Question: This is Dillie Hellman/Elgamal cryptosystem question, please advise 2. *Consider the following protocol. Alice and Bob choose a common prime p. Alice picks a random
This is Dillie Hellman/Elgamal cryptosystem question, please advise 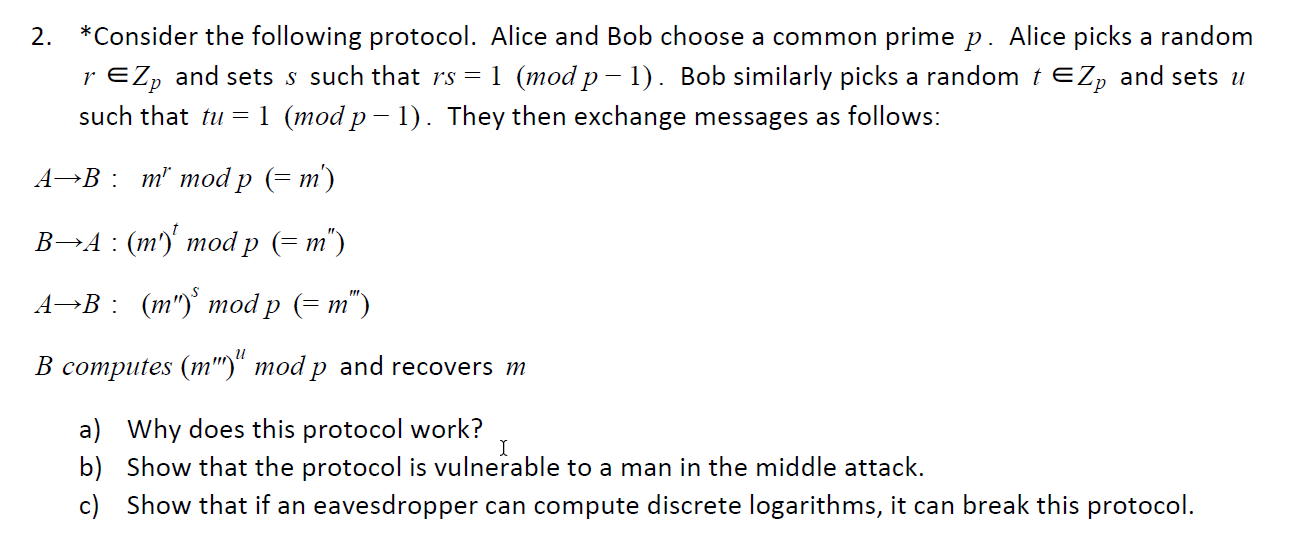
2. *Consider the following protocol. Alice and Bob choose a common prime p. Alice picks a random r EZp and sets s such that rs = 1 (mod p - 1). Bob similarly picks a random t EZp and sets u such that tu = 1 (mod p - 1). They then exchange messages as follows: A-B: m mod p = m') B~A: (m) mod p (= m") A-B: (m)* mod p (= m") B computes (m'') mod p and recovers m a) Why does this protocol work? b) Show that the protocol is vulnerable to a man in the middle attack. c) Show that if an eavesdropper can compute discrete logarithms, it can break this protocol
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


