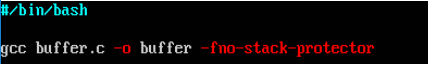Question: There is a function called 'hackme' in the C source code, which will print a message with your CWID if it is called with correct
There is a function called 'hackme' in the C source code, which will print a message with your CWID if it is called with correct parameters. However, this function is not called anywhere in the program. So, how could you call it with your CWID without modifying the program?
Read the C source code again to locate the stack overflow vulnerability. Here comes your task to perform the attack exploiting the vulnerability: modify the input file 'data.txt' so that when you run the program with it again, 'hackme' is called with your CWID.
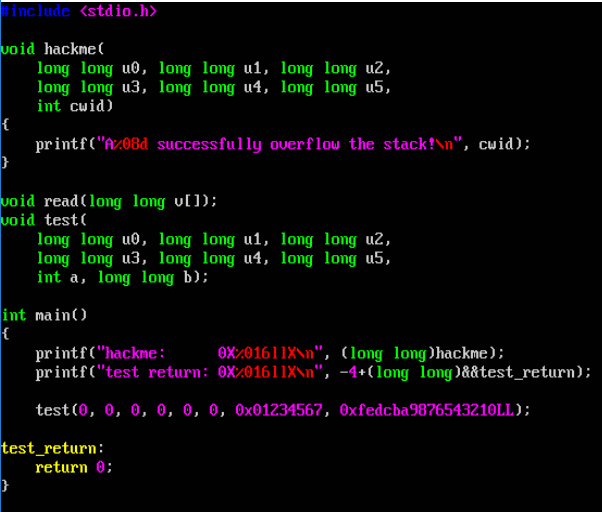
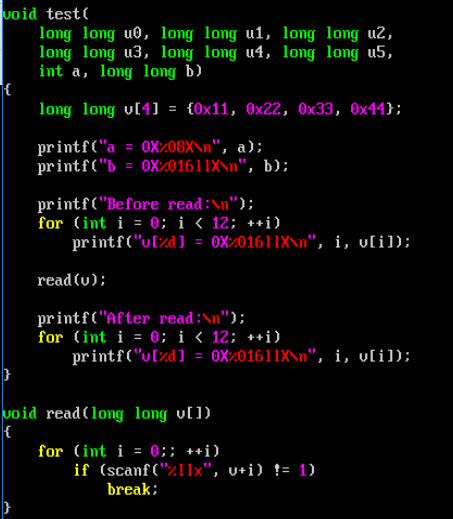
the given code for buffer.c is
given code for build.sh is
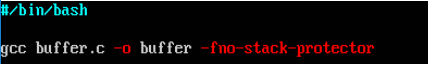
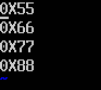
given code for data.txt is
the output i get when I run ./buffer
at the moment is
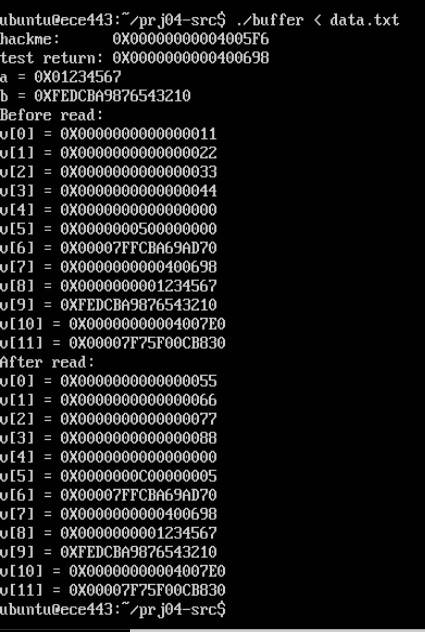
what do I have to do so it prints out
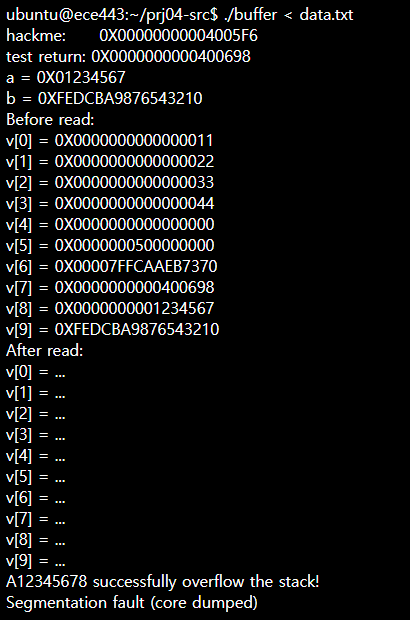
and questions are
Explain the structure of the stack frames using the program output as an example. Why do we use the type 'long long' extensively in the program?
What is the stack overflow vulnerability in the C program? How would you modify the C source code to correct it?
Explain your attack, i.e. explain why you modify the input file in such a way.
(20% bonus) What is the purpose of the parameters 'u0' to 'u5' for both 'test' and 'hackme'?
include uoid hackme( long long u0, long long ul, long long u2, long long u3, long long u4, long long u5, int cwid) printf("A 08d successfully ouerflou the stackn", cwid) oid readlong long vlI) uoid test long long u0, long long ul, long long u2, long long u3, long long u4, long long u5 int a, long long b) int main printf("hackne: printf("test return: 0X/ 01611X ", (long OXz016 11X>n", long)hackme): 4+(long long)&&test-return); test(0, 0, 0, 0, 0, 0, 0x01234567, 0xfedcba9876543210LL): test_return return 0 uoid test long long u0 long long u1, long long u2, long long u3, long long u, long long u5, int a, long ng b) long long u[4] {0x11, 0x22, 0x33, 0x44}; printf "a-0X/08XNn", a) printf("b = OX:01611X>n'', b); printf"Before read:Nn"): for (int i = 0; i 12: ++i) printf "vudx/01611Xn", i, ulil); read (u): printf("After read: ") for (int i -0; 12: ++1) printf("uzd0X 01611Xn", i, ulil): uoid read(long long ull) for (int i 0:: +i) if (scanfC"11x", u-i) t- 1) break: 1/bin/bash gcc buffer.c -o buffer -fno-stack-protector 5678 5678 0-0 00 ubuntueece443: "/pr j04-src$ ./buffer uoid hackme( long long u0, long long ul, long long u2, long long u3, long long u4, long long u5, int cwid) printf("A 08d successfully ouerflou the stackn", cwid) oid readlong long vlI) uoid test long long u0, long long ul, long long u2, long long u3, long long u4, long long u5 int a, long long b) int main printf("hackne: printf("test return: 0X/ 01611X ", (long OXz016 11X>n", long)hackme): 4+(long long)&&test-return); test(0, 0, 0, 0, 0, 0, 0x01234567, 0xfedcba9876543210LL): test_return return 0 uoid test long long u0 long long u1, long long u2, long long u3, long long u, long long u5, int a, long ng b) long long u[4] {0x11, 0x22, 0x33, 0x44}; printf "a-0X/08XNn", a) printf("b = OX:01611X>n'', b); printf"Before read:Nn"): for (int i = 0; i 12: ++i) printf "vudx/01611Xn", i, ulil); read (u): printf("After read: ") for (int i -0; 12: ++1) printf("uzd0X 01611Xn", i, ulil): uoid read(long long ull) for (int i 0:: +i) if (scanfC"11x", u-i) t- 1) break: 1/bin/bash gcc buffer.c -o buffer -fno-stack-protector 5678 5678 0-0 00 ubuntueece443: "/pr j04-src$ ./buffer