Question: The following figure illustrates a protocol that allows to authenticate a public key. The exchanges are made over http . Can you analyse the protocol
The following figure illustrates a protocol that allows to authenticate a public key.
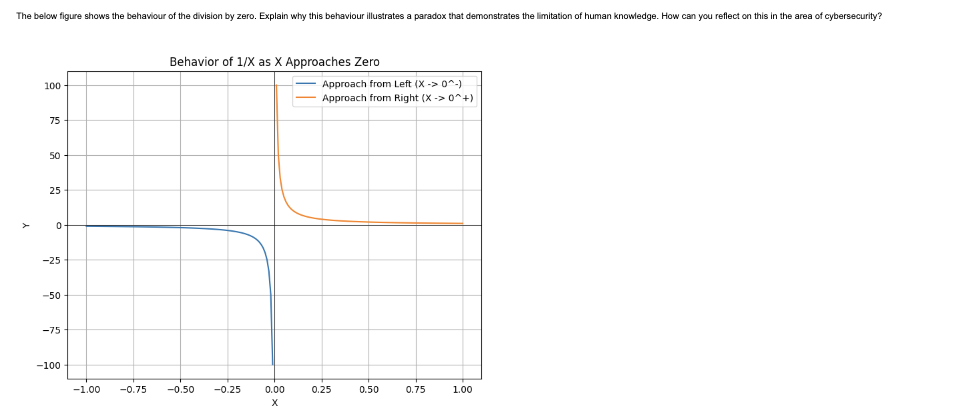
The exchanges are made over http Can you analyse the protocol to see whether it is vulnerable to man in the middle attack?Behavior of as Approaches Zero
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


