Question: The Caesar Cipher The Caesar ciphere is an ancient method of encrypting text, i.e. to transform text into a format that is unreadable for anyone
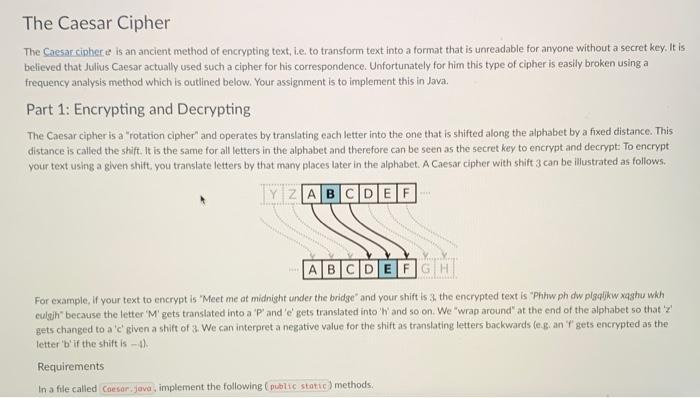
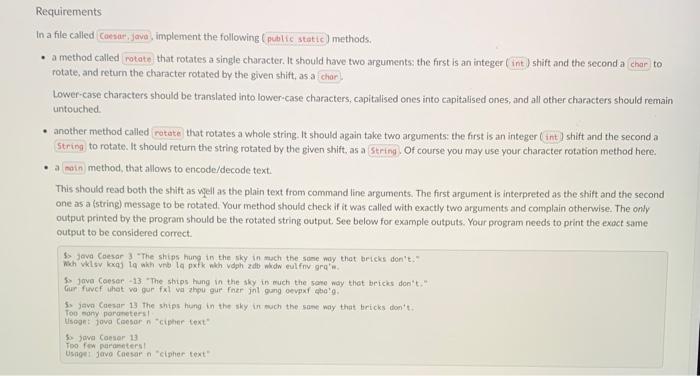
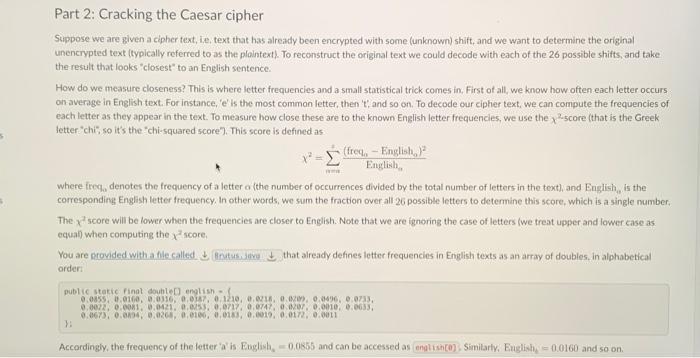
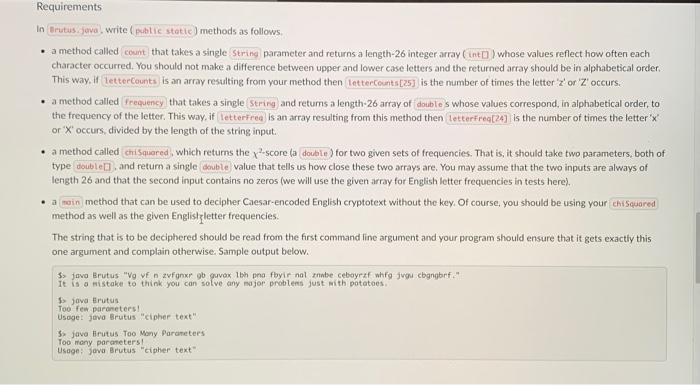
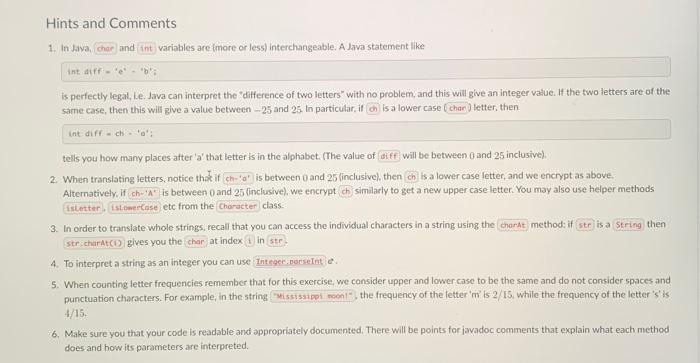
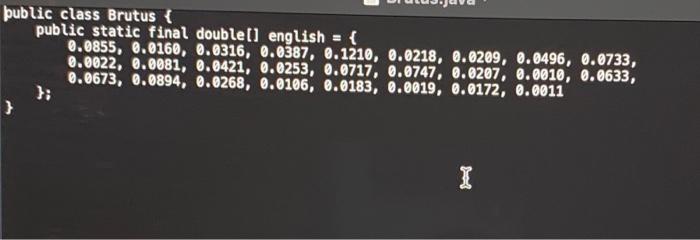
The Caesar Cipher The Caesar ciphere is an ancient method of encrypting text, i.e. to transform text into a format that is unreadable for anyone without a secret key. It is believed that Julius Caesar actually used such a cipher for his correspondence. Unfortunately for him this type of cipher is easily broken using a frequency analysis method which is outlined below. Your assignment is to implement this in Java. Part 1: Encrypting and Decrypting The Caesar cipher is a "rotation cipher" and operates by translating each letter into the one that is shifted along the alphabet by a fixed distance. This distance is called the shift. It is the same for all letters in the alphabet and therefore can be seen as the secret key to encrypt and decrypt: To encrypt your text using a given shift, you translate letters by that many places later in the alphabet. A Caesar cipher with shift 3 can be illustrated as follows. For example, if your text to encrypt is "Meet me at midnight under the bridge" and your shift is 3 , the encrypted text is "Phhw ph dw plsqlikw xaghu whh eulgin" becase the letter ' M ' gets translated into a ' P ' and ' e ' gets translated into ' h ' and so on. We "wrap around' at the end of the alphabet so that ' z ' gets changed to a 'c' given a shift of 3 . We can interpret a negative value for the shift as translating letters backwards (e. ga an 'f' gets encrypted as the letter ' b ' if the shitt is 4. Requirements In a file called implement the following ! methods. a method called implement the following methods. rotate, and return the character rotated by the given shift; as a Lower-case characters should be translated into lower-case characters, capitalised ones into capitalised ones; and all other characters should remain untouched. another method called that rotates a whole string. It should again take two arguments: the first is an integer [int ] shift and the second a to rotate. It should return the string rotated by the given shift, as a Of course you may use your character rotation method here. method, that allows to encode/decode text. This should read both the shift as well as the plain text from command line arguments. The first argument is interpreted as the shift and the second one as a fstring) message to be rotated. Your method should check if it was called with exactly two arguments and complain othenvise. The only output printed by the program should be the rotated string output. See below for example outputs. Your program needs to print the exact same output to be considered correct. 