Question: The answer should be based on system security context. Text &EraserRedactHighlightmege Signature Questions: [Q1] You Name a data item whose lifetime (amount of time for
The answer should be based on system security context.
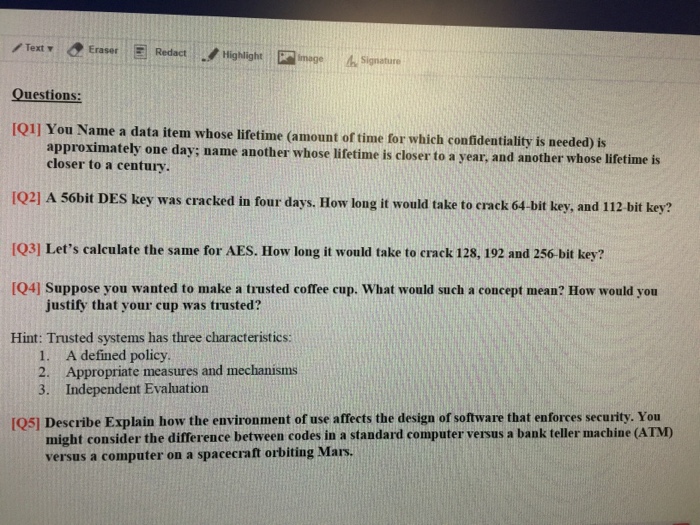
Text &EraserRedactHighlightmege Signature Questions: [Q1] You Name a data item whose lifetime (amount of time for which confidentiality is needed) is approximately one day; name another whose lifetime is closer to a year, and another whose lifetime is closer to a century IQ2] A 56bit DES key was cracked in four days. How long it would take to crack 64-bit key, and 112 bit key? 1Q3] Let's calculate the same for AES. How long it would take to crack 128, 192 and 256-bit key? Q4] Suppose you wanted to make a trusted coffee cup. What would such a concept mean? How would you justify that your cup was trusted? Hint: Trusted systems has three characteristics: 1. A defined policy 2. Appropriate measures and mechanisms 3. Independent Evaluation [Q5] Describe Explain how the environment of use affects the design of software that enforces security. You might consider the difference between codes in a standard computer versus a bank teller machine (ATM versus a computer on a spacecraft orbiting Mars
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


