Question: The instructions are in the first image IS486 - Managing Cyber Security Operations Case Study Lab Assignment #4 Due Date: The exact due date for
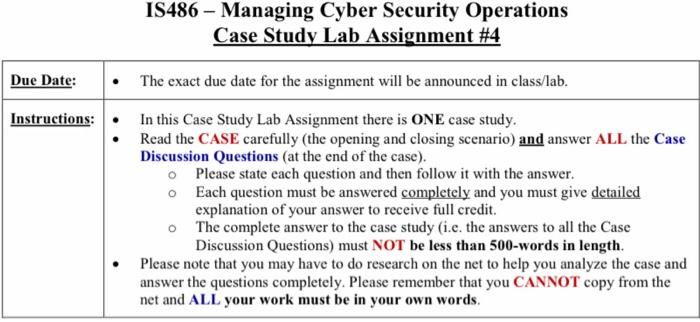

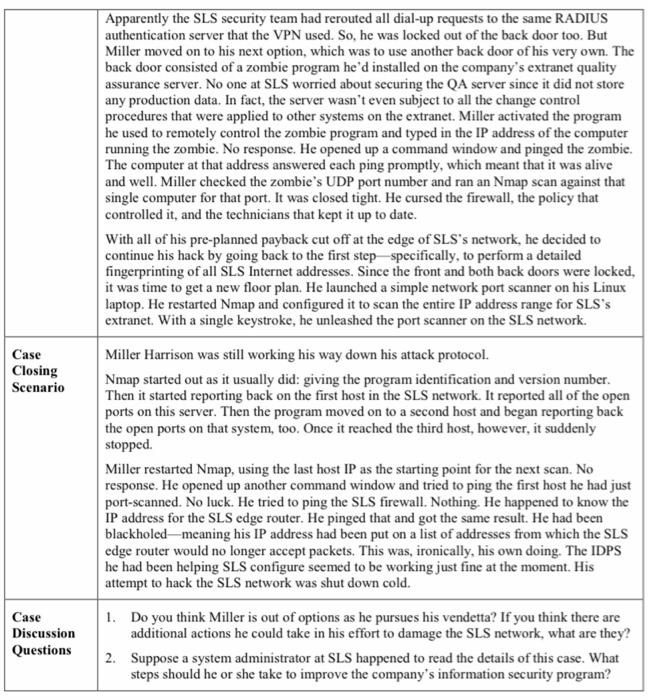
IS486 - Managing Cyber Security Operations Case Study Lab Assignment #4 Due Date: The exact due date for the assignment will be announced in class/lab. Instructions: In this Case Study Lab Assignment there is ONE case study. Read the CASE carefully (the opening and closing scenario) and answer ALL the Case Discussion Questions at the end of the case). o Please state each question and then follow it with the answer. Each question must be answered completely and you must give detailed explanation of your answer to receive full credit. The complete answer to the case study (i.e. the answers to all the Case Discussion Questions) must NOT be less than 500-words in length. Please note that you may have to do research on the net to help you analyze the case and answer the questions completely. Please remember that you CANNOT copy from the net and ALL your work must be in your own words. O Case Opening Scenario Security Technology Miller Harrison was going to make them sorry and make them pay. Earlier today, his contract with SLS had been terminated, and he'd been sent home. Oh sure, the big shot manager, Charlie Moody, had said Miller would still get paid for the two weeks remaining in his contract, and that the decision was based on changes in the project and evolving needs as project work continued," but Miller knew better. He knew he'd been let go because of that know-nothing Kelvin and his simpering lapdog Laverne Nguyen. And now he was going to show them and everyone else at SLS who knew more about security. Miller knew that the secret to hacking into a network successfully was to apply the same patience, attention to detail, and dogged determination that defending a network required. He also knew that the first step in a typical hacking protocol was footprinting-that is, getting a fully annotated diagram of the network. Miller already had one of these--in a violation of company policy, he had brought a copy home last week when Laverne first started trying to tell him how to do his job. When they terminated his contract today, Miller's supervisors made him turn in his company laptop and then actually had the nerve to search his briefcase. By then, however, Miller had already stashed all the files and access codes he needed to wage an attack. To begin, he activated his VPN client to connect to the SLS network from his rented connection at an Internet cafe. He realized almost immediately that Charlie Moody had also confiscated the crypto-token that enabled him to use the VPN for remote access. No problem, Miller thought. If the front door was locked, he would try the back door. He cabled his laptop to the analog phone line, opened up a modem dialing program and typed in the dialup number for SLS he had gotten from the network administrator last week. After the dialer established the connection, Miller positioned his hands on the keyboard, and then he read the prompt on his monitor: SLS Inc. Company Use Only. Unauthorized use is prohibited and subject to prosecution. Enter Passphrase: Case Closing Scenario Apparently the SLS security team had rerouted all dial-up requests to the same RADIUS authentication server that the VPN used. So, he was locked out of the back door too. But Miller moved on to his next option, which was to use another back door of his very own. The back door consisted of a zombie program he'd installed on the company's extranet quality assurance server. No one at SLS worried about securing the QA server since it did not store any production data. In fact, the server wasn't even subject to all the change control procedures that were applied to other systems on the extranet. Miller activated the program he used to remotely control the zombie program and typed in the IP address of the computer running the zombie. No response. He opened up a command window and pinged the zombie. The computer at that address answered each ping promptly, which meant that it was alive and well. Miller checked the zombie's UDP port number and ran an Nmap scan against that single computer for that port. It was closed tight. He cursed the firewall, the policy that controlled it, and the technicians that kept it up to date. With all of his pre-planned payback cut off at the edge of SLS's network, he decided to continue his hack by going back to the first step specifically, to perform a detailed fingerprinting of all SLS Internet addresses. Since the front and both back doors were locked, it was time to get a new floor plan. He launched a simple network port scanner on his Linux laptop. He restarted Nmap and configured it to scan the entire IP address range for SLS's extranet. With a single keystroke, he unleashed the port scanner on the SLS network. Miller Harrison was still working his way down his attack protocol. Nmap started out as it usually did: giving the program identification and version number. Then it started reporting back on the first host in the SLS network. It reported all of the open ports on this server. Then the program moved on to a second host and began reporting back the open ports on that system, too. Once it reached the third host, however, it suddenly stopped. Miller restarted Nmap, using the last host IP as the starting point for the next scan. No response. He opened up another command window and tried to ping the first host he had just port-scanned. No luck. He tried to ping the SLS firewall. Nothing. He happened to know the IP address for the SLS edge router. He pinged that and got the same result. He had been blackholed-meaning his IP address had been put on a list of addresses from which the SLS edge router would no longer accept packets. This was, ironically, his own doing. The IDPS he had been helping SLS configure seemed to be working just fine at the moment. His attempt to hack the SLS network was shut down cold. 1. Do you think Miller is out of options as he pursues his vendetta? If you think there are additional actions he could take in his effort to damage the SLS network, what are they? 2. Suppose a system administrator at SLS happened to read the details of this case. What steps should he or she take to improve the company's information security program? Case Discussion Questions
Step by Step Solution
There are 3 Steps involved in it
1 Do you think Miller is out of options as he pursues his vendetta If you think there are additional actions he could take in his effort to damage the SLS network what are they Miller has exhausted se... View full answer

Get step-by-step solutions from verified subject matter experts


