Question: The Python programming language provides the programmer with a variety of string manipulation methods (functions). For this assignment, you'll implement two of those functions as
The Python programming language provides the programmer with a variety of string manipulation methods (functions). For this assignment, you'll implement two of those functions as CUSP subroutines.The first of these Python methods is swapcase(). This function expects a string as an argument and returns a copy of the original string but with a lower case letters converted to upper case, and all upper case letters converted tolower case. Characters that are not letters remain unchanged. Here is an example of the function in action:>>> test = "lEArN pYtHOn iN 30 YeaRS!">>> result = test.swapcase()>>> print(result)LeaRn PyThoN In 30 yEArs!The task for you is to write a subroutine in CUSP that does what swapcase()does.Your subroutine should expect the following parameters to be pushed on the stack by the calling procedure in this order:The starting address of the original string will be pushed first on the stackThe number of characters in that string will be pushed nextThe starting address of the converted string will be pushed lastName your subroutine swapcase. Your subroutine should create a new string as described aboveand place the new string in memory starting at the address given in the last parameter pushed on the stack. Note that the original string should not be altered in any way by your subroutine.
The function must be implemented below.
Accumulator, Index Register, Frame Pointer, Stack Pointer are the registers
Using following machine code language attached please:
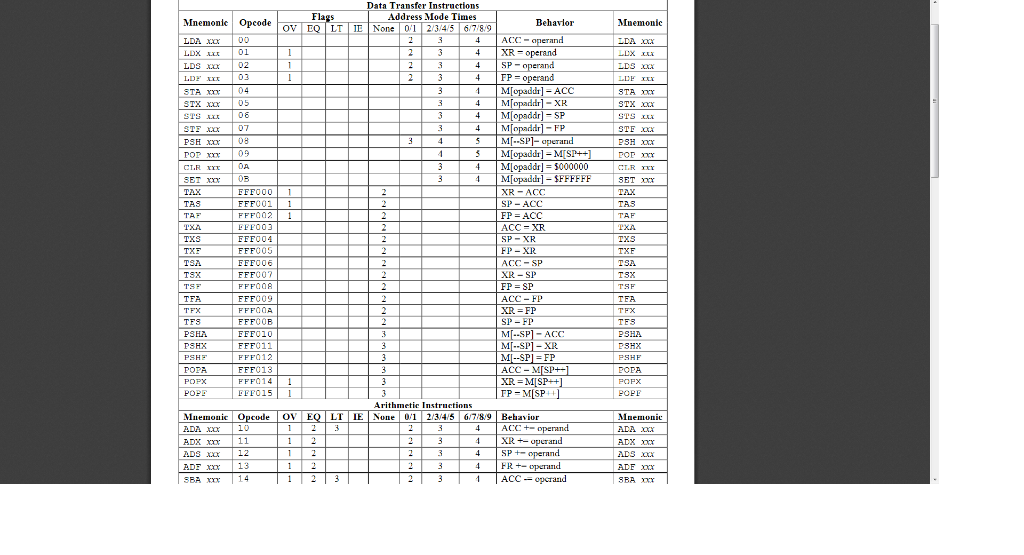
