Question: The AES key schedule was designed to be efficient in environments with limited storage. For example, in a 128-bit key AES, once we compute W[4]
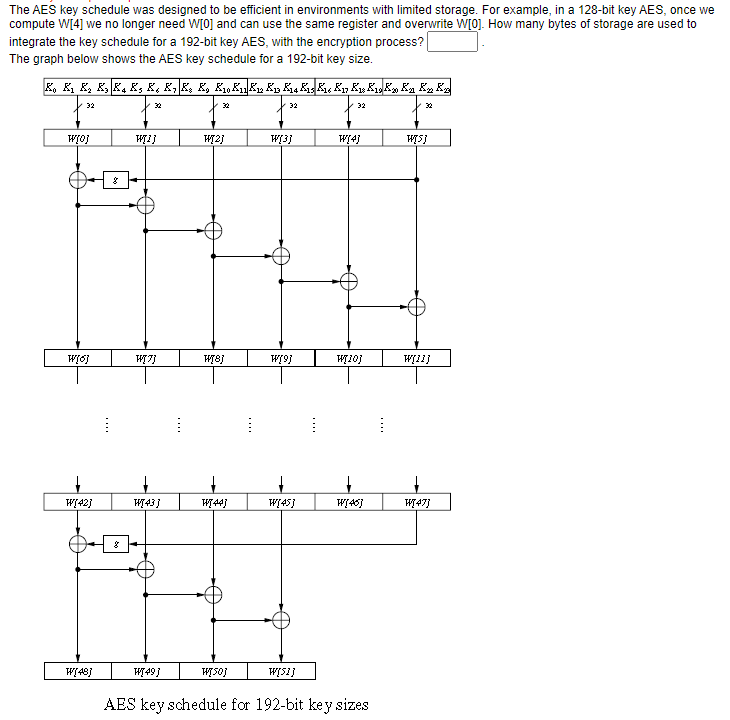 The AES key schedule was designed to be efficient in environments with limited storage. For example, in a 128-bit key AES, once we compute W[4] we no longer need W[0] and can use the same register and overwrite W[0]. How many bytes of storage are used to integrate the key schedule for a 192-bit key AES, with the encryption process?
The AES key schedule was designed to be efficient in environments with limited storage. For example, in a 128-bit key AES, once we compute W[4] we no longer need W[0] and can use the same register and overwrite W[0]. How many bytes of storage are used to integrate the key schedule for a 192-bit key AES, with the encryption process?
The AES key schedule was designed to be efficient in environments with limited storage. For example, in a 128-bit key AES, once we compute W[4] we no longer need W[0] and can use the same register and overwrite W[0]. How many bytes of storage are used to integrate the key schedule for a 192-bit key AES, with the encryption process? The graph below shows the AES key schedule for a 192-bit key size. AES key schedule for 192-bit key sizes
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