5. Java Coesar 3" The ships hurg in the sky in mach the sime may that bricks don't:" 5. java Coeser -13. "The ships hung in the sky in wuch the sane nay thet beicks don"t." fur funcf what wo gur fat va ehpu gur finer inl gang oevpxe pho'g. 5. jeva Caesar 13 the ships hung in the sky in auch the same way that bricks dontt. Too nony poraneters! Hisege: jowa caosor n "cipher text" 5. java Coesor 13 Too fon paramerst Usaget javo Caesar-n "cipher text" Part 2: Cracking the Caesar cipher Suppose we are given a cipher text, ie, text that has already been encrypted with some (unknown) shift, and we want to determine the original unencrypted text (typically referred to as the plointext). To reconstruct the original text we could decode with each of the 26 possible shifts, and take the result that looks "closest" to an English sentence. How do we measure closeness? This is where letter frequencies and a small statistical trick comes in. First of all, we know how often each letter occurs on average in English text. For instance, ' e ' is the most comman letter, then ' t ', and so on. To decode cur cipher text, we can compute the frequencies of each letter as they appear in the text. To measure how close these are to the known English letter frequencles, we use the x2.5core (that is the Greek letter "chis, so it's the "chi-squared score?". This score is defined as. x2=k=1Englishp0(freq0English0)2 where irequ denotes the frequency of a letter a (the number of occurrences divided by the total number of letters in the text), and English, is the corresponding English letter frequency. In other words, we sum the fraction over all 26 possible letters to deternine this score, which is a single number. The x2 score will be lower when the frequencies are closer to English. Note that we are fignoring the case of letters fwe treat upper and lower case as equal) when computing the x2 score. You are nrovided with a file called that already defines letter frequencies in English texts as an array of doubles, in alphabetical orden public stakic finol doubleD english = H. Accordingly, the frequency of the letter 'a' is English 2=0.0855 and can be accessed as . Similarly, English hj=0.0160 and so on. - a method called that takes a single parameter and returns a length-26 integer array i whose values reflect how often each character occurred, You should not make a difference between upper and lower case letters and the returned array should be in alphabetical order. This way, if is an array resulting from your method then is the number of times the letter ' z ' or ' Z ' occurs. - a method called that takes a single and returns a length-26 array of is whose values correspond, in alphabetical order, to the frequency of the letter. This way, if is an array resulting from this method