Question: The protocol is used between a cellphone and a cell tower for the purpose of authentication. 1) Gossip 2) Link state 3) Challenge-response 4) Neighbor
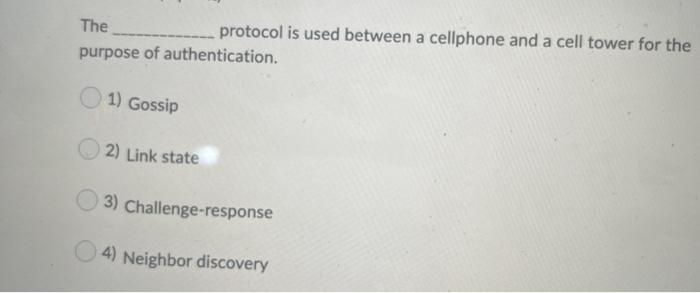

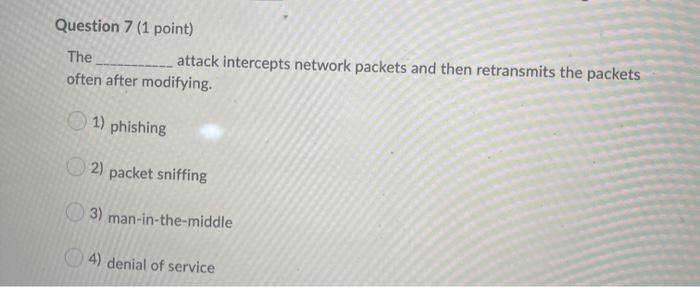
The protocol is used between a cellphone and a cell tower for the purpose of authentication. 1) Gossip 2) Link state 3) Challenge-response 4) Neighbor discovery Question 6 (1 point) Which of the following statements is NOT true? 1) 2) Biometric in security refers to any measure used to uniquely identify a person based on biological or physiological traits. Smart cards has an IC and provides a higher degree of protection than magnetic stripe cards. 3) Passive RFID chips do not require a battery embedded. 4) With the advances of technologies, the protection of digital information does not need to include methods for physically protecting the digital interfaces. Question 7 (1 point) The attack intercepts network packets and then retransmits the packets often after modifying. 1) phishing 2) packet sniffing 3) man-in-the-middle 4) denial of service
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


