Question: The assembly code is dumped from the function checkPass(). This function takes an input string password and checks whether it fits a predefined pattern. Determine
The assembly code is dumped from the function checkPass(). This function takes an input string "password" and checks whether it fits a predefined pattern. Determine what the predefined pattern was and show how you would bypass this checkPass().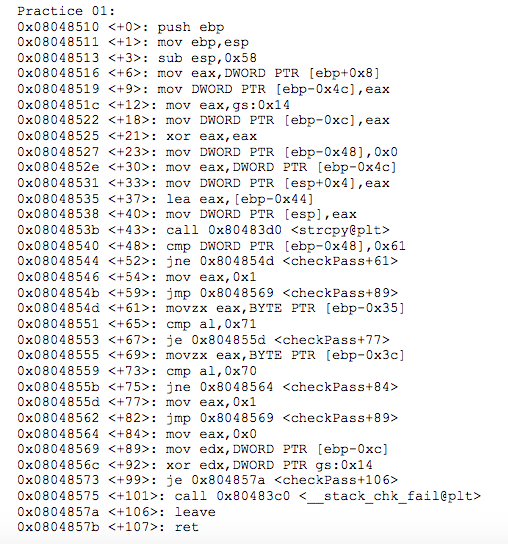
Practice 01: 0x08048510 : push ebp 0x08048511 : mov ebp, esp 0x08048513 : mov DWORD PTR [ebp-0x4c],eax 0x0804851c : mov eax,gs:0x14 0x08048522 xor eax, eax 0x08048527 : mov DWORD PTR [ebp-0x48),0x0 0x0804852e mov eax, DWORD PTR [ebp-0x4c] 0x08048531 : mov DWORD PTR [esp+0x4], eax 0x08048535 : lea eax, [ebp-0x44] 0x08048538 : mov DWORD PTR [esp], eax 0x0804853b : call 0x80483d0 0x08048540 : cmp DWORD PTR [ebp-0x48], 0x61 0x08048544 : jne 0x804854d 0x08048546 : m eax, 0x1 0x0804854b : jmp 0x8048569 0x0804854d : movzx eax, BYTE PTR [ebp-0x35] 0x08048551 : cmp al,0x71 0x08048553 : je 0x804855d 0x08048555 : movzx eax, BYTE PTR [ebp-0x3c] 0x08048559 : cmp al, 0x70 0x0804855b : jne 0x8048564 0x0804855d : mov eax, 0x1 0x08048562 jmp 0x8048569 0x08048564 : mov eax, 0x0 0x08048569 : mov eax, DWORD PTR [ebp-0xc] 0x0804856c : xor edx, DWORD PTR gs:0x14 0x08048573 : je 0x804857a 0x08048575 : call 0x80483c0 0x0804857a leave 0x0804857b : ret Practice 01: 0x08048510 : push ebp 0x08048511 : mov ebp, esp 0x08048513 : mov DWORD PTR [ebp-0x4c],eax 0x0804851c : mov eax,gs:0x14 0x08048522 xor eax, eax 0x08048527 : mov DWORD PTR [ebp-0x48),0x0 0x0804852e mov eax, DWORD PTR [ebp-0x4c] 0x08048531 : mov DWORD PTR [esp+0x4], eax 0x08048535 : lea eax, [ebp-0x44] 0x08048538 : mov DWORD PTR [esp], eax 0x0804853b : call 0x80483d0 0x08048540 : cmp DWORD PTR [ebp-0x48], 0x61 0x08048544 : jne 0x804854d 0x08048546 : m eax, 0x1 0x0804854b : jmp 0x8048569 0x0804854d : movzx eax, BYTE PTR [ebp-0x35] 0x08048551 : cmp al,0x71 0x08048553 : je 0x804855d 0x08048555 : movzx eax, BYTE PTR [ebp-0x3c] 0x08048559 : cmp al, 0x70 0x0804855b : jne 0x8048564 0x0804855d : mov eax, 0x1 0x08048562 jmp 0x8048569 0x08048564 : mov eax, 0x0 0x08048569 : mov eax, DWORD PTR [ebp-0xc] 0x0804856c : xor edx, DWORD PTR gs:0x14 0x08048573 : je 0x804857a 0x08048575 : call 0x80483c0 0x0804857a leave 0x0804857b : ret




