Question: The Access Data utility compares known file hash values to files on your evidence drive or image files to see whether they contain suspicious data.
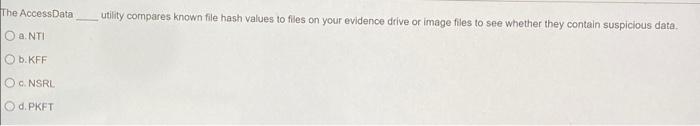

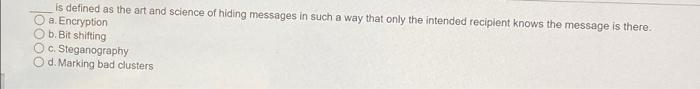


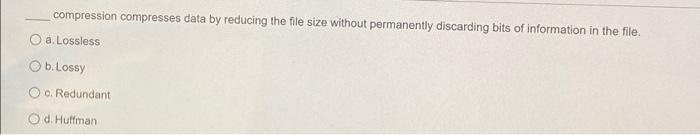


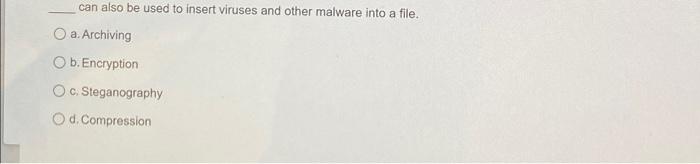
The Access Data utility compares known file hash values to files on your evidence drive or image files to see whether they contain suspicious data. O ANTI b.KFF NSRL d. PKFT The acronym "KFF" stands for O a. Keep First File b. Known Forensic File c. Known File Finder O d. Known File Filter is defined as the art and science of hiding messages in such a way that only the intended recipient knows the message is there. a. Encryption b. Bit shifting O c. Steganography Od. Marking bad clusters attacks use every possible letter, number, and character found on a keyboard when recovering a password. O a Statistics b. Dictionary c. Brute-force O d. Profile are based on mathematical instructions that define lines, curves, text, ovals, and other geometric shapes. a. Metafile graphics b. Vector graphics c. Bitmap images d. Line-art images compression compresses data by reducing the file size without permanently discarding bits of information in the file. O a. Lossless Ob.Lossy Oo. Redundant d. Huffman If you can't open an image file in an image viewer, the next step is to examine the file's a, extension b. size C.name d. header data In Forensic Toolkit (FTK), one could use the to examine a file's header information. a. Native Tab Ob. Hex Tab. C. PRTK O d. Registry Viewer can also be used to insert viruses and other malware into a file. a. Archiving O b.Encryption O c. Steganography O d. Compression steganography places data from a secret file into a host file by increasing the host file size. O a. Append b. Insertion O c. Substitution d. Replacement
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