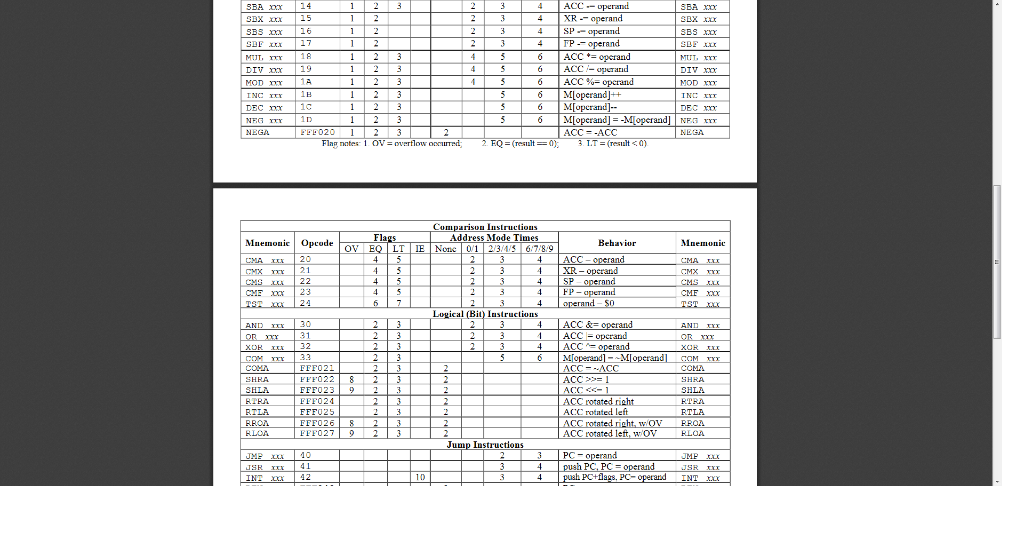
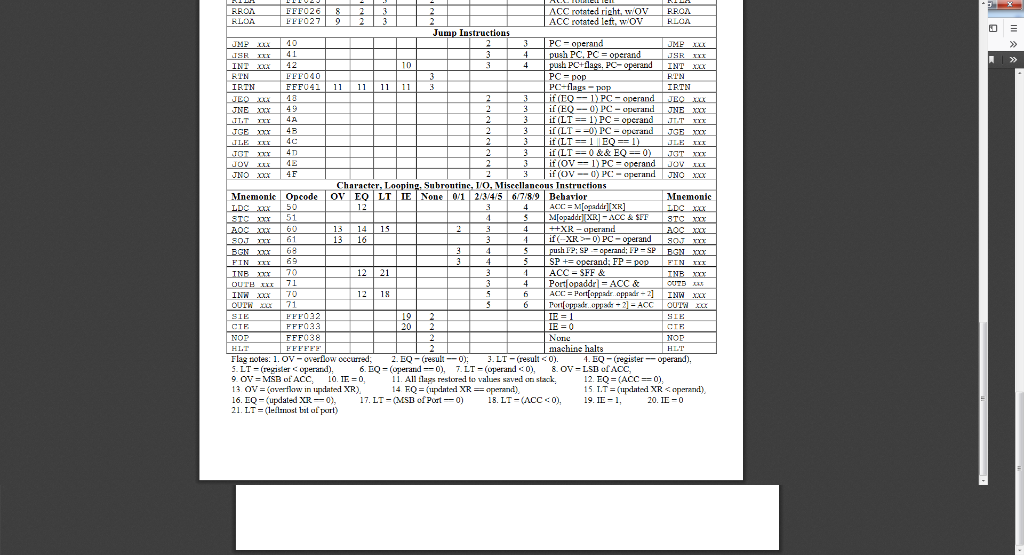
Data Transfer Instructions Address Mode Times Mnemonle Opcode ov 3 Behavlor Muemonic 45 67/89 ACC 1Mopaddr]-ACC 4Mlopaddr] 5000000 | MIopadd]-$FFFFFF 4 EFF000 FFFO FFF002 EFFOO FFF007 FFFOO9 FFFOOEB ML-SP]- ACC FFF01 FFF12 FFF013 FFF0141 EFFO15 MI--SPI FP Arithmetic Instructions OV EO LTIE None 1 2/3/4/5 6.789 Behavior Mmemoni XR+operand ACC-operand 3BA x 14 DX xxx 15 ox 16 3BS xo NIIT TY 6 ACCpad MOD mx 6 Moperand]- 020 1 2 3 ACC -ACC NECA Flan nates 1 Ov:ovrflow (result 0) omparison Instructions ddress Mode Times Fla Mnenonic Opcode Behavior 7.8.9 20 21 34 FP-aperand ical (Bit) Instruclions 30 32 MToperand] and! CCM ACC COMA FFHO22 8 23 FFF023 ACC1 HLA ACC- ACC rotated left ACC rotated left, wOV HLA RILA FFFO25 RTLA RLOR Jump Instructions 12 PC flags, PC | ACC eft, wov Jump Iustructions 10 PC-o UME INI IRIN 12 FFO4 PC PC PC pop PCflags- 11 13 IRTN 49 4A. 4B 4C 4D i (EQ-0) PC-aperarnd frov1PCoperand 3-1 if (OV--PC-operand AF | Character, La Subrontine, IO, Miscellancous Trn Mnemonic | Opcode | Oy EQ | LT E | None l 0/1 2/3/4:5 | 6.,7.8.9 | Behavior Mnemonic ACC = M 51 if(-XR-0) PC P- SP SP cperand: FP- ACC PortlopaddrA FF & INx 70 12 18 6 ACC = Port[appadr appar FFF032 FFF038 Flag notes: 1.ov-overflow occured 2.EQ-(resul0 3LT-(resul)4. EQ-(register-operand). 5.LT-(register ': operand), 6. EQ_(uperand-0), 7. LT-(operand ": , 8. OV-LSD ofACic. 9OV = MSB ofACC, 10.=0, 11.All flags restored to values saved an stack. 12.EQ=(ACC =:0): 13 OV = (overflow in updated XR). 