Question: This is a cryptology question from the textbook Introduction to Modern Cryptography by Katz and Lindell. 5.6 For each of the following modifications to the
This is a cryptology question from the textbook Introduction to Modern Cryptography by Katz and Lindell.
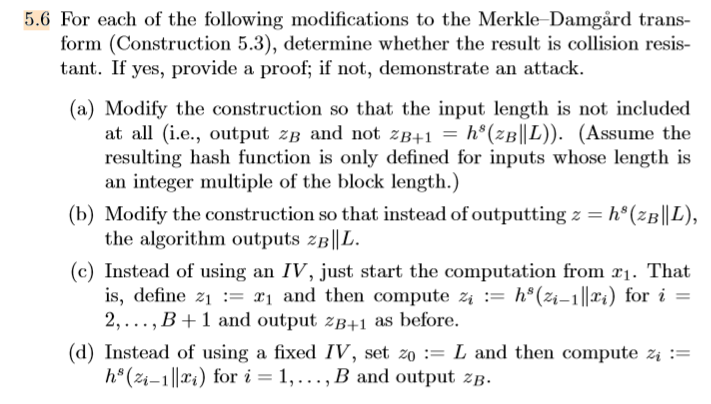
5.6 For each of the following modifications to the Merkle-Damgrd trans- form (Construction 5.3), determine whether the result is collision resis- tant. If yes, provide a proof; if not, demonstrate an attack (a) Modify the construction so that the input length is not included at all (i.e., output zB and not zB+1 = h"(zBI1L)). (Assume the resulting hash function is only defined for inputs whose length is an integer multiple of the block length.) (b) Modify the construction so that instead of outputting z - h8(2B L) the algorithm outputs 2B|L (c) Instead of using an IV, just start the computation from xi. That is, define zi := ri and then compute zi := hs(4-1 llri) for i 2,.., B+1 and output zB+1 as before. (d) Instead of using a fixed IV, set zo L and then compute h (-1) for i-1,..., B and output zB. 5.6 For each of the following modifications to the Merkle-Damgrd trans- form (Construction 5.3), determine whether the result is collision resis- tant. If yes, provide a proof; if not, demonstrate an attack (a) Modify the construction so that the input length is not included at all (i.e., output zB and not zB+1 = h"(zBI1L)). (Assume the resulting hash function is only defined for inputs whose length is an integer multiple of the block length.) (b) Modify the construction so that instead of outputting z - h8(2B L) the algorithm outputs 2B|L (c) Instead of using an IV, just start the computation from xi. That is, define zi := ri and then compute zi := hs(4-1 llri) for i 2,.., B+1 and output zB+1 as before. (d) Instead of using a fixed IV, set zo L and then compute h (-1) for i-1,..., B and output zB
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


