well-secured server room.
This task requires me to write at least 1000 words, however, I do not know what else to write about the wireless attacks other than listing them and defining them. The same things goes with the WAP placement and BYOD policy. I need your help coming up with what else can I write about for this task.
What do you think should I include within this "research"? I know that there are plenty of research regarding these topics but they can get too advanced in comparison to what we are studying in uni.
CONTEXT:
You have been tasked with designing and putting into place a new enterprise network architecture based on conventional technologies and IPv4 addressing for the business while working as a network engineer for an IT company named ShibaInc.
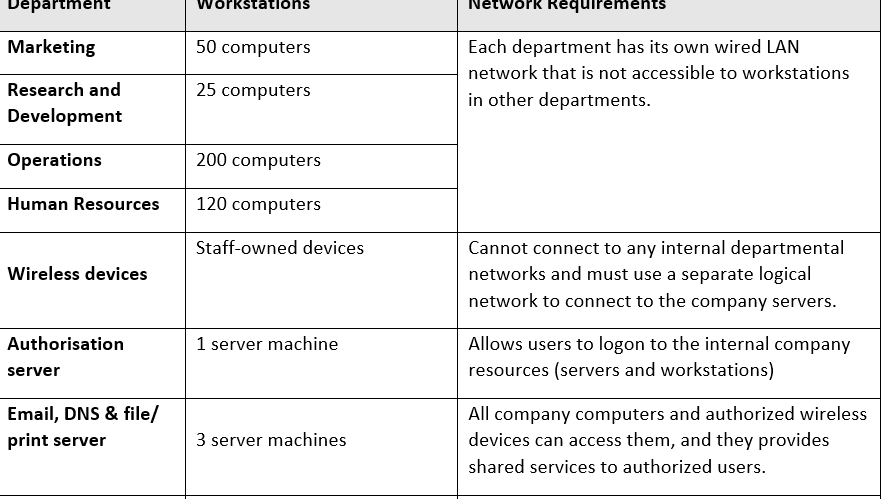
The company offers wired LAN connection and PC desktop workstations for office users and is made up of four departments: Marketing, Research and Development, Operations, and Human Resources.
The network needs five servers: a File/Print server, a Web server, an Email server, a DNS server, and an Authorization server. All office-based users must have access to all five servers. External users can only visit its external website.
The company allows employees to access the internet via wireless networks on their personal devices, such as iPhones and iPads. However, these devices should only be able to access servers and not be allowed to access departmental networks. The business also wants to test using IoT devices to monitor the server room.
The distribution of workstations is shown in Table 1, which describes the high-level network requirements for each department.

\begin{tabular}{|l|l|l|} \hline Web server & 1 server machine & Aserverthathostsanexternallyaccessiblewebsitethatisaccessibletoallusers. \\ \hline loT devices & loT devices & loTdevicesmustnowkeeptrackoftheserverroomstemperatureanddoor. \\ \hline \end{tabular}
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