16.EQ-(updated XR-0), 17. LT-QLSD ofPurl0) 18.LT-(ACC-: 0), 19.11-1, 20.11-0 21 LTelmst bal of purt) 14 EQ-(updnted X-operand) 1 5 T.T = (updnted XR operand) Data Transfer Instructions Address Mode Times Mnemonle Opcode ov 3 Behavlor Muemonic 45 67/89 ACC 1Mopaddr]-ACC 4Mlopaddr] 5000000 | MIopadd]-$FFFFFF 4 EFF000 FFFO FFF002 EFFOO FFF007 FFFOO9 FFFOOEB ML-SP]- ACC FFF01 FFF12 FFF013 FFF0141 EFFO15 MI--SPI FP Arithmetic Instructions OV EO LTIE None 1 2/3/4/5 6.789 Behavior Mmemoni XR+operand ACC-operand 3BA x 14 DX xxx 15 ox 16 3BS xo NIIT TY 6 ACCpad MOD mx 6 Moperand]- 020 1 2 3 ACC -ACC NECA Flan nates 1 Ov:ovrflow (result 0) omparison Instructions ddress Mode Times Fla Mnenonic Opcode Behavior 7.8.9 20 21 34 FP-aperand ical (Bit) Instruclions 30 32 MToperand] and! CCM ACC COMA FFHO22 8 23 FFF023 ACC1 HLA ACC- ACC rotated left ACC rotated left, wOV HLA RILA FFFO25 RTLA RLOR Jump Instructions 12 PC flags, PC | ACC eft, wov Jump Iustructions 10 PC-o UME INI IRIN 12 FFO4 PC PC PC pop PCflags- 11 13 IRTN 49 4A. 4B 4C 4D i (EQ-0) PC-aperarnd frov1PCoperand 3-1 if (OV--PC-operand AF | Character, La Subrontine, IO, Miscellancous Trn Mnemonic | Opcode | Oy EQ | LT E | None l 0/1 2/3/4:5 | 6.,7.8.9 | Behavior Mnemonic ACC = M 51 if(-XR-0) PC P- SP SP cperand: FP- ACC PortlopaddrA FF & INx 70 12 18 6 ACC = Port[appadr appar FFF032 FFF038 Flag notes: 1.ov-overflow occured 2.EQ-(resul0 3LT-(resul)4. EQ-(register-operand). 5.LT-(register ': operand), 6. EQ_(uperand-0), 7. LT-(operand ": , 8. OV-LSD ofACic. 9OV = MSB ofACC, 10.=0, 11.All flags restored to values saved an stack. 12.EQ=(ACC =:0): 13 OV = (overflow in updated XR). 16.EQ-(updated XR-0), 17. LT-QLSD ofPurl0) 18.LT-(ACC-: 0), 19.11-1, 20.11-0 21 LTelmst bal of purt) 14 EQ-(updnted X-operand) 1 5 T.T = (updnted XR operand)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


