Question: The solution needs to be a tree diagram similar to the image attached below. Please help me out with this. Task 2 - Attack Trees

The solution needs to be a tree diagram similar to the image attached below. Please help me out with this.
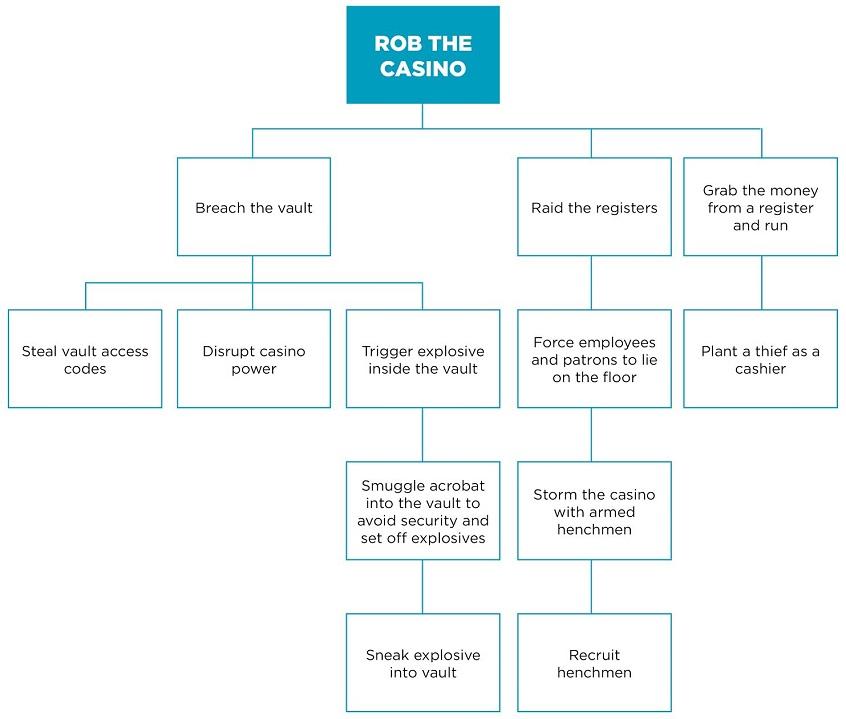
Task 2 - Attack Trees Generate an attack tree to compromise one of your friend's laptop. You should consider all means of attack including, but not necessarily limited to social engineering, physical access/theft, remote login, malware etc. Your goal is to access and delete a particular file on your friend's laptop and nothing more
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