then is the number of times the letter ' x ' or ' X ' occurs, divided by the length of the string input. - a method called which retums the x2 score la for two given sets of frequencies. That is, it should take two parameters, both of type and retum a single value that tells us how close these two arrays are. You may assume that the two inputs are always of length 26 and that the second input contains no zeros (we will use the given array for English letter frequencies in tests here). a method that can be used to decipher Caesar-encoded English cryptotext without the key, Of course, you should be using your method as well as the given Englisk zletter frequencies. The string that is to be deciphered should be read from the first command line argument and your program should ensure that it gets exactiy this one argument and complain otherwise. Sample output below. It is a mistake to think you can solve any nojor problems just mith potatoes. 5. jova Erutus Too fen paroneters! Usoge: jeva Brutus "cipher text" 3. javo Brutus Too Mony Paraneters Too meny paraneters! Usage: jova Brutus "eipher text" 1. In lava, and variables are (more or less) interchangeable. A dava statement like Int atff = 'e" - "bt: is perfectly legal, te. Java can interpret the "difference of two letters" with no problem, and this will give an integer value. If the two letters are of the same case, then this will give a value between 25 and 25 in particular, if is a lower case letter, then. Intdiff=ch=a7; tells you how many places after 'a' that letter is in the alphabet. The value of will be between 0 and 25 inclusive). 2. When transiating letters, notice thot if is between 0 and 25 (inclusive), then is a lower case letter, and we encrypt as above. Alternatively. if is between 0 and 25 (inclusive), we encrypt ch similarly to get a new upper case letter. You may also use helper methods etc from the class. 3. In order to translate whole strings, recall that you can access the individual characters in a string using the gives you the at index in 4. To interpret a string as an integer you can use 5. When counting letter frequencies remember that for this exercise, we consider upper and lower case to be the same and do not consider spaces and punctuation characters. For example, in the string the frequency of the letter ' 1 ' is 2/15. while the frequency of the letter 's' is: 4. 15 . 6. Make sure you that your code is readable and appropriately documented. There will be points tor javadoc comments that explain what each method does and how its parameters are interpreted. public class Brutus \{ public static final double[ ] english ={ 0.0855,0.0160,0.0316,0.0387,0.1210,0.0218,0.0209,0.0496,0.0733,0.0022,0.0081,0.0421,0.0253,0.0717,0.0747,0.0207,0.0010,0.0633,0.0673,0.0894,0.0268,0.0106,0.0183,0.0019,0.0172,0.0011
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


